Introduction
Hey there, Welcome back. In this post, let’s see how to use netcat for privilege escalation and how it work below is the video format of the post. Do check it out 👇🏾
Video
What is Netcat (nc)
Netcat, also known as “nc”, is a command-line tool used for network communication. It is designed to read and write data across network connections using TCP or UDP protocols.
Netcat is a versatile tool that can be used for various purposes, such as:
- Port scanning: Netcat can be used to scan for open ports on a remote system.
- File transfer: Netcat can be used to transfer files between two systems over a network connection.
- Remote administration: Netcat can be used to execute commands on a remote system, allowing for remote administration.
- Chatting: Netcat can be used for chatting between two systems on a network.
Netcat can also be used to create a simple network server or client, making it a valuable tool for network troubleshooting and testing. However, it should be used with caution, as it can also be used for malicious purposes such as hacking or data theft.
Who developed netcat
It seems the tool is developed by an org by Stearns and we can also see the package tracker from salsa Debian.
Netcat commands
- -c: shell commands as `-e’; use /bin/sh to exec [dangerous!!]
- -e: filename program to exec after connect [dangerous!!]
- -b: allow broadcasts
- -g: gateway source-routing hop point[s], up to 8
- -G: num source-routing pointer: 4, 8, 12, …
- -h: this cruft
- -i: secs delay interval for lines sent, ports scanned
- -k: set keepalive option on socket
- -l: listen mode, for inbound connects
- -n: numeric-only IP addresses, no DNS
- -p: port local port number
- -r: randomize local and remote ports
- -q: secs quit after EOF on stdin and delay of secs
- -s: addr local source address
- -T: tos set Type Of Service
- -t: answer TELNET negotiation
- -u: UDP mode
- -v: verbose [use twice to be more verbose]
- -w: secs timeout for connects and final net reads
- -C: Send CRLF as line-ending
- -z: zero-I/O mode [used for scanning]
How to use netcat
To use Netcat for privilege escalation you can just mention nc and you can specify the command you want from above.
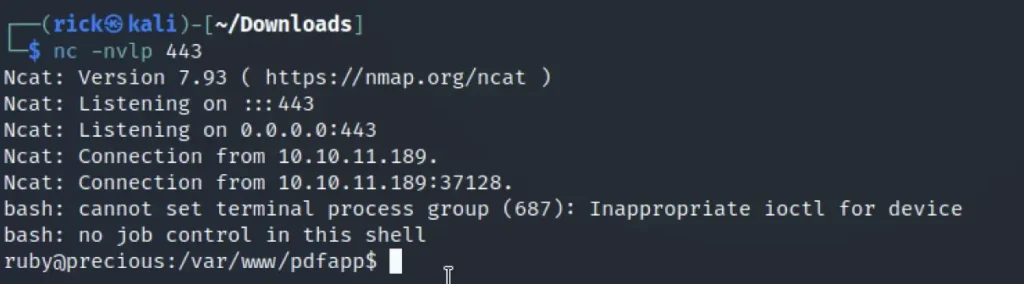
Usually to get a reverse shell access we do the below command.
nc -nlvp 4444 nc -nlvp <port no>
The reverse shell access works with netcat only when the payload is executed in the target flaw.
Conclusion
According to me, Netcat is the best tool for reverse shell access and some alternatives are pwncat.
Also Read: Armitage Tutorial
Also Read: msfvenom Full Tutorial


