Introduction
sql injection payload: In the ever-evolving landscape of cybersecurity, SQL Injection remains a prevalent and dangerous vulnerability.
It occurs when an attacker injects malicious SQL code into a website’s input fields, allowing them to manipulate the site’s database. To effectively combat this threat, it is crucial to comprehend the inner workings of SQL Injection payloads.
Advertisement
Understanding an SQL Injection Payload
SQL Injection payloads are the malicious code snippets that attackers insert into vulnerable input fields, typically found in web forms, search bars, or login pages.
These payloads exploit poor input validation, enabling attackers to gain unauthorized access to a website’s database and execute arbitrary SQL queries.
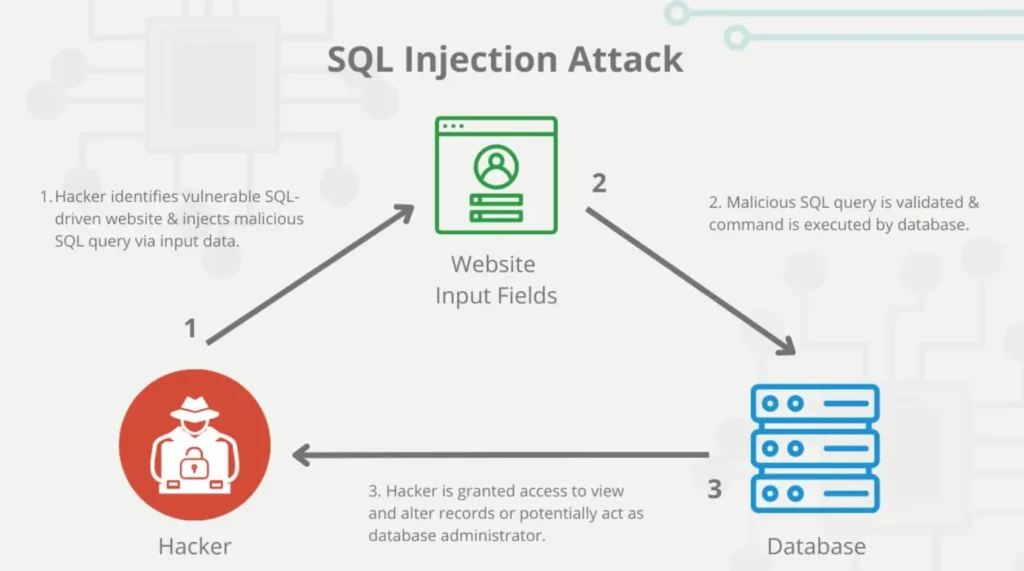
The Vulnerable Input Field
The first step in an SQL Injection attack is identifying a vulnerable input field on the target website. This field often lacks proper validation or sanitization, making it susceptible to malicious input.

Crafting the Payload
Once a vulnerable input field is identified, the attacker crafts an SQL Injection payload. This payload is a carefully constructed piece of SQL code that aims to manipulate the database. A simple example of an SQL Injection payload is as follows:
' OR '1'='1
In this payload, the attacker’s input closes the existing query and appends a condition that is always true (‘1’=’1’), effectively bypassing any authentication checks.
Advertisement
Payload Example
Consider a scenario where a website has a search bar allowing users to search for products by name. An attacker enters the following SQL Injection payload into the search bar:
' OR '1'='1'; --
In this payload, the semicolon (;) terminates the original query, and the double hyphen (--) comments out the rest of the query. As a result, the search bar’s query becomes:
SELECT * FROM products WHERE name = '' OR '1'='1'; -- '
This modified query always evaluates to true (‘1’=’1’), returning all products from the database, effectively bypassing any search functionality.
Types of SQL Injection Payloads
SQL Injection payloads come in various forms, each designed for a specific purpose. Let’s explore some common types along with examples of payloads and how they work:
Union-Based SQL Injection
Payload Example
' UNION SELECT null, username, password FROM users--

How It Works:
- The ‘ UNION SELECT null’ part is used to ensure that the injected query returns the same number of columns as the original query.
- The ‘username’ and ‘password’ fields aim to retrieve sensitive data from the ‘users’ table.
- The double hyphen (
--) is used to comment out the rest of the original query.
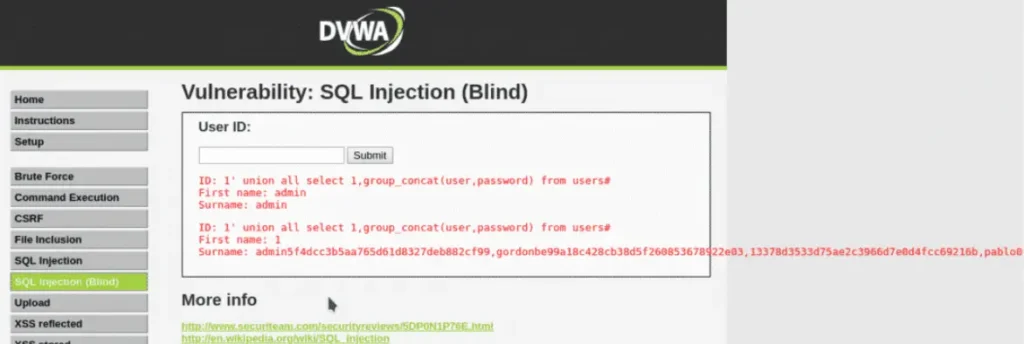
Blind SQL Injection
Payload Example
' AND 1=CONVERT(int, (SELECT TOP 1 column_name FROM information_schema.columns))--
How It Works:
- This payload checks if the condition ‘1=CONVERT(int, (SELECT TOP 1 column_name FROM information_schema.columns))’ is true.
- If true, the website’s response indicates that the injected condition holds, revealing information about the database schema.
Advertisement
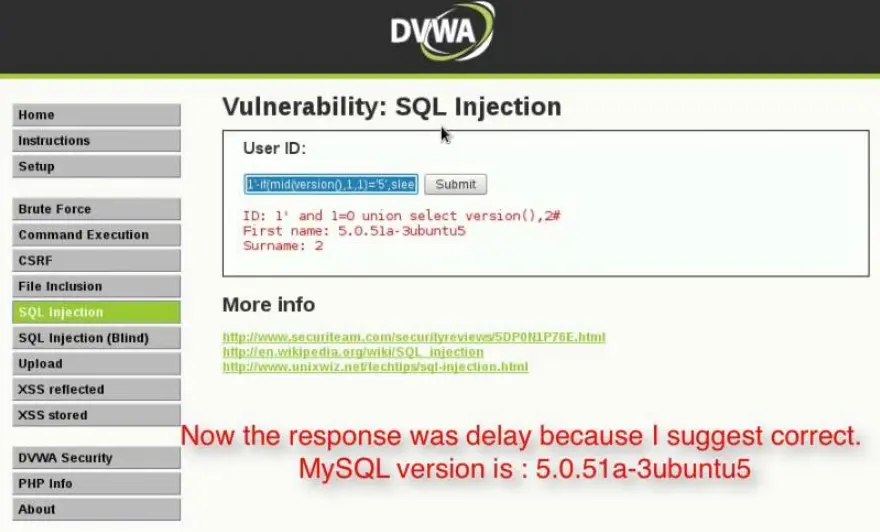
Time-Based Blind SQL Injection
Payload Example
' OR IF(1=1, SLEEP(5), 0)--
How It Works:
- This payload induces a time delay in the website’s response if the condition ‘1=1’ is true.
- By monitoring the response time, the attacker can infer whether the condition holds and gather information indirectly.
Prevention and Mitigation
Now that we’ve explored how SQL Injection payloads work, it’s essential to focus on prevention and mitigation strategies to protect your website:
Input Validation
Implement strict input validation and sanitization mechanisms. Ensure that user inputs are thoroughly checked before processing.
Parameterized Statements
Use parameterized statements in your SQL queries. Parameterized queries separate user input from SQL code, preventing SQL Injection vulnerabilities.
Web Application Firewalls (WAFs)
Consider deploying a Web Application Firewall to filter out malicious requests and protect your website from SQL Injection attacks.
Conclusion
In the digital age, safeguarding your website from SQL Injection payloads is paramount. By understanding how these exploits work and implementing robust security measures, you can significantly reduce the risk of falling victim to this pervasive threat.
Remember, cybersecurity is an ongoing process. Stay vigilant, keep your systems up-to-date, and continuously educate yourself and your team on the latest security practices to ensure your website remains secure in the face of evolving threats.
Advertisement
Read More: SQLMAP Full Tutorial




