Introduction In this post, You will learn what is DLL Hijacking and also you will learn the difference between DLL Hijacking and Dylib Hijacking. Below is the video format of the post, Check it out ???????? What is DLL...
Tag - Security
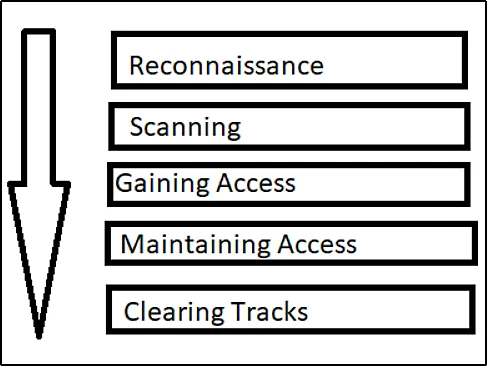
Introduction In this post, You will learn what are the 5 stages of hacking and also there will be a brief explanation of how it works. Video The 5 Stages of Hacking The 5 phases or 5 stages of...
Introduction In this post, You will learn what is cyber-attack vector and you will know the 10 most common cyber attack vectors. What is a cyber-attack vectors❓ A cyber-attack vectors is a pathway used by a hacker to...
Introduction In this post, You will learn about the top 5 brute force software and these software’s are very much powerful so, play safely. Below is the video format of the post, Check it out...
Introduction In this post, Let’s see what is brute force attack and how to do it and also I will mention some software for brute force. What is Brute Force Attack explained ???????? A Brute Force is a password...
What is CIA triad ❓ The CIA triad is a fundamental security concept. CIA Stands for Confidentiality, Integrity, Availability. Let me break down what is CIA triad is in simple words. The whole principle is to...
Introduction In this post, you will learn the 10 different types of hackers and what they do and below is the video format of the post, check it out ???????? Video Types of hackers There are 10 different types of...
Introduction In this post, you will learn the three different types of password cracking methods. And I have already written a post about password cracking tools such as john the ripper, THC hydra do check out. [Click...
Introduction In this post, you will learn the three most common ways to compromise a device and also I will share the ways to compromise OS and web applications. The three ways to compromise? I have mentioned the three...