Introduction
In this post, You will learn what is tcpdump, and also you will learn all the commands of tcpdump and below is the video format of the post, check it out.
To learn more about tcpdump [Click here]
Video
What is tcpdump ❓
Tcpdump is a packet capturing and Network analyzing tool. Which is mostly used as an alternative to Wireshark. The tool is not a GUI format, which means the tool is a command-line interface.
This tool by default uses libpcap library to capture all the packets.
The tool was initially released in the year 1988, and it was developed by four members they are Van Jacobson, Sally Floyd, Vern Paxson and Steven McCanne and the tool is written in c language.
That’s why I suggest my readers give a study to C language.
Advertisement
To learn more about tcpdump [Click here]
Tcpdump Useful Command
In tcpdump only three commands are very important and most often used and I mentioned them below;
-D: Display network
-c count: Exit after receiving count packets.
-i: interface: Listen on particular network
Tcpdump command
Below are the tcpdump full commands and tutorial and I hope you like it, If you have any doubt comment down below or watch the YouTube video I made.
List Interfaces
Interface are noting but the networks, To check the available network(Interface) Just enter this command
tcpdump -D

Default capture
To instantly capture in tcpdump, You can just enter tcpdump, and it will start to capture packets on the current network.
tcpdump

Capturing particular network
To capture packets of any particular network then we should enter the -i command.
tcpdump -i eth0
tcpdump -i <Network>
You can specify the network

Capturing specific amount of packet
Suppose if you wanted to capture only 10 packets, then you can enter the -c command.
tcpdump -i <Network> -c <packet number>
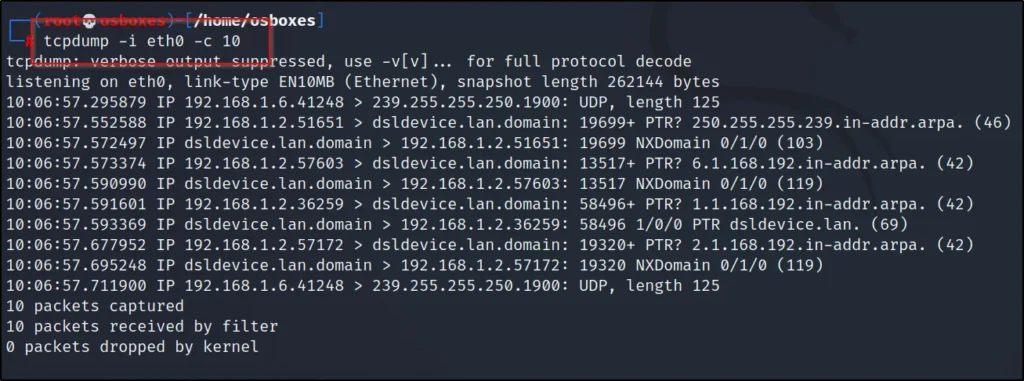
tcpdump -i eth0 -c 10
Here I am capturing 10 packets in the eth0.
Verbose mode
Almost in every tool there is a verbose and this command is very effective. The verbose mode converts the values into human-readable format.
Advertisement
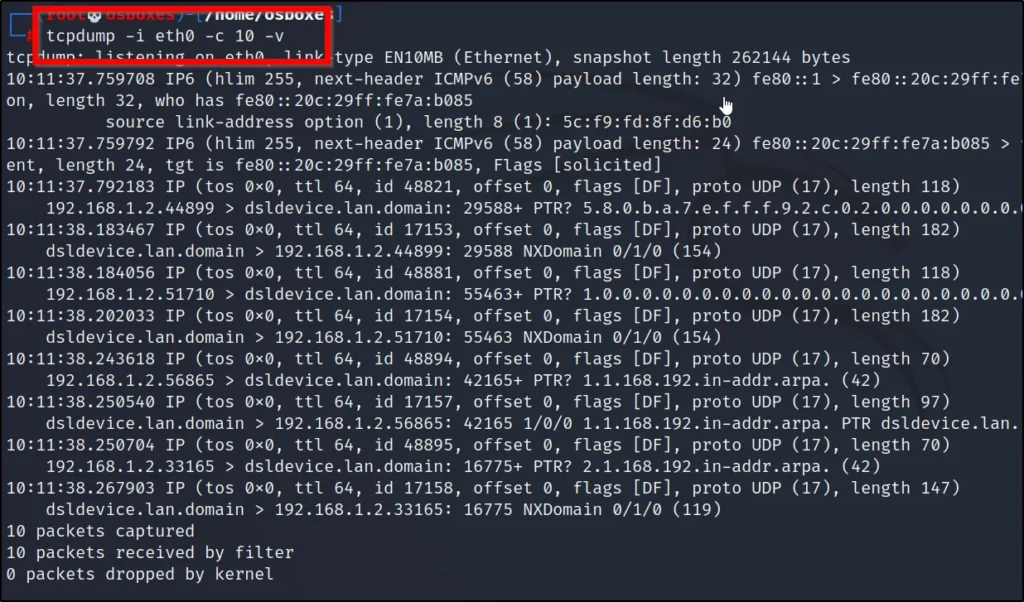
If you enter -v in tcpdump you can see where is the source IP from, and you can also see where is the destination.
tcpdump -i eth0 -c 10 -v
Printing packets in ASCII text
ASCII text in tcpdump rare very effective for e.g.: If there is an IP from Google the ASCII turn it to www.google.com
Take a look at the below pic.
tcpdump -i eth0 -c 10 -A

Not converting into domains names
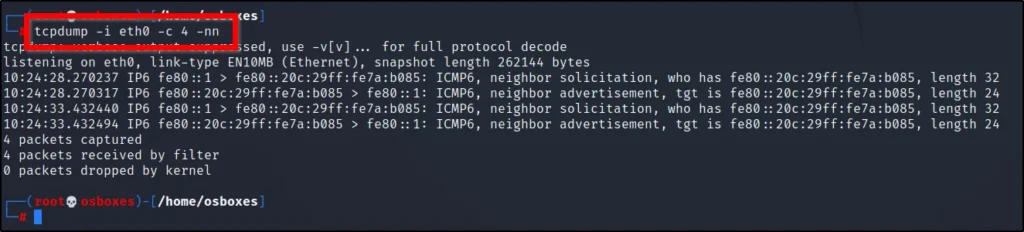
What if you don’t want to convert your IP’s to domain, then just enter -nn then you can see only IP address.
tcpdump -i eth0 -c 4 -nn
Port Filter
In port filter, let us help to capture packet from specific port.
tcpdump -i <Network> -c <Packet numbers> port <port number>
tcpdump -i eth0 -c 5 port 80

Packet filtering
Packet filtering is really great feature, but I don’t recommend doing this. In packet filtering, we can specify which packet to capture.
Advertisement
Suppose If I wanted to capture only ARP then I can mention the ARP and then we will be seeing only ARP packets captured.
tcpdump -i eth0 arp -c 5

Saving capture packet
To save the packets in a file, we use the -w command and then specify the file and the output format.
tcpdump -i eth0 -c 5 -w pcap
*The output format can be in pcap or pcappng

View the saved file
To view the save file, enter this command
tcpdump -r <Filename>
tcpdump -r file.pcap

Dump mode
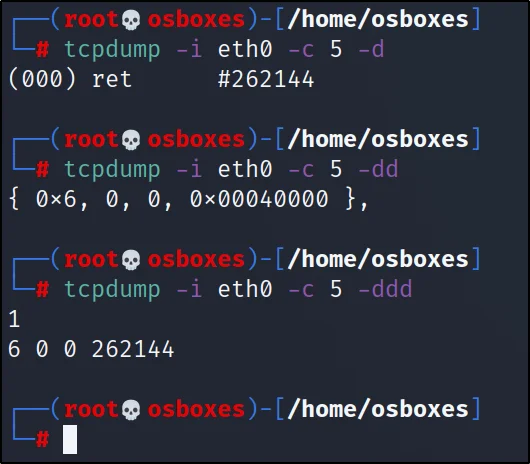
There are three levels in dump mode, they are -d, -dd, -ddd
-d: dumps the compiled matching code into a readable output.
-dd: parameter, dumps the code as a C program fragment.
-ddd: parameter and dumps code as a decimal number with a count.
tcpdump -i eth0 -c 5 -d
tcpdump -i eth0 -c 5 -dd
Finally,
tcpdump -i eth0 -c 5 -ddd
Conclusion
In my opinion, tcpdump is a great tool, but I personally don’t like CLI and prefer the Wireshark(GUI).
You can use the tcpdump for just capturing and load it to Wireshark and you can work there.
Some alternatives for tcpdump are dumpcap and even Wireshark and tshark.
Advertisement
Also Read: Wireshark Full tutorial
Also Read: Dumpcap tutorial from noob to pro




