Introduction
In this post, you will learn what is Aircrack-ng and how it works, An overview alone. In this post I am not teaching how to work with Aircrack-ng, I have written a separate post on how to work with Aircrack-ng, The post is available in the hacking tool menu.
What is Aircrack-ng?
Aircrack-ng is a powerful wireless hacking tool but still depends on other tools for gathering information. In addition, this tool is a packet sniffer. By using this tool the user can do a targeted attack only. Aircrack-ng is written in C language.
This tool can also perform as a WEP encryption key recovery. So, overall this is an awesome wireless hacking tool. Some alternative for this tool is Kismet and Airodump-ng. The kismet tool has IDS sensors in addition.
The tool was initially released in the year 2007 and got an attraction from cyber experts.
Also Read: What is Wireshark?
How Aircrack-ng works?
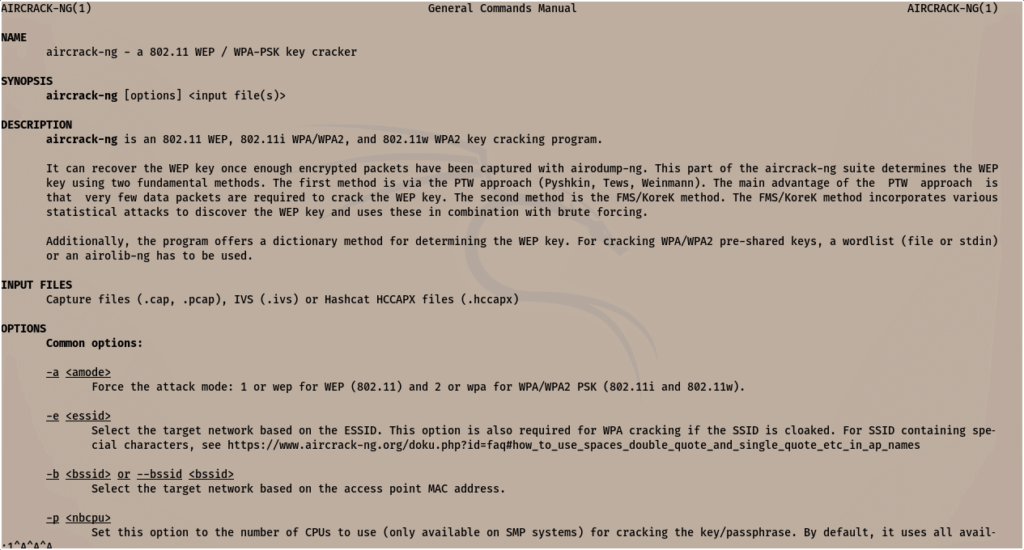
The suit includes attacks known as FMS, KoreK, PTW. The Aircrack-ng sniffs some of the network packets and finds any vulnerabilities using other tools such as Metasploit or Nikto. As I said before this tool is dependant on other tools.
Once the vulnerabilities are found the tool is ready for a wireless attack.
Specifically, the FMS attack is used against RC4 (Rivest cipher 4) encrypted keys. The KoreK attack is used against WEP-encrypted keys, Mostly public wifi will have WEP encrypted passwords.
PTW attack is used against WEP and WPA encrypted keys.
This tool can be used in many ways like doing a wireless attack, Monitoring the wifi network, Creating a fake access point and so on…
Also Read: THC Hydra, begineer’s choice
Who can use Aircrack-ng?
The tool can be used by anyone, with any type of OS(operating system). Yes, the tool supports Windows, macOS, Linux etc.,
Also Read: What is John the Ripper?
Also Read: What is Metasploit
Read: What is Nmap used for!



