Introduction
Welcome to the world of ethical hacking, where reconnaissance reigns supreme. In this blog post, we’ll delve into the vital role of reconnaissance in cybersecurity.
Get ready to uncover the tactics, significance, and ethical considerations behind this essential phase of hacking. Let’s dive in!
What is Recon ?
Reconnaissance, often abbreviated as “recon,” inSubdomain Enumerationvolves gathering all available information about the target or victim you intend to hack.
This includes details such as their location, IP address, open ports, services, subdomains, directories, and more.

In this blog post, we’ll focus specifically on web applications and discuss the methods for gathering comprehensive information about them to initiate the hacking process.
Advertisement
Subdomain Enumeration
Every domain typically hosts numerous subdomains, sometimes numbering in the thousands.
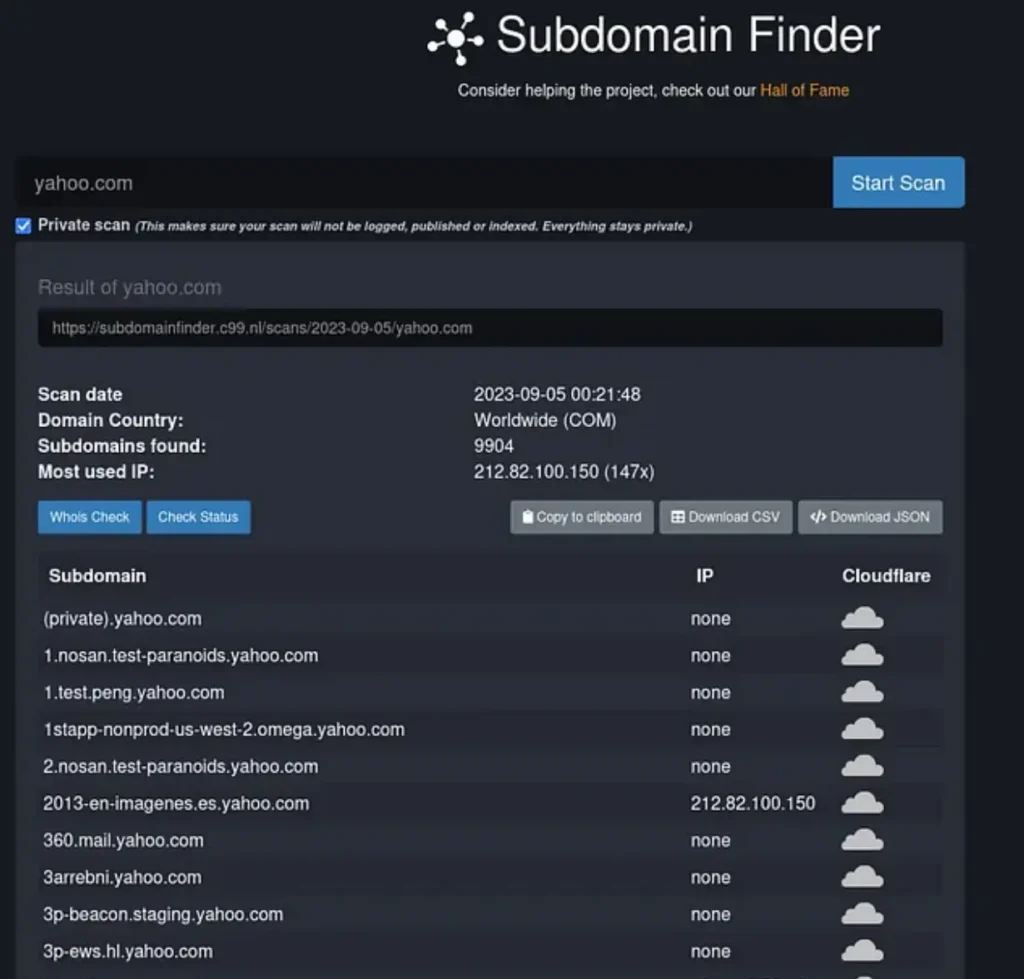
Subdomainfinder.c99.nl is a fantastic website for collecting subdomains.One highly recommended website for discovering potential subdomains associated with any domain or organization is https://securitytrails.com.
This platform is particularly effective for enumerating subdomains and is widely regarded as a valuable resource in the field.
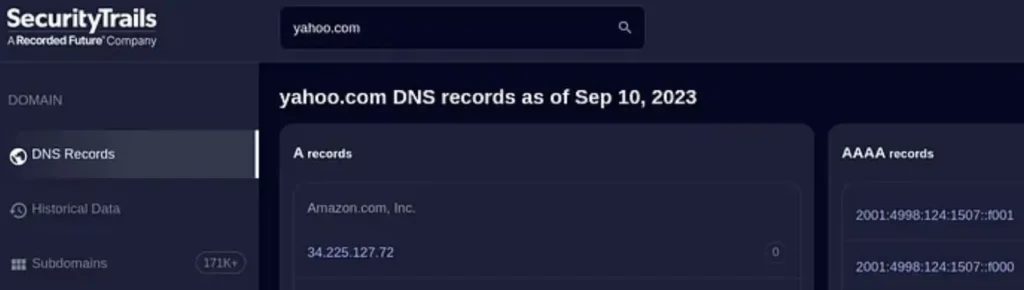
If you take a look at the image, you’ll notice there are over 171,000 subdomains listed for yahoo.com. The website also offers additional details about the domain such as records for A, AAAA, CNAME, and more.
You can utilize the SecurityTrails API to gather all subdomains through the terminal. However, it’s worth noting that this service is not free; it’s a paid service and is generally recommended for large organizations engaged in reconnaissance activities.
Subdomainfinder.c99.nl is a fantastic website for collecting subdomains.
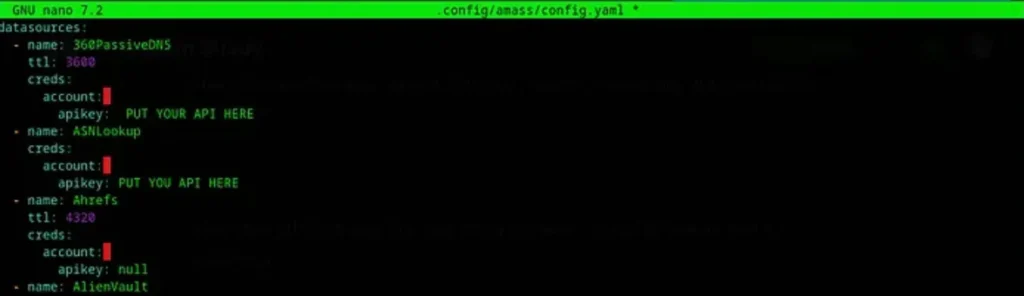
Amass, available on GitHub at https://github.com/owasp-amass/amass, is a powerful tool for gathering subdomains. To make the most of it, you’ll need to supply it with multiple API keys.
It’s recommended to invest time in gathering as many API keys as possible, even if it takes a week or more.
Once you’ve installed Amass, you can use the following command in your terminal:
nano $HOME/.config/amass/config.yaml
You can start searching for APIs such as Shodan, Censys, Cloudflare, FOFA, and many others to enhance the capabilities of Amass.
After gathering all the APIs and setting them up in Amass, you can begin using the tool by following these steps:
Compile all the domains you want to search into a file named “domains.txt” or any other preferred name.
amass enum -active -df domains.txt -config $HOME/.config/amass/config.yaml -o amass_subdoamins.txt
For large scopes, such as those for companies and Autonomous System Numbers (ASN), Amass is commonly utilized in the following manner:
amass intel -org "Tesla"
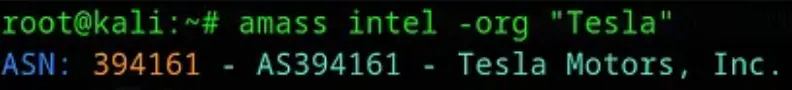
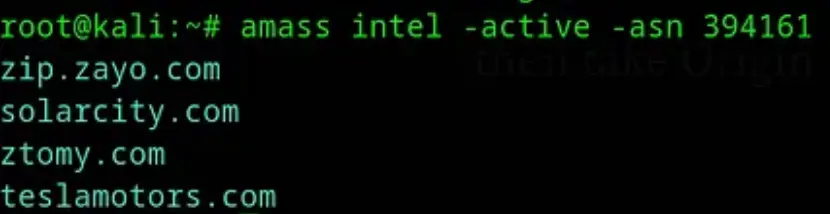
Next, obtain the Origin ASN (394161) for the Tesla company.
amass intel -active -asn 394161
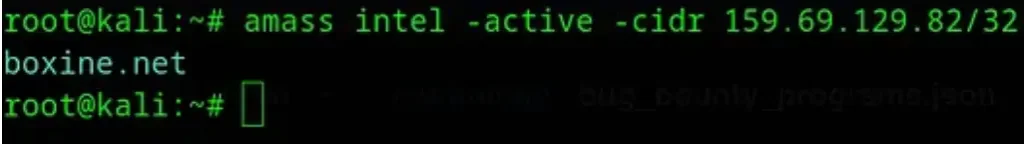
If you have the CIDR (Classless Inter-Domain Routing) notation for the company’s network and want to use Amass to find domains related to the company, you can proceed as follows:
amass intel -active -cidr 159.69.129.82/32
Also Read: Amass Full Tutorial
Assetfinder, available on GitHub at https://github.com/tomnomnom/assetfinder, is a tool designed to passively gather all subdomains.
It serves as an alternative to methods such as Google Dorks and crt.sh, offering passive subdomain enumeration capabilities.
cat domains | assetfinder -subs-only
To unlock the full power of Subfinder, one of the most potent tools for subdomain discovery, you need to provide API keys.
You can do this by navigating to the following directory: ~/.config/subfinder/provider-config.yaml, and then adding the API keys from various websites as specified.
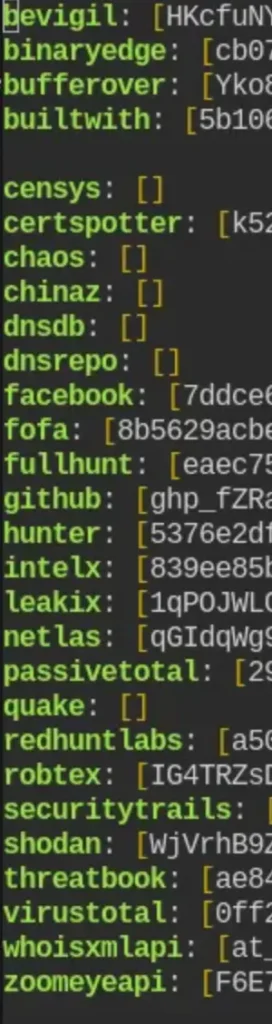
After adding the API keys to the configuration file, you can start Subfinder to begin the subdomain discovery process.
subfinder -d google.com
Also Read: Subfinder Full Tutorial
virtual host
ffuf -u 'https://example.com' -H 'Host: FUZZ.example.com' -w Seclists/Discovery/DNS/top-1million-11.txt
Alternatively, instead of specifying a domain like “example.com,” you can use its IP address. This approach is commonly used in server configurations to direct traffic to a specific website hosted on that IP address.
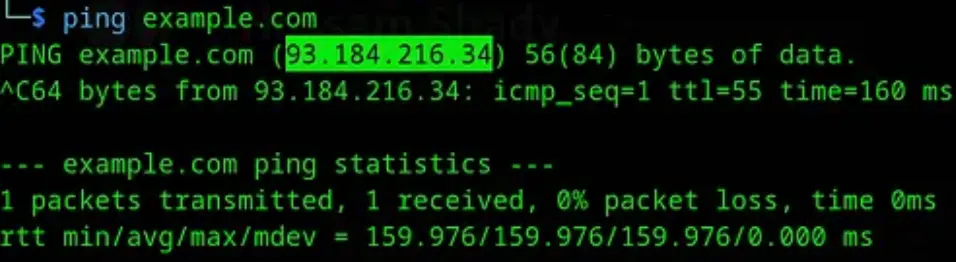
ffuf -u http://93.184.216.34 -H "Host: FUZZ.example.com" -w Seclists/Discovery/DNS/top-1million-11.txt
After executing the command mentioned above, you may notice numerous outputs with the same size, for instance, 4517. To filter these outputs based on their size, you can utilize the -fs option.
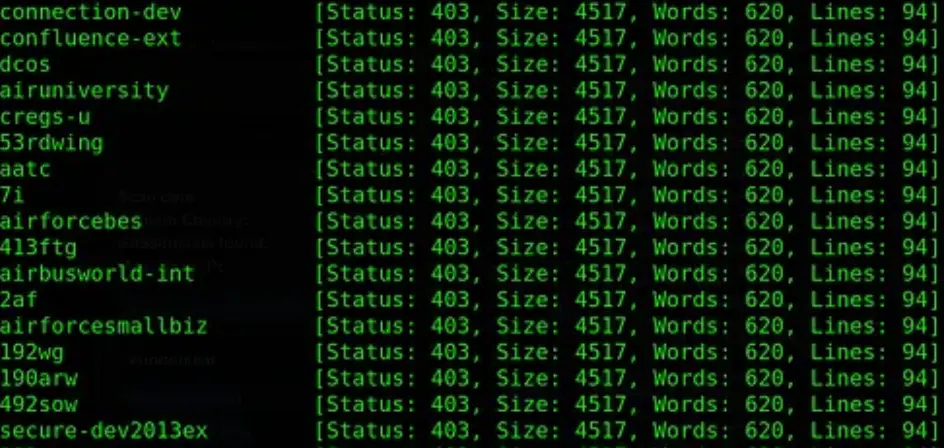
ffuf -u 'https://example.com' -H 'Host: FUZZ.example.com' -w Seclists/Discovery/DNS/top-1million-11.txt -fs 4517
After filtering the outputs based on their size, you can proceed to access the subdomains from the virtual host.
However, if this approach is not functioning as expected, it could indicate potential issues with the server configuration or the accessibility of the subdomains.
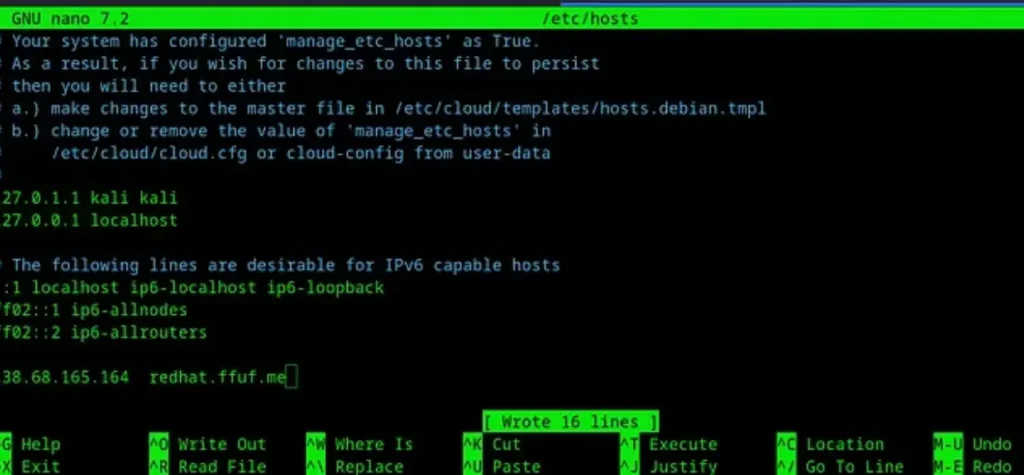
Before accessing the subdomains from the virtual host, you need to add the subdomain you found to the /etc/hosts file.
This subdomain should point to the main domain’s IP address. For example, if you found the subdomain “ffuf.me” and it indicates the same IP address as the main domain, you would add an entry like this to your /etc/hosts file:
138.68.165.164 ffuf.me
This allows your system to resolve the subdomain to the correct IP address when accessing it locally.
After adding the subdomain you found to the /etc/hosts file and indicating it to the origin domain’s IP address, save the changes.
Then, return to your browser and attempt to access the subdomain directly. You should now be able to access the subdomain successfully.

Once you’ve ensured that the page is functioning correctly and have downloaded any secret files, you can further practice by visiting http://ffuf.me and https://www.acceis.fr/ffuf-advanced-tricks/.
If you’ve collected all possible subdomains and stored them in a file named “subdomains.txt,” you can remove any duplicate entries by running the following command:
cat subdomains.txt | sort -u >> uniq_subs.txt
After removing duplicates from the “subdomains.txt” file, you can use HTTPX to identify only the live subdomains.
cat uniq_subs.txt | httpx -o httpx
After running HTTPX to identify live subdomains, it’s time to move on to Part 2 of the process.
For me, I typically rely on Security Trails, Subfinder, and Assetfinder for smaller scopes.
Part 2
Directory and File Enumeration
There are various methods available for obtaining directories and files. Dirb for directory enumeration
dirb https://example.com
Dirsearch is another tool commonly used for file enumeration.
dirsearch -u https://example.com
FFUF is a versatile tool often utilized for fuzzing files and directories.
ffuf -u https://www.example.com/FUZZ -w wordlist/Seclists/Discovery/Web-content/raft-medium-files.txt -mc 200,302,301 -t 1000
You can also consider using other tools such as Gobuster, Meg, and more for file and directory enumeration.
Part 3
Parameter fuzzing and gathering involves testing and collecting information on various parameters within a web application, such as URL parameters, form inputs, and cookies, to identify vulnerabilities and potential attack vectors.
arjun
arjun -u https://www.example.com/file.php
paramspider
paramspider -l domains.txt -s
gospider
gospider -S domains.txt -o gospider
burpsuite paraminer
After installing the extension, navigate to the request and right-click. Then, select “Extensions” followed by “Paraminer.” From there, choose “Guess params” and then “Guess everything.”
Part 4
To collect all URLs related to the target and save them in a file named “urls.txt”, you can use various methods such as web crawling, scraping, or utilizing tools like
Subdomain Enumeration and Web Application Vulnerability Scanners. Once you have gathered the URLs, simply list them in the “urls.txt” file, with each URL on a separate line. For example:
https://example.com/page1
https://example.com/page2
https://example.com/page3
…
waybackurls
cat urls.txt | waybackurls
Gau
cat urls.txt | gau
Katana
katana -list urls.txt -v -jc -o katana
hakrawler
cat urls.txt | hakrawler
Conclusion
I’ll be here whenever you’re ready to continue. Just let me know when you’re ready for the next steps, techyrick!


