Introduction
In this Post, You will learn What is Steganography and where it is used? Steganography in CTF’s
If You have any doubts, Please comment down below 👇🏾
What is Steganography?
Steganography is a method used to conceal a confidential message within another entity. For instance, one might hide a secret within an image or an audio file.
There are numerous tools available to assist in concealing a secret message within an image or other file types. One of the most renowned tools is steghide. We’ll delve deeper into this later on.
Also Read: Steghide Full Tutorial
Types of Steganography
There are two types of steganography:
(i) Physical
(ii) Digital
In this article, we’ll focus on digital steganography.

Where is steganography used?
Government agencies like the SVR utilize steganography for certain communications.
Malicious hackers employ steganography for various types of attacks. Some of the most notable methods include embedding actual scripts within macro-enabled Word documents, songs, or movies.
For further information, you can refer to this article: What is Steganography? A Complete Guide to the Ancient Art of Concealing Messages
How to Hide a text file to an Image
To install steghide, if you’re using Kali Linux, you can use the command:
sudo apt install steghide
After installing steghide, you can use the following command syntax to embed a file into another file:
steghide embed -ef <file to be embedded> -cf <file to embed into>
Replace <file to be embedded> with the name of the file you want to hide, and <file to embed into> with the name of the file you want to embed into.
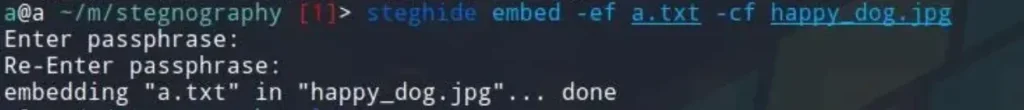
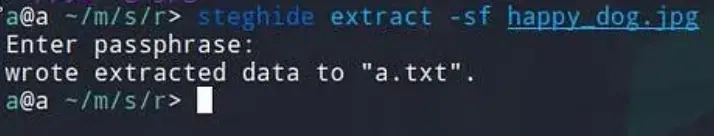
Now, to extract our data, we’ll use the following command:
steghide extract -sf <file with hidden data> -xf <output filename>
Replace <file with hidden data> with the name of the file containing the hidden data, and <output filename> with the name you want to give to the extracted file.
Time to do Some CTF
CTF Hackerman Challenge: https://app.hackthebox.com/challenges/17
Here’s my method for approaching steganography challenges in any CTF:
Steps:
Download the challenge file.
Upon downloading the file, I always run ExifTool against it. (In CTF, you can find passphrases or other useful information.)
Next, I utilize the strings command to print sequences of printable characters in the files. Following that, I explore other tools such as steghide and foremost.
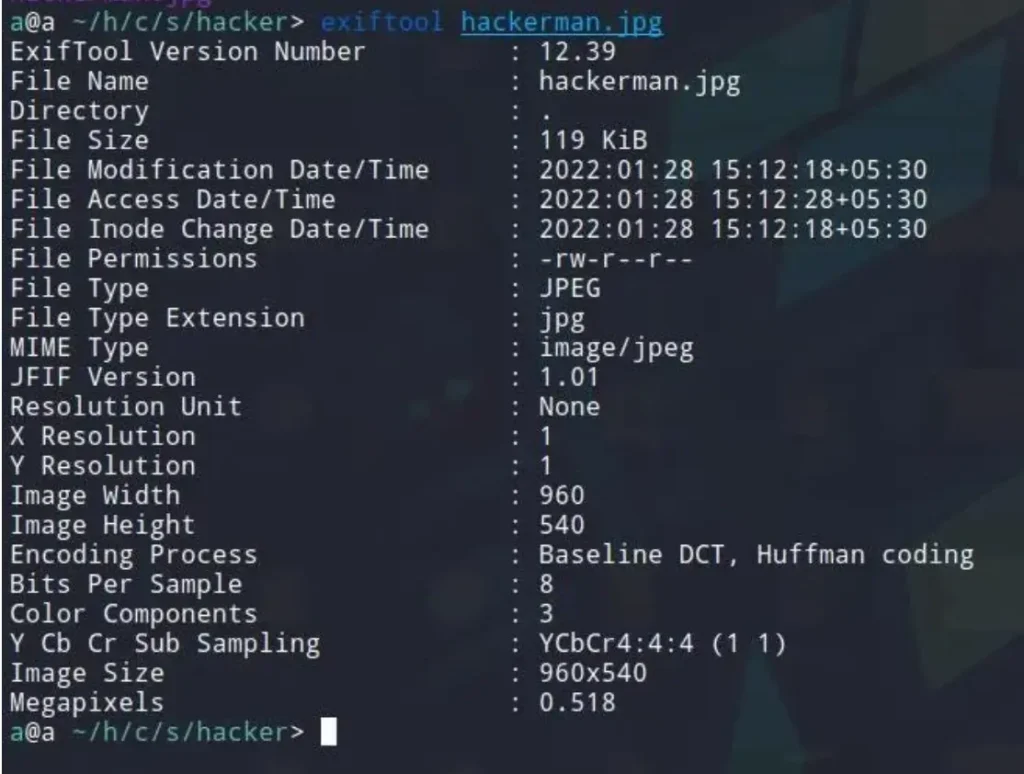
Verifying EXIF data.
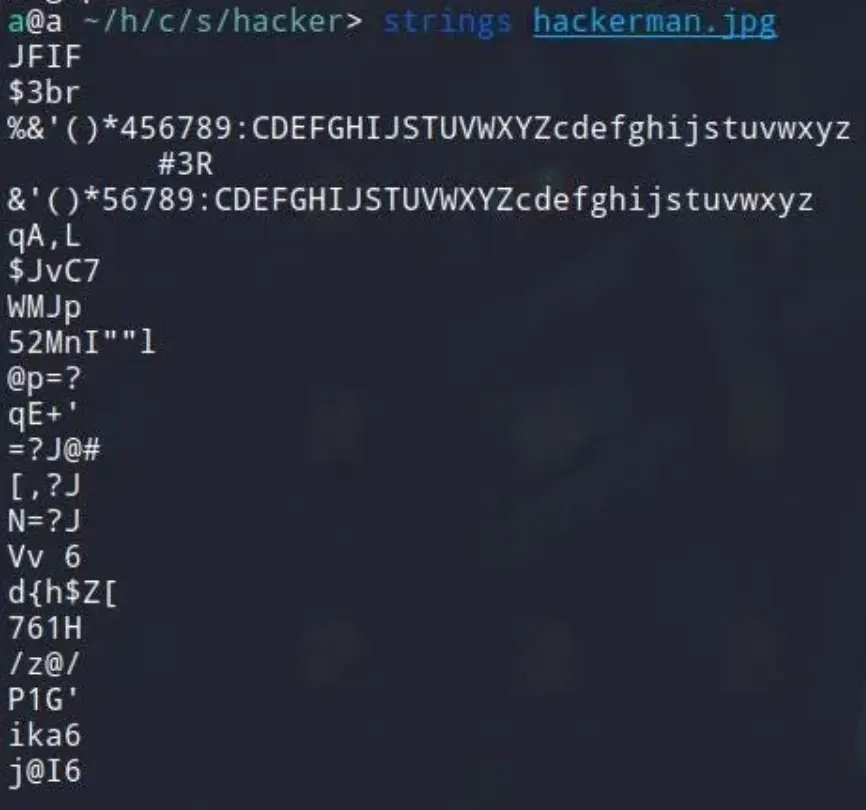
Examining strings.
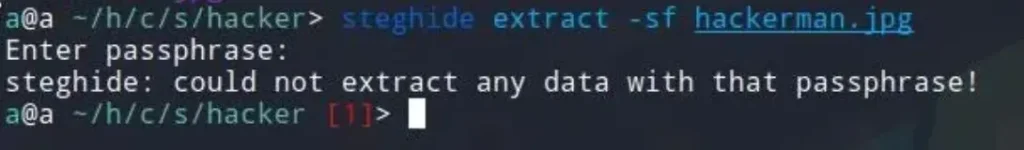
As I didn’t know the passphrase, I attempted to brute force it using stegcracker.
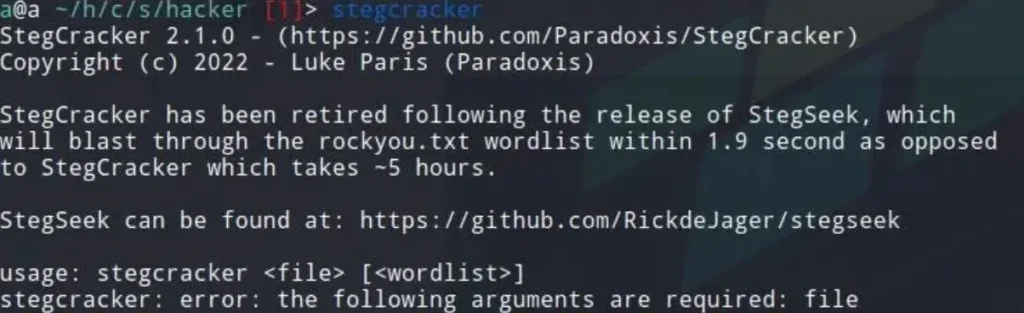
Stegcracker
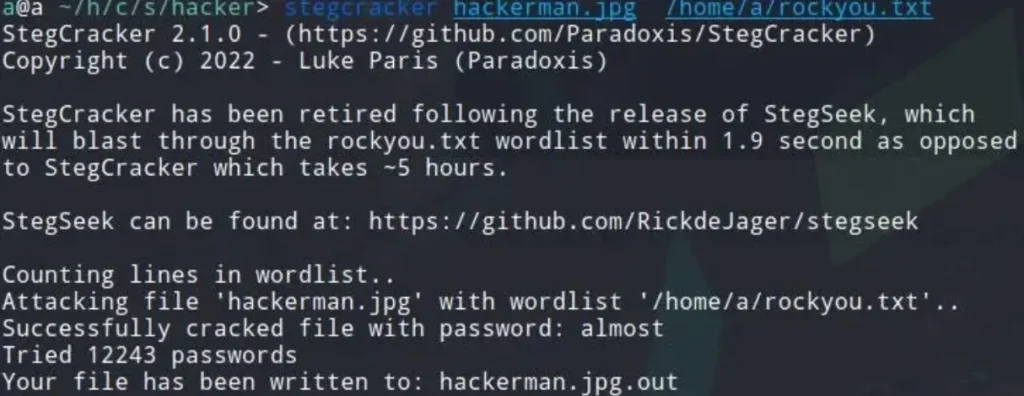
Password cracked.
We now have the passphrase “almost.” We can proceed to extract the hidden file using steghide.
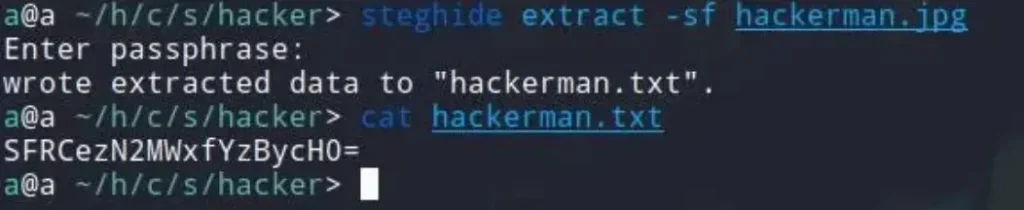
Our final output is base64 encoded. We can easily decode it by using base64 decoding.
Frequently Asked Questions (FAQ) on Steganography
- What is steganography?
- Steganography is the practice of concealing a secret message within another medium, such as an image, audio file, or text, without attracting attention to the existence of the hidden message.
- How does steganography differ from cryptography?
- While cryptography focuses on making a message unreadable to anyone except those with the decryption key, steganography hides the existence of the message itself.
- What are some common techniques used in steganography?
- Common techniques include LSB (Least Significant Bit) hiding, hiding messages within image or audio file metadata, and using invisible ink or microdots on physical documents.
- Why is steganography used?
- Steganography is used for covert communication, data hiding, copyright protection, and digital watermarking. It can also be employed for security purposes in data transmission.
- How can one detect steganography?
- Detecting steganography often requires specialized tools or forensic analysis. Suspicious file characteristics, unusual file sizes, or discrepancies in metadata may indicate the presence of hidden data.
- Is steganography legal?
- Steganography itself is legal in most jurisdictions. However, its use for illegal activities, such as hiding malware or illicit communications, is subject to legal repercussions.
- Can steganography be detected by antivirus software?
- While some antivirus software may detect known steganographic techniques or patterns associated with malicious usage, it is not foolproof. Advanced steganographic methods can evade detection by antivirus software.
- What are some real-world applications of steganography?
- Real-world applications include covert communication by intelligence agencies, embedding copyright information in digital media, and hiding messages in social media posts for privacy or security reasons.
- How secure is steganography?
- The security of steganography depends on various factors, such as the complexity of the hiding technique, the size of the hidden message, and the skill of the attacker. While steganography can offer a level of security, it is not invulnerable to detection or decryption.
- Can steganography be used for digital forensics?
- Yes, steganography can be used in digital forensics to analyze and uncover hidden information in files. Forensic analysts may employ specialized tools and techniques to detect and extract hidden data for investigative purposes.


