Introduction In this post, you will learn what is SQL injection and in addition, I will explain how website hacking became more popular and at last you will learn if the SQL based languages are really...
Tag - Security
Introduction In this post, you will learn what is Hiren’s boot cd and also we are going to see the Linux live cd? How the live CDs are effective in compromising and I have already written a blog post on what is Kon boot...
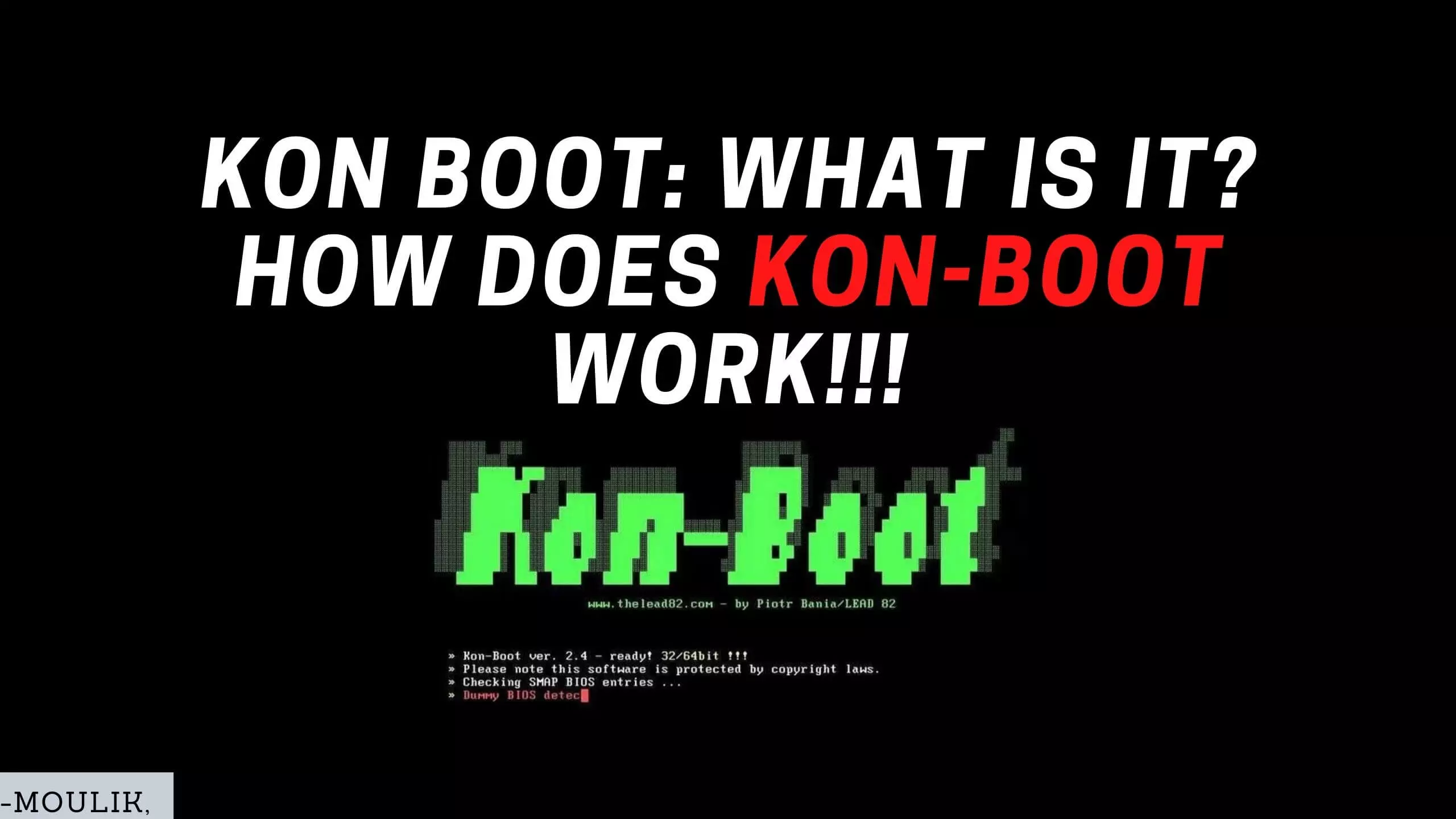
Introduction In this post, you will learn what is kon-boot and how does it work and Kon-book is mostly used for compromising or recovery of passwords. This post is just an overview of what is tool is and I am not performing...
Introduction In this post, you will learn what is IoT device and how it works exactly and how does IoT is involved in cyberattacks. And I will also relate how the IoT is involved with the cyberattack with an example. What...
Introduction In this post, you will learn what is internal and external reconnaissance and an example from both the reconnaissance. You will also learn how the process works. What is Reconnaissance? Like many words in IT...
Introduction In this post, you will learn what is baiting and what the hell is it doing in IT. This post is all about baiting’s and I have already written a post on what is social engineering do check it out click here...
Introduction In this post, you will learn what is water holing and how it works and water is a type of social engineering attack. I have already written a post on what is social engineering and its most common type. To read...
Introduction Diversion theft: In this post, you will learn what is diversion thefts and how it works exactly. Diversion thefts is a type of social engineering attack. And I have already written a post on what is social...
Introduction In this post, you will learn what is pretexting and how pretextings works exactly and also we will see an example of pretexting. Pretextings is a social engineering attack. If you don’t know what is social...