Introduction
In this post, you will learn what is cryptographic key and 12 types of cryptographic key. If you already knew something about cryptographic key, please leave a comment below.
What is a cryptographic key?
The cryptographic key is a string of data used while encrypting and decrypting. While Encrypting data, users use this key to encrypt their data when transferring the data on public internet. When the data is encrypted, it means the plain text of data become cipher text. Which looks something like this.
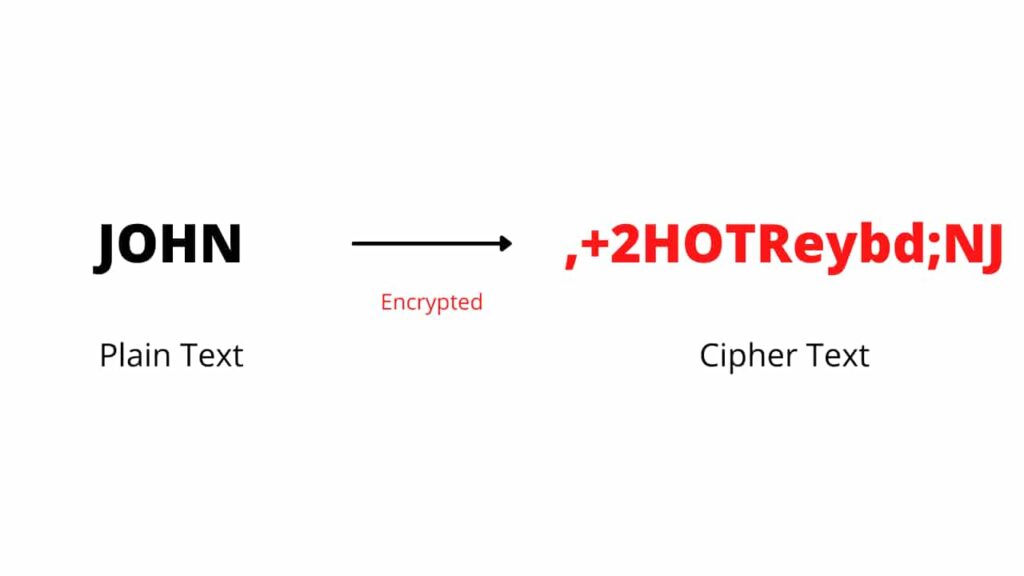
Users use encryption so, no middle man see your data. Even while at decryption, users uses a cryptographic key to decrypt the string of code and can read the data in plain text.
Also Read: What is Encryption and decryption? How it works
Symmetric vs Asymmetric key
Before seeing the types of cryptographic key, let’s see a small recap of Symmetric and Asymmetric key;
Symmetric key – Symmetric key use same string value for encryption and decryption. Which means symmetric key uses same keys for encrypting and decrypting data.
Asymmetric key – Asymmetric key use different string value for encryption and decryption. Which means Asymmetric key uses different keys for encrypting and decrypting a data.
Also Read: How forget password mechanism works?
Types of cryptographic key
There are 12 common types of cryptographic key in the of key management;
- Authorization key
- Master key
- Transient key
- Ephemeral key
- Key agreement key
- Transport key
- Wrapping key
- Authentication key
- Signature key
- Private key
- Public key
- Asymmetric key
12 Types of Cryptographic keys – Explained
Authorization key – A private or public Asymmetric key pair. A private Authorization key provides privilege to the entity. Whereas public Authorization key verifies that the key is successfully decrypted.
Master Key – It is a symmetric master key which generates other symmetric keys using symmetric cryptographic method.
Transient Key – A Asymmetric public or private key pair. Which is used only once.
Ephemeral Key – A public or private Asymmetric key pair which is used only once and to establishing other keys.
Key Agreement key – A public or private Asymmetric which is used to exchange for other keys, and the other term for exchanging keys, is key agreement key.
Transport key – A public or private Asymmetric key which encrypts the message which contains other keys. Transport key also a type of wrapping key.
Wrapping Key – It is a symmetric key which encrypts the message which contains symmetric keys.
Authentication key – A public or private Asymmetric key which verifies identity, communication and stored data.
Signature key – A public or private Asymmetric key pair which generates a digital signature for verifying the identity.
Private key – A public or private Asymmetric key, Alternatively be a symmetric public or private pair of keys. In symmetric, the same keys are used for encryption and decryption. In Asymmetric, the key remains private.
Public key – A public key is an Asymmetric key with public algorithm and verified identity, such as stored data publicly.
Asymmetric key – A public or private key pair encrypted publicly therefore need private key to decrypt.
Also Read: What is a computer worm? How does it work
Also Read: What is Computer virus and how a Virus works in computer
Read: What is a Trojan horse?
Read: What is Spyware, how does a spyware work?
Source: Wikipedia
Source: Cryptographic keys