Table of ContentsIntroductionVideoLet's start ????Your First Bash ScriptScanner using ScriptConclusion Introduction In the previous post, You must have learned about some of the basic commands related to process...
Tag - Linux
Table of ContentsIntroductionVideoLet's start ????Your First Bash ScriptScanner using ScriptConclusion Introduction In the previous post, You must have learned about some of the basic commands related to permissions...
Table of ContentsIntroductionVideoLet's start ????Your First Bash ScriptScanner using ScriptConclusion Introduction In this post, You will learn how to control file and directory permissions in kali linux. If you have...
Table of ContentsIntroductionVideoLet's start ????Your First Bash ScriptScanner using ScriptConclusion Introduction In this post, Let’s see how to add and remove software in Linux. This is going to be really...
Table of ContentsIntroductionVideoLet's start ????Your First Bash ScriptScanner using ScriptConclusion Introduction ???????? In this post, you will learn some basic network analysing and managing commands. If you have...
Table of ContentsIntroductionVideoLet's start ????Your First Bash ScriptScanner using ScriptConclusion Introduction???????? In this post, You will learn some of the important Linux commands. Hope you have seen the...
Table of ContentsIntroductionVideoLet's start ????Your First Bash ScriptScanner using ScriptConclusion Introduction In this post, You will learn basic Linux commands. You can start your hacking journey from...
Table of ContentsIntroductionVideoLet's start ????Your First Bash ScriptScanner using ScriptConclusion Introduction In this post, You will learn basic Linux commands. You can start your hacking journey from here...
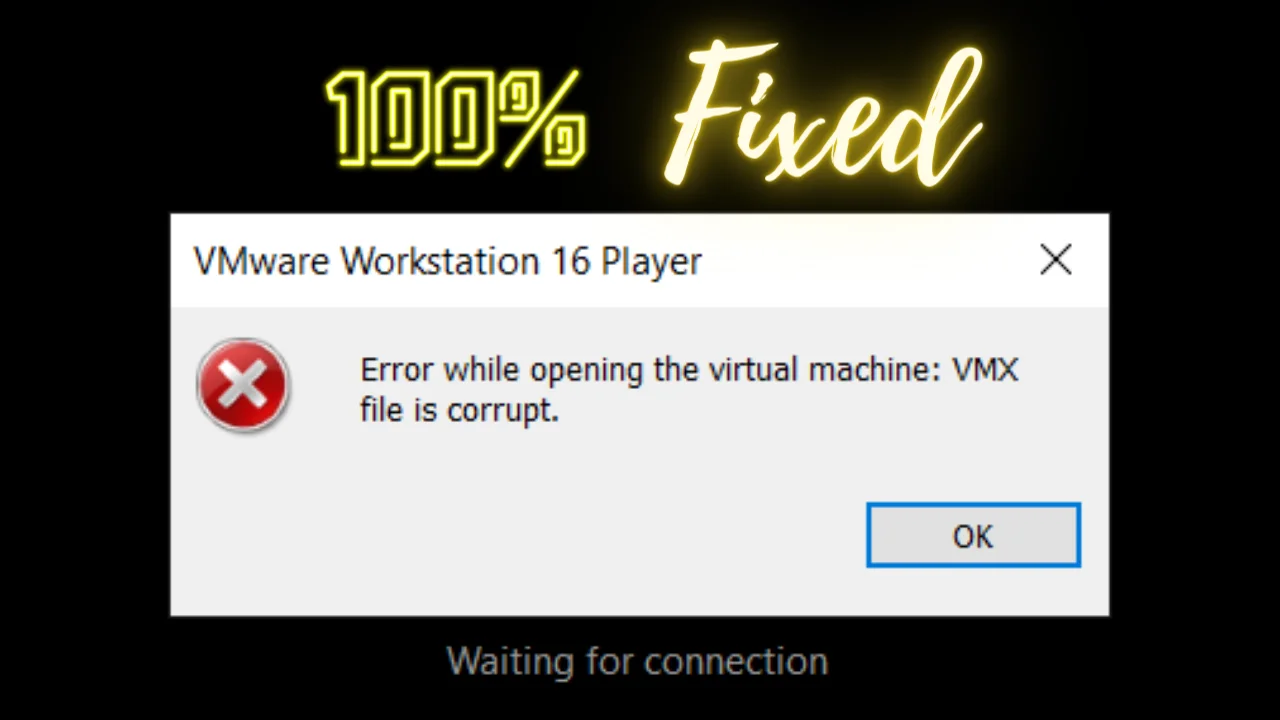
Introduction In this post, we will see a VMware error occurring while opening any vmdk file. By end of this post, you will be able to solve this error, Error while opening the virtual machine: VMX file is corrupt. Video:...